Network Security Network Attacks and Mitigation
... • A DoS attack damages or corrupts your computer system or denies you and others access to your networks, systems, or services. ...
... • A DoS attack damages or corrupts your computer system or denies you and others access to your networks, systems, or services. ...
Aaron Wilson – Web Designer / Developer 704-254
... ad campaigns. Work with sales force to develop PHP and MySQL password protected online marketing material database. Develop monthly e-newsletter in HTML and CSS for delivery to customer email list. Manage in-house hosted websites on Windows IIS Server. Develop custom HTML website landing pages for t ...
... ad campaigns. Work with sales force to develop PHP and MySQL password protected online marketing material database. Develop monthly e-newsletter in HTML and CSS for delivery to customer email list. Manage in-house hosted websites on Windows IIS Server. Develop custom HTML website landing pages for t ...
Key To Personal Information Security
... • Sniffer programs exploit this characteristic, monitoring all traffic and capturing the first 128 bytes or so of every unencrypted FTP or Telnet session (the part that contains user passwords) • It is estimated that in the last year more than 100,000 systems were victims of packet sniffers ...
... • Sniffer programs exploit this characteristic, monitoring all traffic and capturing the first 128 bytes or so of every unencrypted FTP or Telnet session (the part that contains user passwords) • It is estimated that in the last year more than 100,000 systems were victims of packet sniffers ...
Introduction to management of Information Technologies
... An attacker is preparing an attack. He got the IP address of a potential target. Which of the following could he use in order to determine whether or not the potential target exist, is connected to the network, and is maybe responsive? a) b) c) ...
... An attacker is preparing an attack. He got the IP address of a potential target. Which of the following could he use in order to determine whether or not the potential target exist, is connected to the network, and is maybe responsive? a) b) c) ...
F5 Silverline Protect Your Business and Stay Online
... DDoS attacks are increasing in scale and complexity, threatening to overwhelm the internal resources of businesses globally. These attacks combine high-volume traffic clogging with stealthy, low-and-slow, application-targeted techniques. To stop DDoS attacks from reaching the enterprise network, org ...
... DDoS attacks are increasing in scale and complexity, threatening to overwhelm the internal resources of businesses globally. These attacks combine high-volume traffic clogging with stealthy, low-and-slow, application-targeted techniques. To stop DDoS attacks from reaching the enterprise network, org ...
Slides - TAMU Computer Science Faculty Pages
... • Internet infrastructure (e.g., DNS, BGP) is trustworthy – DNS is more vulnerable than you think … ...
... • Internet infrastructure (e.g., DNS, BGP) is trustworthy – DNS is more vulnerable than you think … ...
an inside look at botnets
... – October 2002 – Simple code in C, 2000 lines – IRC based command and control system – Easy to extend and so many patches available(DOS attacks, information harvesting routines) – Motivation for patch dissemination is diffusion of accountability ...
... – October 2002 – Simple code in C, 2000 lines – IRC based command and control system – Easy to extend and so many patches available(DOS attacks, information harvesting routines) – Motivation for patch dissemination is diffusion of accountability ...
General Overview of Attacks
... version of UNIX, including installation of “Sniffers” that can steal unencrypted passwords when people log on to the systems. 3. Denial-of-service attacks were particularly troubling for internet service providers. ...
... version of UNIX, including installation of “Sniffers” that can steal unencrypted passwords when people log on to the systems. 3. Denial-of-service attacks were particularly troubling for internet service providers. ...
Aon Presentation 17-3-11 - Class Leading Solutions
... Just a website isn’t good enough any more if winning new business, increasing barriers, retaining clients, gaining competitive advantage, etc are important to you. The 6-8% Rule. Having a website is almost never actually using the technology to the Practices benefit. ...
... Just a website isn’t good enough any more if winning new business, increasing barriers, retaining clients, gaining competitive advantage, etc are important to you. The 6-8% Rule. Having a website is almost never actually using the technology to the Practices benefit. ...
Chap 3
... Floods a host with ICMP Saturates Internet connection with bogus traffic and delays/prevents legitimate traffic from reaching its destination ...
... Floods a host with ICMP Saturates Internet connection with bogus traffic and delays/prevents legitimate traffic from reaching its destination ...
Attacks and Mitigations
... – Computers are often recruited into a botnet by running malicious software. This may be achieved by luring users with a drive-by download, exploiting web browser vulnerabilities, or tricking the user into running a Trojan horse program, possibly in an email attachment. It will typically install mod ...
... – Computers are often recruited into a botnet by running malicious software. This may be achieved by luring users with a drive-by download, exploiting web browser vulnerabilities, or tricking the user into running a Trojan horse program, possibly in an email attachment. It will typically install mod ...
