CDM-Cyber-Warnings-May-2016
... the Cybersecurity Skills Shortage It’s no secret there’s a severe skills shortage in cybersecurity. More than 209,000 cybersecurity jobs in the U.S. alone are presently unfilled according to a 2015 Peninsula Press analysis of data from the Bureau of Labor Statistics. In addition, according to Penins ...
... the Cybersecurity Skills Shortage It’s no secret there’s a severe skills shortage in cybersecurity. More than 209,000 cybersecurity jobs in the U.S. alone are presently unfilled according to a 2015 Peninsula Press analysis of data from the Bureau of Labor Statistics. In addition, according to Penins ...
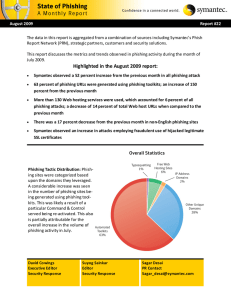
Highlighted in the August 2009 report
... Unique Phishing Web site: The phishing Websites that have a unique Web page are classified as “Unique Phishing Websites”. URLs from phishing toolkits that randomize their URL string are observed to point to the same Web page and do not contain a unique Web page in each URL. Unique Phishing websites ...
... Unique Phishing Web site: The phishing Websites that have a unique Web page are classified as “Unique Phishing Websites”. URLs from phishing toolkits that randomize their URL string are observed to point to the same Web page and do not contain a unique Web page in each URL. Unique Phishing websites ...
Website Appeal: Development of an Assessment Tool and
... marketing efforts of firms trading online [45], [53]. Consequently, a significant amount of work has been done to either extend established marketing models to include elements of digital marketing [23] or build new theoretical paradigms [68] to assess and evaluate marketing over the web. With the e ...
... marketing efforts of firms trading online [45], [53]. Consequently, a significant amount of work has been done to either extend established marketing models to include elements of digital marketing [23] or build new theoretical paradigms [68] to assess and evaluate marketing over the web. With the e ...
Spear Phishing Attacks—Why They are Successful and How to Stop
... The Solution: Next Generation Threat Protection Today, organizations need a new generation of security system, one that detects and blocks the advanced targeted attack techniques that include spear phishing. The following are more details on the FireEye solution to effectively stop advanced targete ...
... The Solution: Next Generation Threat Protection Today, organizations need a new generation of security system, one that detects and blocks the advanced targeted attack techniques that include spear phishing. The following are more details on the FireEye solution to effectively stop advanced targete ...
White Hat SEO Strategies
... maintenance plus new and frequently updated content is required, replacing the old one which when introduced does not keep up with the Google.com page rank, White Hat SEO strategies were duly introduced. ...
... maintenance plus new and frequently updated content is required, replacing the old one which when introduced does not keep up with the Google.com page rank, White Hat SEO strategies were duly introduced. ...
How to promote your childcare using the Internet.
... receive content about your industry. The advantage of email marketing is that you can choose a do-it-yourself option, where you do all the work and save hundreds, perhaps even thousands of dollars. ...
... receive content about your industry. The advantage of email marketing is that you can choose a do-it-yourself option, where you do all the work and save hundreds, perhaps even thousands of dollars. ...
NEW YORK TECH-SECURITY CONFERENCE
... “I didn't get a chance to complete the evaluation form, but the workshop today was EXCELLENT! I just wanted to express my appreciation for the information made available to us at the workshop today. I thought that all of the presenters were clear, concise and provided highly useful and easily unders ...
... “I didn't get a chance to complete the evaluation form, but the workshop today was EXCELLENT! I just wanted to express my appreciation for the information made available to us at the workshop today. I thought that all of the presenters were clear, concise and provided highly useful and easily unders ...
FINANCIAL LITERACY on the WEB - Center for Retirement Research
... analyses that few individuals would have the time, interest, or ability to perform on their own. The technology that drives these aggregators is so sophisticated that they seem deceptively simple to use. Dynamic budgeting tools are currently very popular. They extract spending and income data from a ...
