* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download The Advanced Penetration Testing Boot Camp
Cloud computing issues wikipedia , lookup
Information security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Distributed firewall wikipedia , lookup
Unix security wikipedia , lookup
Mobile device forensics wikipedia , lookup
Security-focused operating system wikipedia , lookup
Data remanence wikipedia , lookup
Information privacy law wikipedia , lookup
Mobile security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Computer security wikipedia , lookup
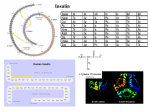
Emerging Threats in the Healthcare IT Ecosystem Ralph Echemendia HealthTech - Advisory Solutions Ralph Echemendia Advisory Solutions About me • Over 20years experience as Information security expert, researcher, ethical hacker, forensics/expert witness and instructor in many IT areas. • Specializing in Security of Virtualized Architectures • Featured in many articles and reports in main media outlets • As a consultant conducted security audits, technical education and penetration tests for many Fortune 1000 companies including: • • • • Oracle Microsoft Google and American Express Universal Picture and Summit Entertainment • Government institutions such as: • • • • United Nations NASA FBI DOD and GSA to name a few. Overview • History of Cyber-Threats • Information Vulnerabilities • Data Breaches • Medical Cybercrime: The Next Frontier • The Cloud • The Future Source : http://jeremiahgrossman.blogspot.com/ History of Cyber-Threats Information Vulnerabilities • Information security vulnerabilities are weaknesses that expose an organization to risk. • Understanding your vulnerabilities is the first step to managing risk. Data Leaks • Unprotected or Unsafe Data Data leakage filled the headlines in 2008 as corporations and government proved themselves to be lax in protecting their confidential data. • Organizations of all sizes are finding that today’s mobile and collaborative workforce needs access to information inside and outside the office, along with the ability to share data with co-workers and partners. • Users are routinely using and sharing data without giving thought to confidentiality and regulatory requirements. • Almost 30 percent of organizations store contract, financial data, patient information, contact details and personal account data on removable or mobile media. Data Leaks are everywhere! Used hardware? • Incidents were reported of confidential data ending up in the public domain after old computer hardware, which had not been securely erased, was sold on auction sites like eBay. • Analysts suggest that there is a higher demand (and thus higher price offered) for used hard drives on eBay than for brand new ones. • Imagine the amount of confidential information that is potentially recoverable. Data Leaks cost MONEY???? •The average organizational cost of a data security breach in the U.S. dropped 24 percent to $5.5 million in 2011 from $7.2 million in 2010, according to the latest report from the Ponemon Institute. •Based on the data breach experiences of 49 companies from 14 industries, including healthcare, the average cost per record also dropped from $214 to $194. This was the first time in the seven years for which the Ponemon Institute has done this survey that this cost declined. That’s great news no? Data Leaks cost MONEY???? NOT TRUE FOR HEALTHCARE • The healthcare industry is apparently lagging behind other industries in this regard. • In an earlier report, Ponemon found that health data breaches increased 32 percent from 2010 to 2011 and that the average cost per organization grew 10 percent last year. - Average per-capita cost of $240 per record. • A recent Redspin report on the state of health IT security found that the total number of health records breaches are up. Report says they increased 97 percent from 2010 to 2011. Largest Healthcare Data Breaches http://www.datalossdb.org/ Data Leaks on Google? Medical Cybercrime: The Next frontier Eastern European gangs stealing computer files with Americans' health insurance information for resale? In late July, an interesting story came out of Chicago's suburbs: Hackers broke into a small medical practice's server, encrypted patients' electronic medical records (EMRs) and emails, and demanded a ransom. Instead of paying the ransom, the Surgeons of Lake County turned the server off and called police. It is not known whether the hackers who targeted the Surgeons of Lake County also extorted other businesses--but federal-mandated HIPAA records indicate 37 hospitals and doctors' offices nationwide have been hacked since 2009, resulting in the theft or damage of patients' medical records. Source: Sophos Medical Cybercrime: The Next frontier Remotely hacking insulin pumps to kill patients? • A much more worrying--and dangerous--form of medical hacking is creating counterfeit medical devices or hacking existing ones. Counterfeit medical devices are a huge problem; according to the World Health Organization. • 8% of medical devices worldwide were counterfeit as of 2010. • Although the counterfeit insulin pumps, condoms, contact lenses, and surgical equipment are mainly found abroad, many find their way Stateside due to insecure supply chains. Source: Sophos Medical Cybercrime: The Next frontier Remotely hacking insulin pumps to kill patients? • At the 2011 Defcon in Las Vegas security expert and diabetic Jay Radcliffe demonstrated how he discovered critical security lapses in Medtronic insulin pumps that could let hackers remotely kill patients by manipulating the amount of insulin pumped. • Radcliffe successfully hacked his own insulin pump and discovered massive loopholes that can be used cybercriminals. • By manipulating insulin pumps remotely, criminals could kill or seriously injure targets; their crime, meanwhile, would be likely to escape detection from law enforcement unaware insulin pumps could be hacked. Source: Sophos Medical Cybercrime: The Next frontier Remotely hacking insulin pumps to kill patients? • Two members of Congress have asked the Government Accountability Office (GAO) to review the Federal Communications Commission's approach to medical devices with wireless capabilities to ensure that the devices are "safe, reliable, and secure.” • Medical devices use poorly