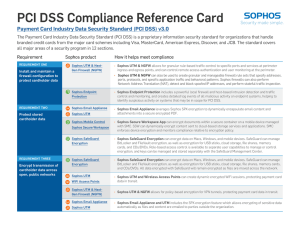
PCI DSS Compliance Reference Card
... PCI DSS Compliance Reference Card Payment Card Industry Data Security Standard (PCI DSS) v3.0 The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, Maste ...
... PCI DSS Compliance Reference Card Payment Card Industry Data Security Standard (PCI DSS) v3.0 The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, Maste ...
M3AAWG Anti-Abuse Best Common Practices for Hosting and Cloud
... ● Virtual Private Server (VPS) An arrangement under which customers are given a virtual server environment in which they usually have admin-level control of that environment. In some cases they may also have guaranteed processes or hardware allocations. The hosting provider owns and provides the vir ...
... ● Virtual Private Server (VPS) An arrangement under which customers are given a virtual server environment in which they usually have admin-level control of that environment. In some cases they may also have guaranteed processes or hardware allocations. The hosting provider owns and provides the vir ...
Design and Implementation of Security Operating System based on
... Analyzes and reviews relative work of security ...
... Analyzes and reviews relative work of security ...
PaaS Acceptable Use Policy
... Customer Server Security. Customer is responsible for ensuring and maintaining security of their systems and the machines that connect to and use PerkinElmer’s cloud solutions, including implementation of necessary patches and operating system updates and protecting its own server, data, password fi ...
... Customer Server Security. Customer is responsible for ensuring and maintaining security of their systems and the machines that connect to and use PerkinElmer’s cloud solutions, including implementation of necessary patches and operating system updates and protecting its own server, data, password fi ...
Defending the Cloud from the Full Stack Hack
... and loading them into a cloud provider with little or no changes ...
... and loading them into a cloud provider with little or no changes ...
latest AHIA and Grant Thornton LLP White Paper: Third
... Establishing effective controls within a vendor management program requires a few basic though not necessarily easy to achieve steps: 1. Identify your vendor population. At many organizations, complete vendor inventories either don’t exist or are out of date. Before you can audit vendors’ complianc ...
... Establishing effective controls within a vendor management program requires a few basic though not necessarily easy to achieve steps: 1. Identify your vendor population. At many organizations, complete vendor inventories either don’t exist or are out of date. Before you can audit vendors’ complianc ...
Success story: China Telecom e-surfing cloud storage
... be constantly expanded. The capacity expansion granularity directly determines carriers' platform construction costs. UDS capacity expansion is based on its UDSNs (also named smart disks), each of which contains a disk drive, an energy-saving ARM chip, small-capacity memory, and an Ethernet interfac ...
... be constantly expanded. The capacity expansion granularity directly determines carriers' platform construction costs. UDS capacity expansion is based on its UDSNs (also named smart disks), each of which contains a disk drive, an energy-saving ARM chip, small-capacity memory, and an Ethernet interfac ...
Cloud Traceability Working Group Face to Face Report
... logstash, kibana) stack – particular reference to UK but widely seen elsewhere too • RAL have ELK infrastructure (on back of castor work), migration to new hardware longer than planned. In place now. Next step to send logs from cloud into that. • RAL have done low level work to tune ELK to better sc ...
... logstash, kibana) stack – particular reference to UK but widely seen elsewhere too • RAL have ELK infrastructure (on back of castor work), migration to new hardware longer than planned. In place now. Next step to send logs from cloud into that. • RAL have done low level work to tune ELK to better sc ...
The Advanced Penetration Testing Boot Camp
... • Two members of Congress have asked the Government Accountability Office (GAO) to review the Federal Communications Commission's approach to medical devices with wireless capabilities to ensure that the devices are "safe, reliable, and secure.” • Medical devices use poorly developed code that often ...
... • Two members of Congress have asked the Government Accountability Office (GAO) to review the Federal Communications Commission's approach to medical devices with wireless capabilities to ensure that the devices are "safe, reliable, and secure.” • Medical devices use poorly developed code that often ...
8th Symposium on Networking and Wireless
... Methods and tools for Ad Hoc Networks Performance modeling and analysis in Wireless Ad Hoc Networks Routing, broadcasting and multicasting in Ad Hoc Networks Energy-efficient protocols for Ad Hoc Networks Resource management, quality of service, and routing in Ad Hoc and Sensor Networks Fault-tolera ...
... Methods and tools for Ad Hoc Networks Performance modeling and analysis in Wireless Ad Hoc Networks Routing, broadcasting and multicasting in Ad Hoc Networks Energy-efficient protocols for Ad Hoc Networks Resource management, quality of service, and routing in Ad Hoc and Sensor Networks Fault-tolera ...