... analyses that few individuals would have the time, interest, or ability to perform on their own. The technology that drives these aggregators is so sophisticated that they seem deceptively simple to use. Dynamic budgeting tools are currently very popular. They extract spending and income data from a ...
1. The Threat Environment: Attackers and their Attacks
... ◦ A group of more than 2,500 retail stores companies operating in the United States, Canada, England, Ireland, and several other countries ◦ Does business under such names as TJ Maxx and Marshalls ...
... ◦ A group of more than 2,500 retail stores companies operating in the United States, Canada, England, Ireland, and several other countries ◦ Does business under such names as TJ Maxx and Marshalls ...
Joshua White - Everis Inc.
... Joshua White Director of CyOON Research and Development “Cyber Operations for Optical Networks” [email protected] Everis Inc http://www.EverisInc.com ...
... Joshua White Director of CyOON Research and Development “Cyber Operations for Optical Networks” [email protected] Everis Inc http://www.EverisInc.com ...
Detecting and Mitigating Persistent Javascript eCommerce Malware
... merchant’s website and compromising payment card data. Visa is providing this report in order to alert eCommerce merchants to this malware technique, and to provide detection and mitigation methods if this malware is discovered. ...
... merchant’s website and compromising payment card data. Visa is providing this report in order to alert eCommerce merchants to this malware technique, and to provide detection and mitigation methods if this malware is discovered. ...
SSL - Security Day´14
... What Is ASM? • Allows the security team to secure a website without changing the ...
... What Is ASM? • Allows the security team to secure a website without changing the ...
The Inside Stories Of The Way To Design A Corporate Website In
... government’s willingness to implement e-governance have already brought success in egovernment initiatives across the industrialised world (see Sharif et al., 2006). In Turkey as well, especially local government restructuring involved ICTs investment more intensive than before. Georgescu (2007) hig ...
... government’s willingness to implement e-governance have already brought success in egovernment initiatives across the industrialised world (see Sharif et al., 2006). In Turkey as well, especially local government restructuring involved ICTs investment more intensive than before. Georgescu (2007) hig ...
Top Five DNS Security Attack Risks and How to Avoid Them
... AT&T suffers DNS outage caused by DDOS attack ...
... AT&T suffers DNS outage caused by DDOS attack ...
Research on Experiential Marketing Strategy in Corporate Websites
... 5.2 Provide opportunities for users involvement of design and manufacturing With virtual products/services on Net, company can encourage customers to participate in company activities. Virtual environment similar to offline shop can give users visual impression of products/ service. Hence, they will ...
... 5.2 Provide opportunities for users involvement of design and manufacturing With virtual products/services on Net, company can encourage customers to participate in company activities. Virtual environment similar to offline shop can give users visual impression of products/ service. Hence, they will ...
Management & Engineering
... 4 Experiential Economy and Experiential Marketing 4.1 Experiential economy and four realms of experience Experiential Economy is characterized as that the consumption is only a process; the memory of experience will be preserved in the minds of consumers permanently at the end of the process. Pine I ...
... 4 Experiential Economy and Experiential Marketing 4.1 Experiential economy and four realms of experience Experiential Economy is characterized as that the consumption is only a process; the memory of experience will be preserved in the minds of consumers permanently at the end of the process. Pine I ...
Bots and Botnets - IT Services Technical Notes
... 2002 Nascar Racing 2003 Rainbow Six III RavenShield Command and Conquer: Tiberian Sun Command and Conquer: Red Alert Command and Conquer: Red Alert 2 NOX Chrome Hidden & Dangerous 2 Soldier of Fortune II - Double Helix Neverwinter Nights Neverwinter Nights (Shadows of Undrentide) Neverwinter Nights ...
