* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Are Clouds Secure?
Post-quantum cryptography wikipedia , lookup
Information privacy law wikipedia , lookup
Unix security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Airport security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Wireless security wikipedia , lookup
Security printing wikipedia , lookup
Distributed firewall wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Information security wikipedia , lookup
Cloud computing issues wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Mobile security wikipedia , lookup
Security-focused operating system wikipedia , lookup
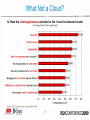
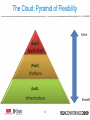
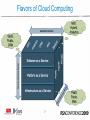
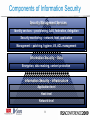
Are Clouds Secure? Security and Privacy Implications of Cloud Computing Subra Kumaraswamy, Sun Tim Mather, RSA 04/21/09 | Session ID: HOT-105 Session Classification: Intermediate What We’re Not Going to Discuss • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor rehash unchanged practices 2 What Not a Cloud? 3 What We Are Going to Discuss Information Security – Infrastructure (network-, host-, application-level) Information Security – Data Security Management Services (security management, security monitoring, identity services) Other Important Considerations (audit & compliance, privacy) Security-as-a- [Cloud] Service (SaaS) Where Risk Has Changed: 4 The Cloud: Types 5 The Cloud: Pyramid of Flexibility (SaaS) (PaaS) (IaaS) 6 Flavors of Cloud Computing 7 The Cloud: How are people using it? 8 Components of Information Security Security Management Services Identity services – provisioning, AAA, federation, delegation Security monitoring – network, host, application Management – patching, hygiene, VA, ACL management Information Security – Data Encryption, data masking, content protection Information Security – Infrastructure Application-level Host-level Network-level 9 Information Security – Infrastructure Infrastructure – Network-level • Shared Infrastructure • VLAN – private and public (tagged) • DHCP server, firewall, load balancer • Limitations • No zones – domains instead • Traditional port/protocol filtering irrelevant • Point-to-point encryption (in transit) is doable • Extranet security jeopardized – unless ‘you’ control cloud (IP) addressing (questionable) • Security monitoring – no transparency 11 Infrastructure – Network-level • Threats • Lack of widespread adoption of secure BGP • Secure BGP (S-BGP), Secure Origin BGP (soBGP), and Pretty Good BGP (pgBGP) • Traffic redirection for eavesdropping • DNS: domain hijacking • Lack of widespread adoption of Secure DNS • Only country-wide adoption: Sweden • DoS / DDoS • Mitigations • Virtual private cloud – VPN-based solution with strong authentication • SSL with client-side certs 12 Infrastructure – Host-level • Shared infrastructure • Hardware – CPU, memory, disks, network • Software – virtualization layer (e.g., Xen) • Web Console – provisioning, image management • Limitations • Ephemeral IP address assignment • Patch, configuration management of large number of dynamic nodes • SLAs are mostly standard – click-through user agreement • Host-based IDS is customer responsibility • Access management – OS and vendor specific 13 Infrastructure – Host-level • Threats • Image configuration drift and vulnerabilities • Targeted DOS attack • Potential breakout of VMs; examples: Subvert, Blue Pill, HyperVM • Attack on standard OS services • Mitigations • Reduce attack surface – Secure-by-default, harden image, turn off OS services, use software firewall, enable logging • Institute process – Access provisioning, patch, config. mgmt. • Extend existing IT security standards, practice & processes • Host-based IDS – Tripwire, OSSEC 14 Infrastructure – Application-level • Shared Infrastructure • Virtualized host, network, firewall (if hosted on IaaS or PaaS) • Virtualized stack (e.g., LAMP) • Database Vs Dataspace (e.g., SimpleDB, BigTable) • Limitations • SaaS – application security is a black box • SaaS/PaaS – no CVE participation • IaaS/PaaS – customer responsibility to secure applications • IaaS/PaaS – Limited capabilities for encryption, identity management • No option to install application firewall 15 Infrastructure – Application-level • Threats • OWASP Top 10 • Mash up security • Denial of service by corporate IPS/Firewalls • Developers side stepping controls • Mitigations • Traditional application security testing and monitoring • Review provider SDLC and security assurance process • If possible encrypt data stored in DB • Manage and protect application “secret