developed code that often leads to deaths, injuries, or security lapses. There is no cross-medical industry protocol for coding QA and testing; as a result, software holes often aren't discovered until equipment fails in the field. Source: Sophos Medical Cybercrime: The Next frontier Remotely hacking implantable cardioverter-defibrillators to kill patients? • At the BreakPoint security conference in Melbourne Barnaby Jack demonstrated that he could reverse engineer a pacemaker to deliver fatal shocks from within 30 feet and rewrite the devices onboard software (firmware). • The pacemaker also contained a “secret function” that could activate other cardiac devices within a 30 foot-plus vicinity. • “The worst case scenario that I can think of, which is 100 percent possible with these devices, would be to load a compromised firmware update onto a programmer and … the compromised programmer would then infect the next pacemaker or ICD [implantable cardioverter-defibrillators] and then each would subsequently infect all others in range.” Source: Sophos Cloud Computing • A Brief Intro to IaaS • What should your provider offer? • What are the Future Challenges, Risks and New Issues to deal with? Cloud Drivers • Provider offers a wide range of Managed Infrastructure Services • Fast to Deploy, Scale up, Scale Down or Decommission • Clients demands Latest Technology (refreshed!) and Capabilities • Collective Intelligence of Professional Services Group, Vendors and MSSP services is considerable • Integrated Approach “should” save clients time, effort and costs • Compliance Mandates and Risk Mitigation Techniques should map directly to Provider Capabilities • Risk and Compliance Management Capabilities are very advanced due to “Rising Tide” effect Iaas typical security that is “Built-In” • • • • • • • • • • • • • Administrator Authentication: Password or optional Two Factor Authentication to access Enterprise Cloud Portal SSL Certificates and HTTPS encrypted sessions Dedicated IP Addresses, Public and Private Support of NAT to RFC1918 IP Address space Support of Customer Provided IP Ranges Storage location is only accessible by customer host environment Individual Firewall Contexts/Rules managed and Accessed by Client Only Load Balancer Context is customer managed Private VLANS segregate customer networks Virtual Machines are managed only by customer, service provider has no ability to manage a client server unless specifically invited and credentials shared. Dedicated Resources: Do not allow clients traffic/cpu/memory utilization peaks to affect other client’s environments. Ability to support any host based, network based, inline or span port security technology that the customer requires to be installed into their cloud environment. Support of IPSEC VPN’s Distinct Firewall context Cisco FW Modules in HA Private Rulesets Customer managed Distinct LB context Netscaler in HA Customer managed Portal Secured with SSL Certificate User authentication Single or multifactor NAT for inbound and Outbound traffic Private VLANs Vmware vSwitch DMZ and Internal Network By default, more upon r request Virtual Machines with own OS instances managed By customers Dedicated Resources Customer can oversubscribe within His/her own environment but does not Affect other customers Remote admin Only via VPN Dedicated IP addresses Private and Public Storage only accessible Via customer Host Optional security that is “Bolted-On” • • • • • • • • • • • • • • • • • Managed Firewall Managed Intrusion Detection/Prevention Managed Log Aggregation and Correlation Managed Security Event and Incident Management Network Traffic Session (Netflow) Monitoring and Analysis Full-packet capture and attack replay Memory, Disk and Network Forensics Data Leak Detection/Prevention End User Metrics, Analytics and Root Cause Analysis Content Filtering Anti-DDoS Application Firewalls Network Access Control 2 Factor Authentication Database Access Monitoring File Integrity Management And: Client Provided Security! IPS, DLP, AV, Application Whitelisting, Content Filtering Anti-DDoS , DNS-SEC, Massive Scalability and Peering, CDN NIST Continuous Compliance, NAC, Customer/DHS Mandated Equipment Support for Virtual Appliances Citrix VPX, Coradiant, and others Vulnerability Scanning, DB Access Monitoring Citrix Application Firewall, SSL Acceleration, Auto Reacting Load Balancers, SLA Enforcement Network Taps for Network Full Packet Capture, NetFlow, End User Analytics Inter-VM Monitoring SAML, PEB/CAC,SSO, 2FA, Role Based Access Crypto Customer provided, MTIPS Bandwidth Log Aggregation and SEIM, File Integrity Static and Dynamic Code Testing Archival is Encrypted Intel: Trusted Execution Technology Memory: Capture for Forensics, Malware Analysis, Anti- APT Proserve Efforts Storage: DOD Wipes, Data Spillage Procedures, Forensic Capture Challenges • Lots of Moving Parts: SLA & Root Cause Analysis • Forensics: Network, Disk, Memory • New Issues to Deal with • Mindset Change: From Point in time to Continuous Compliance and Performance Assurance… New Issues to Deal with: • Old considerations for security and compliance • Some new considerations for security and compliance • Where is your Data? • Each server is now a file • Additional considerations for Incident Response • Additional considerations for Forensics • Storage systems much larger • Additional considerations for Law Enforcement • New Attack Vectors: Same as any outsourced datacenter or hosting provider plus.. Guest to Guest, Guest to Host/VMM/HW, Guest to Self, External to Host/VMM/HW, External to Guest, Host/VMM to All, Hardware to VM’s New Threats In addition to the “normal” information security threats, we are increasingly focused on emergent threat trends •Medical device hacks •Advanced Persistent Threats •Application Layer Attacks •Cloud Bursting The Future The Future • Continuous Compliance • Total Application Performance Assurance • Somebody is going to get popped… the question is how fast can the response be? “Intrusion Resilience” • Updated: NIST and Federal Standards for Cloud Security • Growth and increased adoption The Future • Growth in attack vectors • Growth in complexity of attacks • Increase of state-sponsored cybrecrimes • Increase in arrests • Increase in InfoSec budgets • Increase in InfoSec education • Increase in IT Security personnel Thank You