Responding to Intrusions
... between two active nodes on a network. Identity spoofing, aka IP address spoofing, occurs when an attacker assumes the source IP address of IP packets to make it appear as though the packet originated from a valid IP address. A sniffer attack occurs when attackers capture and analyze network traffic ...
... between two active nodes on a network. Identity spoofing, aka IP address spoofing, occurs when an attacker assumes the source IP address of IP packets to make it appear as though the packet originated from a valid IP address. A sniffer attack occurs when attackers capture and analyze network traffic ...
attacks
... threat agent that damages or steals information or physical assets. Vulnerability ◦ an identified weakness in a controlled system, where controls are not present or no longer effective. ...
... threat agent that damages or steals information or physical assets. Vulnerability ◦ an identified weakness in a controlled system, where controls are not present or no longer effective. ...
Session 1 Framework
... Internet • Protect the Internet from their customers • At any given time there are between 20 to 40 DOS/DDOS attacks on the Net ...
... Internet • Protect the Internet from their customers • At any given time there are between 20 to 40 DOS/DDOS attacks on the Net ...
ch08 - Columbus State University
... various protocols e.g. UDP or TCP/SYN ideally want response larger than request prevent if block source spoofed packets ...
... various protocols e.g. UDP or TCP/SYN ideally want response larger than request prevent if block source spoofed packets ...
APT-Tactics
... We detail the typical intentions of an attacker and the tools and processes they would leverage to attain these goals. Lastly, the course presents key approaches to detect and terminate the process of an APT, and the infrastructure required for effective incident response. ...
... We detail the typical intentions of an attacker and the tools and processes they would leverage to attain these goals. Lastly, the course presents key approaches to detect and terminate the process of an APT, and the infrastructure required for effective incident response. ...
Intrusion Detection Systems
... successively trying all the words in some large, exhaustive list. For example, an attack on an authentication service by trying all possible passwords; or an attack on encryption by encrypting some known plaintext phrase with all possible keys so that the key for any given encrypted message containi ...
... successively trying all the words in some large, exhaustive list. For example, an attack on an authentication service by trying all possible passwords; or an attack on encryption by encrypting some known plaintext phrase with all possible keys so that the key for any given encrypted message containi ...
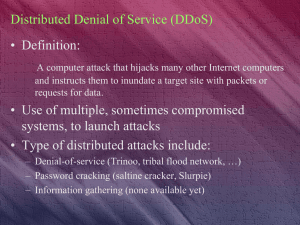
Distributed Denial of Service (DDoS)
... A computer attack that hijacks many other Internet computers and instructs them to inundate a target site with packets or requests for data. ...
... A computer attack that hijacks many other Internet computers and instructs them to inundate a target site with packets or requests for data. ...
Mitigating DDoS Attacks
... Aim to disable the critical service of the whole Internet, such as root DNS ...
... Aim to disable the critical service of the whole Internet, such as root DNS ...
DDoS Attacks: What You Can`t See Can Hurt You Dave Larson
... The Attackers are Getting Smarter Researchers are finding an uptick in the number of new techniques Attackers defeating traditional protection (Firewall, ACL, Blackhole) Attackers are developing new methods of bypassing defenses ...
... The Attackers are Getting Smarter Researchers are finding an uptick in the number of new techniques Attackers defeating traditional protection (Firewall, ACL, Blackhole) Attackers are developing new methods of bypassing defenses ...
Anonymous - ACG 6415
... In its early form, the concept had been adopted by a decentralized online community acting anonymously in a synchronized manner, usually in the direction of a loosely group-chosen goal, but the primary focus was to entertain them. Began in 2008 as a decentralized network of individuals, and beca ...
... In its early form, the concept had been adopted by a decentralized online community acting anonymously in a synchronized manner, usually in the direction of a loosely group-chosen goal, but the primary focus was to entertain them. Began in 2008 as a decentralized network of individuals, and beca ...
Operation Payback

Operation Payback was a coordinated, decentralized group of attacks on high profile opponents of Internet piracy by Internet activists using the ""Anonymous"" moniker. Operation Payback started as retaliation to distributed denial of service (DDoS) attacks on torrent sites; piracy proponents then decided to launch DDoS attacks on piracy opponents. The initial reaction snowballed into a wave of attacks on major pro-copyright and anti-piracy organizations, law firms, and individuals.Following the United States diplomatic cables leak in December 2010, the organizers commenced DDoS attacks on websites of banks who had withdrawn banking facilities from WikiLeaks.