* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Covert channel
Zero-configuration networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Airborne Networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
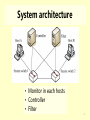
Design of the multi-level security network switch system which restricts covert channel Conference: Communication Software and Networks (ICCSN), 2011 IEEE 3rd International Conference on Authors: Xiong Liu, Haiwei Xue, Xiaoping Feng, Yiqi Dai, Department of Computer Science and Technology, Tsinghua University, Beijing 10084, China 1 Covert channel • In computer security, a covert channel is a type of computer security attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy. 2 Multi-level Security Local Area Network system (MSL) • The low level host can send data packet to high level host, but high level host cannot send data packet to low level host. • TCP/IP SYN/ACK packet cannot be sent back in the above mechanism. So it must allow the sending of SYN/ACK. • The SYN/ACK may become a loophole for the covert channel. Low level 3 High level host System architecture • Monitor in each hosts • Controller • Filter 4 System architecture- Monitor • The system can monitor the hosts’ actions to specify the hosts’ security level by the monitors. • The user must install the monitor in their computer. • Monitor communicate to the controller. 5 System architecture- controller • Functions: – Host registering: Make sure that all the hosts and switches connected to the network are authorized. – Flow computing: Compute the packet’s flow path based on the network’s topological structure. It can make sure all of the data flow paths are compatible with the system’s security policy Level: 2 Level: 3 6 System architecture- controller (cont.d) – Flow updating: When the flow path has been computed, the Controller updates the flow tables of switches which locate on the path to set up it. 7 System architecture- filter • Content check module – Level 1: Check the data field and flags field. – Level 2: Check the unused fields and optional field. – Level 3: Check the sequence number and acknowledgement number. – Level 4: Check the covert channel which uses packet retransmission or packet loss to send information. 8 Experiment 9 Conclusion • This paper proposed a design of multilevel security network switch system which can restrict covert channel. • The design can guarantee the availability and security of the information exchange among hosts in multi-level security network system. The experiment showed that the design is available. 10 Reference • http://en.wikipedia.org/wiki/Covert_cha nnel • [L-BLP security model in local area network],http://www.ejournal.org.cn/C N/abstract/abstract44.shtml 11