* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Data Security
Access control wikipedia , lookup
Information privacy law wikipedia , lookup
Wireless security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Mobile security wikipedia , lookup
Computer virus wikipedia , lookup
Security-focused operating system wikipedia , lookup
Data remanence wikipedia , lookup
Cyberattack wikipedia , lookup
Computer security wikipedia , lookup
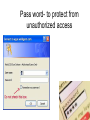
Data Security Unauthorized Access Natural disaster Accidentals Destruction ( Hard ware failure ) Natural disaster Accidentals Destruction ( Hardware failure ) Back up Mostly protect data from natural disasters Unauthorized Access • Passwords • Locks Some computers may have locks on them. • Biometrics Locks. Bio Matrix system- to protect data from unauthorized access Pass word- to protect from unauthorized access • Theft of data. passwords locks encryption Hackers • someone who can gain unauthorized access to other computers. • This can be as simple as figuring out somebody else's password or as complex as writing a custom program to break another computer's security software. DATA SAFETY • Hacking • Hackers can change files or can make transactions. • We can protect our data from hackers by using fairwall. • Viruses • a program or part of code that is loaded onto your PC without your knowledge & runs against your wishes. virus • Computer viruses are programs written by "mean" people. • Some viruses are programmed specifically to damage the data on your computer by corrupting programs, deleting files, or even erasing your entire hard drive. Trojan Horses • A trojan horse is not a virus. It is a program that you run because you think it will serve a useful purpose such as a game or provides entertainment. Like a "trojan horse" • A trojan horse does not replicate or spread like a virus. • Trojan Horses • a destructive program that masquerades as a benign application. Unlike viruses, Trojan horses don’t replicate themselves. • Worms –a program or algorithm that replicates itself over a computer network & usually performs malicious actions, Antivirus Hardware protection • UPS (uninterrupted power supply )-to avoid the risk of sudden power failure and fluctuations • Stabilizer – to control the voltage • Surge protection- to protect agents lightning and thundering • Surge protection to protect against lightening & thunder. • Stabilizer –To control the voltage. COMPUTER & SECURITY We can mainly divided computer & security for the 3 parts. computer safety. data safety. our safety. • Hardware protecting UPS –(uninterrupted power supplier) To avoid risk of sudden power failure& fluctuations, Computer security • • • • • Physical security Environment should be.... 1) dust free 2) Dry 3) smoke free COMPUTER SECURITY • Physical security dust free dry smoke free