keys” • User awareness – phishing attacks on users 16 Information Security – Data Data Security • Confidentiality, Availability • Multi-tenancy • Data-at-rest possibly not encrypted • Data being processed definitely not encrypted • Data lineage (mapping data flows) • Data provenance • Data remanence 18 Security Management Services Security Management – Customer Responsibilities Activities IaaS PaaS OS, DB, Application Hardening and Patching • Manage VM Image hardening • Manage patching of VM , app and DB using your established process • Harden applications by • Not applicable integration by integrating security into SDLC • Test for OWASP Top 10 vulnerabilities Change and configuration • Manage change and management configuration management of host , DB, Application using your established process SaaS • Customer deployed application only • Not applicable Vulnerability management • Manage OS, Application • Customer deployed vulnerabilities leveraging application only your established vulnerability management process • Not applicable Access Control management • Manage Access control to VM, zone firewall using vendor consoles. Install and manage host firewall policies • Manage user provisioning • Restrict access using authentication and IP based restriction • Delegate authentication if SAML supported • Manage user provisioning • Restrict access using authentication and IP based restriction • Delegate authentication if SAML supported Security Monitoring – Customer view Activities IaaS PaaS SaaS Network monitoring • Not available • Not available • Not available Host monitoring • Install and manage HIDS such as OSSEC • Not available • Not available • Not available • Not available • Monitor security events using logs stored in VM Database monitoring • Install DB security monitoring tool on the VM hosting DB Application monitoring • Monitor application security • Monitor application logs logs that may be • Monitor application available – No standard vulnerabilities using your preferred tool Sun ConfidentialInternal Only • Not available Identity Services • Generally, strong authentication is available only through delegation • Federated identity generally not available • Support for SAML v2, WS* and XACML is sporadic • OpenID is not enterprise-ready • OpenID OATH OAuth OpenAuth OpenSSO • All five are “open” and deal with authentication, but…. • Delegated authorization generally not available • Generally weak credential management – of weak credentials 22 Other Important Considerations Audit & Compliance • No audit standards specific to the ‘cloud’ • Not operational, procurement (e.g., FAR), or security • SAS-70 Type 2 is an audit format – not specific audit criteria • Most cloud providers don’t even have a SAS-70 • Compliance: so-called Patriot Act Problem • Location, location, location • Issue is assurance of compliance (e.g., data lineage – let alone data providence) 24 Privacy • Loss of Fourth Amendment protection • Legal order served on provider – not ‘you’ • Some data can be accessed merely by NSLs • Magistrate judge court orders under §215 • Probably no encryption of data-at-rest • No indexing or sorting of encrypted data • Definitely no encryption while data processed • Promise of 2-DNF (homomorphic encryption), Predicate Encryption (asymmetric encryption) • Data remanence: limited attempt to address • NIST Special Publication 800-88, Guidelines for Media Sanitization 25 Security-as-a[Cloud] Service Security Through the Cloud • Proliferation of endpoints • Different OSs, form factors – but all with access to organizational data • Scalability & manageability of existing solutions stretched too far • USENIX paper in July 2008 in San Jose • “CloudAV: N-Version Antivirus in the Network Cloud” • Network-centric: e-mail, vulnerability assessment • Former host resident: anti-malware, content filtering 27 Conclusions • Part of ‘your’ infrastructure security moves beyond your control – Get Ready! • Provider’s infrastructure security may (enterprise) or may not (SMB) be less robust than ‘your’ expectations • Data security becomes significantly more important • Weak access control, credential mgmt. – unless delegated back to ‘you’ 28 Conclusions • No established standards for redaction, obfuscation, or truncation’ • No cloud-specific audit requirements or guidance • “Extending” SAS-70 Type 2 to cloud providers • No cloud-specific regulatory requirements – yet • Some foreign prohibitions on using U.S. cloud providers 29 Questions? 30 Speakers • Subra Kumaraswamy, Senior Security Manager – Sun Microsystems – [email protected] • Tim Mather, Chief Security Strategist – RSA, The Security Division of EMC – [email protected] 31