FME Format Parameters
... the mesh will be set to FME’s default appearance. Any raster referenced as a texture in the 3ds file will be read by FME, as long as the source format is supported by FME. If the feature being written does not contain a valid appearance reference, the default material will be assigned to the corresp ...
... the mesh will be set to FME’s default appearance. Any raster referenced as a texture in the 3ds file will be read by FME, as long as the source format is supported by FME. If the feature being written does not contain a valid appearance reference, the default material will be assigned to the corresp ...
XML and Web Services support in SQL Server 2005
... xml.modify - modifies an instance These methods can return XML data type (query) or SQL Scalar (exist, value) ...
... xml.modify - modifies an instance These methods can return XML data type (query) or SQL Scalar (exist, value) ...
Chapter 02: The Need for Security
... propagate and attack. The code attaches itself to the existing program and takes control of that program’s access to the targeted computer. The virus-controlled target program then carries out the virus’s plan, by replicating itself into additional targeted systems. A worm is a malicious program tha ...
... propagate and attack. The code attaches itself to the existing program and takes control of that program’s access to the targeted computer. The virus-controlled target program then carries out the virus’s plan, by replicating itself into additional targeted systems. A worm is a malicious program tha ...
EMC XTREMCACHE ACCELERATES VIRTUALIZED ORACLE g
... publication date. The information is subject to change without notice. The information in this publication is provided “as is.” EMC Corporation makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of mer ...
... publication date. The information is subject to change without notice. The information in this publication is provided “as is.” EMC Corporation makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of mer ...
Beginners Guide to EDI X12 (including HIPAA)
... These are segment identifiers. Based on those we can have basic idea what data is contained in the segment. ...
... These are segment identifiers. Based on those we can have basic idea what data is contained in the segment. ...
XML and DB2
... Data management functionalities (integrity, security, recoverability and management). User has the option to store the entire document as an column or decomposed into multiple tables and columns. Users can retrieve the entire document or extract XML elements and attributes dynamically in an SQ ...
... Data management functionalities (integrity, security, recoverability and management). User has the option to store the entire document as an column or decomposed into multiple tables and columns. Users can retrieve the entire document or extract XML elements and attributes dynamically in an SQ ...
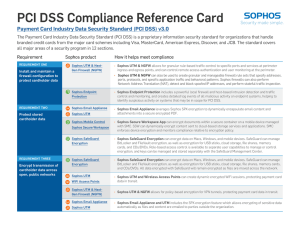
PCI DSS Compliance Reference Card
... ÌÌ Sophos UTM & NGFW includes robust intrusion detection and intrusion prevention policies that can be applied to all traffic coming into the platform. ...
... ÌÌ Sophos UTM & NGFW includes robust intrusion detection and intrusion prevention policies that can be applied to all traffic coming into the platform. ...
XML and Databases
... collection of data. In many ways, this makes it no different from any other file -- after all, all files contain data of some sort. As a "database" format, XML has some advantages. For example, it is self-describing (the markup describes the structure and type names of the data, although not the sem ...
... collection of data. In many ways, this makes it no different from any other file -- after all, all files contain data of some sort. As a "database" format, XML has some advantages. For example, it is self-describing (the markup describes the structure and type names of the data, although not the sem ...
Paper
... be decoupled from the server, thus exploiting Web and XML-standards and common practices to provide an open architecture in which new services can be added by Software AG or the Tamino Developer Community, or by custom code at a particular installation. ...
... be decoupled from the server, thus exploiting Web and XML-standards and common practices to provide an open architecture in which new services can be added by Software AG or the Tamino Developer Community, or by custom code at a particular installation. ...
MySQL Cluster - Villanova Computer Science
... Every NDBCluster has a primary key. If no primary key is defined by the user when a table is created, the NDBCluster storage engine automatically generates a hidden one. ...
... Every NDBCluster has a primary key. If no primary key is defined by the user when a table is created, the NDBCluster storage engine automatically generates a hidden one. ...
Title Data-mining tools enabling Herschel science
... used for the paper and associated postcards from ‘On-Line Data’ • ADS include links to Herschel proposal abstracts since only a few months ago How to access the full contents of publications based on Herschel data? Which Herschel observations were used to produce a particular publication? ...
... used for the paper and associated postcards from ‘On-Line Data’ • ADS include links to Herschel proposal abstracts since only a few months ago How to access the full contents of publications based on Herschel data? Which Herschel observations were used to produce a particular publication? ...
EMC BACKUP AND RECOVERY OPTIONS FOR VSPEX FOR VIRTUALIZED ORACLE 11GR2
... EMC believes the information in this publication is accurate of its publication date. The information is subject to change without notice. The information in this publication is provided as is. EMC Corporation makes no representations or warranties of any kind with respect to the information in this ...
... EMC believes the information in this publication is accurate of its publication date. The information is subject to change without notice. The information in this publication is provided as is. EMC Corporation makes no representations or warranties of any kind with respect to the information in this ...