... 2002 Nascar Racing 2003 Rainbow Six III RavenShield Command and Conquer: Tiberian Sun Command and Conquer: Red Alert Command and Conquer: Red Alert 2 NOX Chrome Hidden & Dangerous 2 Soldier of Fortune II - Double Helix Neverwinter Nights Neverwinter Nights (Shadows of Undrentide) Neverwinter Nights ...
Computer Security and Penetration Testing Chapter 11 Denial
... • Ping of Death – A historical DoS attack in which the hacker uses the Ping utility to acquire access to a system – Hacker sends a packet larger than 64 KB to the target ...
... • Ping of Death – A historical DoS attack in which the hacker uses the Ping utility to acquire access to a system – Hacker sends a packet larger than 64 KB to the target ...
Defending Office 365 Against Denial-of-Service Attacks
... Office 365 services are intentionally built to support a very high load as well as to protect and mitigate against application-level DoS attacks. We have implemented a scaled-out architecture where services are distributed across multiple global datacenters with regional isolation and throttling fea ...
... Office 365 services are intentionally built to support a very high load as well as to protect and mitigate against application-level DoS attacks. We have implemented a scaled-out architecture where services are distributed across multiple global datacenters with regional isolation and throttling fea ...
Taking on the Giant (anatomy of an attack)
... problems with Windows servers running Trend Micro OfficeScan, which does not have the same vulnerability Josh identifies four compromised servers that launched a Distributed Denial of Service Attack; network access for these servers is blocked The DDoS packets failed to leave the campus since the so ...
... problems with Windows servers running Trend Micro OfficeScan, which does not have the same vulnerability Josh identifies four compromised servers that launched a Distributed Denial of Service Attack; network access for these servers is blocked The DDoS packets failed to leave the campus since the so ...
Master - Anvari.Net
... • An Intrusion Detection System (IDS) is a network security system designed to identify intrusive or malicious behaviour via monitoring of network activity. The IDS identifies suspicious patterns that may indicate an attempt to attack, break in to, or otherwise compromise a system. An IDS can be net ...
... • An Intrusion Detection System (IDS) is a network security system designed to identify intrusive or malicious behaviour via monitoring of network activity. The IDS identifies suspicious patterns that may indicate an attempt to attack, break in to, or otherwise compromise a system. An IDS can be net ...
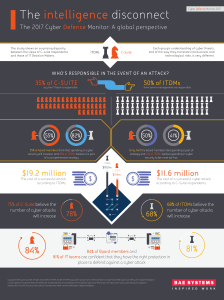
The intelligence disconnect
... security will increase, and 82% of ITDMs believe it is part of a comprehensive strategy ...
... security will increase, and 82% of ITDMs believe it is part of a comprehensive strategy ...
Portfolio for - Warncke Enterprises
... Palmettoguideservice.com - Existing Website Platform Editing and Maintenance Services BrizendinesDeer.com - Custom Website Build, Marketing/Consulting Services TheRustGamePlace.com - Custom Website Build, Graphic Design GhostTargets.com - Consulting Services/Custom Video Production TuskerArchery.com ...
... Palmettoguideservice.com - Existing Website Platform Editing and Maintenance Services BrizendinesDeer.com - Custom Website Build, Marketing/Consulting Services TheRustGamePlace.com - Custom Website Build, Graphic Design GhostTargets.com - Consulting Services/Custom Video Production TuskerArchery.com ...
Operation Payback

Operation Payback was a coordinated, decentralized group of attacks on high profile opponents of Internet piracy by Internet activists using the ""Anonymous"" moniker. Operation Payback started as retaliation to distributed denial of service (DDoS) attacks on torrent sites; piracy proponents then decided to launch DDoS attacks on piracy opponents. The initial reaction snowballed into a wave of attacks on major pro-copyright and anti-piracy organizations, law firms, and individuals.Following the United States diplomatic cables leak in December 2010, the organizers commenced DDoS attacks on websites of banks who had withdrawn banking facilities from WikiLeaks.