IEEE projects
... Mitigating Cross-Site Scripting Attacks with a Content Security Policy Fast and Scalable Range Query Processing With Strong Privacy Protection for Cloud Computing Graph Regularized Feature Selection with Data Reconstruction Secure Multi-Attribute One-to-Many Bilateral Negotiation Framework for EComm ...
... Mitigating Cross-Site Scripting Attacks with a Content Security Policy Fast and Scalable Range Query Processing With Strong Privacy Protection for Cloud Computing Graph Regularized Feature Selection with Data Reconstruction Secure Multi-Attribute One-to-Many Bilateral Negotiation Framework for EComm ...
Defense - Northwestern Networks Group
... Key Amazon EC2 observations: 1. A single account never has more than one instance running on the same physical machine (this might be an issue..) 2. Strong placement locality. When 2 instances run sequentially or concurrently, most likely on the same machine. 3. Amazon balances load across running m ...
... Key Amazon EC2 observations: 1. A single account never has more than one instance running on the same physical machine (this might be an issue..) 2. Strong placement locality. When 2 instances run sequentially or concurrently, most likely on the same machine. 3. Amazon balances load across running m ...
A Secure Anti-Collusion Data Sharing Scheme for
... of low maintenance and little management cost. Meanwhile, we must provide security guarantees for the sharing data files since they are outsourced. Unfortunately, because of the frequent change of the membership, sharing data while providing privacy-preserving is still a challenging issue, especiall ...
... of low maintenance and little management cost. Meanwhile, we must provide security guarantees for the sharing data files since they are outsourced. Unfortunately, because of the frequent change of the membership, sharing data while providing privacy-preserving is still a challenging issue, especiall ...
Curriculum Vitae - ASU People Search
... ANKUR CHOWDHARY Apt.29, 1700 S College Ave. Tempe AZ-85281 ...
... ANKUR CHOWDHARY Apt.29, 1700 S College Ave. Tempe AZ-85281 ...
UAE Online Child Safety Awareness Campaign
... risks Trust your instinct! And tell your parents/teacher immediately if they you feel threatened or scared Never go alone to meet an Internet friend in person and ask permission before going Think before you post, the Internet never forgets… Be protective of your personal information Trustworthy Com ...
... risks Trust your instinct! And tell your parents/teacher immediately if they you feel threatened or scared Never go alone to meet an Internet friend in person and ask permission before going Think before you post, the Internet never forgets… Be protective of your personal information Trustworthy Com ...
Are Clouds Secure? - San Francisco Bay Area ISSA Chapter
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
Are Clouds Secure?
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
POST MASTER DEGREE IN SECURITY IN COMPUTER SYSTEMS
... analysis of their results in order to find suspicious events. By correlating and aggregating different information, the tool should be able to provide a better picture of what happened in the target system and to automatically detect both consistent and inconsistent scenarios. ...
... analysis of their results in order to find suspicious events. By correlating and aggregating different information, the tool should be able to provide a better picture of what happened in the target system and to automatically detect both consistent and inconsistent scenarios. ...
Enterprise Ready Virtual Private Clouds
... – That is seamlessly connected to one or more enterprise sites ...
... – That is seamlessly connected to one or more enterprise sites ...
The Case for Enterprise Ready Virtual Private Clouds Timothy Wood
... That is seamlessly connected to one or more enterprise sites ...
... That is seamlessly connected to one or more enterprise sites ...
Research Scientist – Prague, Czech Republic Cisco Systems
... Cisco SCO line of products is based on the latest, US Army funded R&D and integrates Artificial Intelligence techniques (statistical analysis, autonomic/agent-based computing, ensemble classification, graph theory, gametheoretic self-optimization) within the framework of distributed, intelligent, an ...
... Cisco SCO line of products is based on the latest, US Army funded R&D and integrates Artificial Intelligence techniques (statistical analysis, autonomic/agent-based computing, ensemble classification, graph theory, gametheoretic self-optimization) within the framework of distributed, intelligent, an ...
billion billion
... As the “GREAT MIGRATION” to cloud begins, Cloud Security as a Service and Cloud Access Security Broker (CASB) products will become more pervasive. ...
... As the “GREAT MIGRATION” to cloud begins, Cloud Security as a Service and Cloud Access Security Broker (CASB) products will become more pervasive. ...
Securing The Cloud
... Manages the physical infrastructure Manages the private cloud resources Configures access to cloud resources ...
... Manages the physical infrastructure Manages the private cloud resources Configures access to cloud resources ...
Cloud Computing Security
... • Shared tenancy of physical storage resources means that sensitive data may leak because data destruction policies may be impossible to implement • Media cannot be physically destroyed because a disk is still being used by another tenant • Customer storage cannot be located or tracked as it moves t ...
... • Shared tenancy of physical storage resources means that sensitive data may leak because data destruction policies may be impossible to implement • Media cannot be physically destroyed because a disk is still being used by another tenant • Customer storage cannot be located or tracked as it moves t ...