XML - FSU Computer Science Department
... •Today customers of the WEB want to take orders from customers, display medical records, run a factory robot, and HTML is a weak language to do these things. •Your doctor may be able view the web and see your drug reaction history, but he cannot easily add yet a drug reaction that updates the hospit ...
... •Today customers of the WEB want to take orders from customers, display medical records, run a factory robot, and HTML is a weak language to do these things. •Your doctor may be able view the web and see your drug reaction history, but he cannot easily add yet a drug reaction that updates the hospit ...
A Maturity Model for GIS
... Centralization is the typical step taken when an enterprise recognizes that GIS is useful to multiple aspects of its organization, and requires increased rigor and standardization. Centralization may be approached initially as a cost saving measure. It also allows the introduction of GIS capabilitie ...
... Centralization is the typical step taken when an enterprise recognizes that GIS is useful to multiple aspects of its organization, and requires increased rigor and standardization. Centralization may be approached initially as a cost saving measure. It also allows the introduction of GIS capabilitie ...
DTS
... The internal architecture of SSIS is completely different from DTS. The data flow engine is completely segregated from the control flow engine or SSIS Runtime Engine and hence the performance is improved significantly in SSIS. SSIS is now no longer a stand-alone designer. SSIS uses the new devel ...
... The internal architecture of SSIS is completely different from DTS. The data flow engine is completely segregated from the control flow engine or SSIS Runtime Engine and hence the performance is improved significantly in SSIS. SSIS is now no longer a stand-alone designer. SSIS uses the new devel ...
Domain Ontologies: A Database-Oriented Analysis
... The usage of a conceptualization as a specification is the basis of the Model-Driven Architecture (MDA). A model of the application is first defined. This model is then used to generate the code of the application. The existing formal link between the specification and the software enables to evolve ...
... The usage of a conceptualization as a specification is the basis of the Model-Driven Architecture (MDA). A model of the application is first defined. This model is then used to generate the code of the application. The existing formal link between the specification and the software enables to evolve ...
expresstm database – ppdm wells and land
... Industry Standard PPDM Database CWD’s ExpressTM Database provides up-to-date general well data, production data, injection data, AOFP, BHOP, crown data, freehold mineral rights, land sale postings, reserves data, and gas analysis data in the PPDM 3.71 schema for the Western Canadian provinces of Alb ...
... Industry Standard PPDM Database CWD’s ExpressTM Database provides up-to-date general well data, production data, injection data, AOFP, BHOP, crown data, freehold mineral rights, land sale postings, reserves data, and gas analysis data in the PPDM 3.71 schema for the Western Canadian provinces of Alb ...
Query Execution
... Other Data Models - Cont ƒ Class Declarations –e.g. class {
... Other Data Models - Cont ƒ Class Declarations –e.g. class
- }
ƒ Attributes in ODL
–can be simple or complex type
ƒ Relationships in ODL
–e.g. in Movie: relationship Set
Distilling Data in a SIM: A Strategy for the Analysis
... have a VPN connection that could be targeted, whether you have users connecting over a wireless LAN, or whether you have one or many operating systems extant in your organization.3 ...
... have a VPN connection that could be targeted, whether you have users connecting over a wireless LAN, or whether you have one or many operating systems extant in your organization.3 ...
A Graph-based Approach to Vehicle Trajectory Analysis Diansheng
... distance (straight line) and following representative points. A Delaunay Triangulation (DT) is constructed for the extracted representative points. For each trajectory segment, let A and B be its starting and ending points (both are representative points), the interpolation algorithm will find the s ...
... distance (straight line) and following representative points. A Delaunay Triangulation (DT) is constructed for the extracted representative points. For each trajectory segment, let A and B be its starting and ending points (both are representative points), the interpolation algorithm will find the s ...
ECT 360 Introduction to the Class
... start tag for element foo
end tag for element foo
Anything in between the start tag and end tag is
element content
Attributes are additional data associated with an
element
indicated by name/value pairs inside the start tag
•
...
... start tag for element foo
- Cedric
... path between two nodes by a single “//” edge. Removing nodes helps improving schema management, storage and query processing. The PDV tree is actually a data guide, a summary of access paths to nodes useful for queries. On the other hand, PDVs produced from source XML schemas, unlike these schemas, ...
... path between two nodes by a single “//” edge. Removing nodes helps improving schema management, storage and query processing. The PDV tree is actually a data guide, a summary of access paths to nodes useful for queries. On the other hand, PDVs produced from source XML schemas, unlike these schemas, ...
2.1 Clustering in structured p2p systems
... Structured p2p systems use the first category to achieve clustering. As mentioned before, at this kind of p2p systems, a key derived from a hash function is assigned to each data item. CHORD [1] assigns (using a hash function) to each node of the overlay network an identifier so as each node to main ...
... Structured p2p systems use the first category to achieve clustering. As mentioned before, at this kind of p2p systems, a key derived from a hash function is assigned to each data item. CHORD [1] assigns (using a hash function) to each node of the overlay network an identifier so as each node to main ...