* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Distributed Denial of Service (DDoS)
Airport security wikipedia , lookup
Multilevel security wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Wireless security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Unix security wikipedia , lookup
Mobile security wikipedia , lookup
Operation Payback wikipedia , lookup
Computer security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cyberattack wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
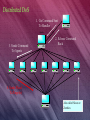
Distributed Denial of Service (DDoS) • Definition: A computer attack that hijacks many other Internet computers and instructs them to inundate a target site with packets or requests for data. • Use of multiple, sometimes compromised systems, to launch attacks • Type of distributed attacks include: – Denial-of-service (Trinoo, tribal flood network, …) – Password cracking (saltine cracker, Slurpie) – Information gathering (none available yet) Distributed DoS 1. Go Command Sent To Handler Attacker Handler 2. Echoes Command Back 3. Sends Command To Agents Agent 1 Agent 2 Agent 3 Agent 4 Agent 5 Agent 6 Agent 7 4. Sends Flood To Target(s) Target Also called Slaves or Zombies DDoS Protective Measures • Keep your systems and applications updated – Automated tools can be used to update systems enterprise wide • Use only trusted tools • Untrusted tools could be used to distribute viruses, Trojan horses and back doors • Employ strong gateway protection (firewall, edge router rules, etc.) • Use intrusion detection tools to detect specific packet attacks • Check for Trojan horse and zombie code – Network vulnerability scans – Host vulnerability scans – Antivirus DDoS Protective Measures • Egress filtering – Disallow packets without valid source address from leaving your network (prevents IP spoofing) – Block certain “broadcast” traffic (for example, ICMP echo reply) • Ingress filtering – ISPs only accept traffic from authorized sources • Have routers turn off forwarding of IP directed broadcast packets • Turn off echo and chargen services Conclusion • Proactive security prevents many attacks – Implement security policy • Fast, robust response is key to handling outbreaks – Implement incident management • Blended threat protection requires comprehensive security across gateways, servers, clients • Security application and management integration increases protection while reducing cost of ownership