2-7 The Mathematics Models and an Actual Proof Experiment
... include the ICMP, IPPM, and HASH methods. In the case of the ICMP and IPPM methods, routers generate traceback information on attack packets with a certain probability. Traceback paths to attackers are confirmed based on the generation of this information. One can therefore calculate the attacker-de ...
... include the ICMP, IPPM, and HASH methods. In the case of the ICMP and IPPM methods, routers generate traceback information on attack packets with a certain probability. Traceback paths to attackers are confirmed based on the generation of this information. One can therefore calculate the attacker-de ...
NetDefend Family Overview & Strategy
... The hardware of D-Link Firewalls DFL-210/260/800/860/1600/2500 is driven and controlled by NetDefendOS. Designed as a dedicated firewall operating system, NetDefendOS features high throughput performance with high reliability while at the same time implementing the key elements of IPS/UTM firewall. ...
... The hardware of D-Link Firewalls DFL-210/260/800/860/1600/2500 is driven and controlled by NetDefendOS. Designed as a dedicated firewall operating system, NetDefendOS features high throughput performance with high reliability while at the same time implementing the key elements of IPS/UTM firewall. ...
Configuring VoIP for SonicOS Enhanced
... as an application on the network makes those threats even more dangerous. By adding VoIP components to your network, you’re also adding new security requirements. VoIP encompasses a number of complex standards that leave the door open for bugs and vulnerabilities within the software implementation. ...
... as an application on the network makes those threats even more dangerous. By adding VoIP components to your network, you’re also adding new security requirements. VoIP encompasses a number of complex standards that leave the door open for bugs and vulnerabilities within the software implementation. ...
A. IMS/Internet interworking scenario.
... integrity, integrity mechanisms always provide some type of proof of data origin. Knowing that a message has not been modified without knowing who initially created the message would be useless. Confidentiality mechanisms keep unauthorized parties from getting access to the contents of a message. Co ...
... integrity, integrity mechanisms always provide some type of proof of data origin. Knowing that a message has not been modified without knowing who initially created the message would be useless. Confidentiality mechanisms keep unauthorized parties from getting access to the contents of a message. Co ...
What Is a Virtual Private Network?
... A virtual private network (VPN) allows the provisioning of private network services for an organization or organizations over a public or shared infrastructure such as the Internet or service provider backbone network. The shared service provider backbone network is known as the VPN backbone and is ...
... A virtual private network (VPN) allows the provisioning of private network services for an organization or organizations over a public or shared infrastructure such as the Internet or service provider backbone network. The shared service provider backbone network is known as the VPN backbone and is ...
AWS Overview of Security Processes
... components from the host operating system and virtualization layer down to the physical security of the facilities in which the services operate. In turn, customers assume responsibility for and management of their operating system (including updates and security patches), other associated applicati ...
... components from the host operating system and virtualization layer down to the physical security of the facilities in which the services operate. In turn, customers assume responsibility for and management of their operating system (including updates and security patches), other associated applicati ...
Protect Your Wireless Network From Attack
... include network security architecture and wireless network design, as well as the implementation of Juniper routers. Donald’s background includes a successful career with International Network Services, and now Lucent Technologies. Besides “unwiring” corporate offices, Donald has spent considerable ...
... include network security architecture and wireless network design, as well as the implementation of Juniper routers. Donald’s background includes a successful career with International Network Services, and now Lucent Technologies. Besides “unwiring” corporate offices, Donald has spent considerable ...
FRITZ!WLAN USB Stick AC 860
... Connecting Computers Directly (Ad Hoc Network) In a direct connection (also called an ad hoc network), computers are connected with each other without any wireless access point like the FRITZ!Box involved. If you set up an ad hoc network on a computer with the FRITZ!WLAN USB stick, other computers c ...
... Connecting Computers Directly (Ad Hoc Network) In a direct connection (also called an ad hoc network), computers are connected with each other without any wireless access point like the FRITZ!Box involved. If you set up an ad hoc network on a computer with the FRITZ!WLAN USB stick, other computers c ...
Reference Manual for the 108 Mbps Wireless Firewall
... browsing activity reporting and instant alerts via e-mail. Parents and network administrators can establish restricted access policies based on time-of-day, web site addresses and address keywords, and share high-speed cable/DSL Internet access for up to 253 computers. In addition to the Network Add ...
... browsing activity reporting and instant alerts via e-mail. Parents and network administrators can establish restricted access policies based on time-of-day, web site addresses and address keywords, and share high-speed cable/DSL Internet access for up to 253 computers. In addition to the Network Add ...
Attack Detection and Defense Mechanisms
... Juniper Networks, Junos, Steel-Belted Radius, NetScreen, and ScreenOS are registered trademarks of Juniper Networks, Inc. in the United States and other countries. JunosE is a trademark of Juniper Networks, Inc. All other trademarks, service marks, registered trademarks, or registered service marks ...
... Juniper Networks, Junos, Steel-Belted Radius, NetScreen, and ScreenOS are registered trademarks of Juniper Networks, Inc. in the United States and other countries. JunosE is a trademark of Juniper Networks, Inc. All other trademarks, service marks, registered trademarks, or registered service marks ...
CIS Cisco IOS 15 Benchmark
... warranties, or covenants of any kind whatsoever (including the absence of any warranty regarding: (a) the effect or lack of effect of any SB Product on the operation or the security of any network, system, software, hardware, or any component of any of them, and (b) the accuracy, utility, reliabilit ...
... warranties, or covenants of any kind whatsoever (including the absence of any warranty regarding: (a) the effect or lack of effect of any SB Product on the operation or the security of any network, system, software, hardware, or any component of any of them, and (b) the accuracy, utility, reliabilit ...
Penetration Testing and Network Defense
... tests for financial institutions across the southeastern United States. He also was previously employed as a senior network engineer with an online banking company, where he was responsible for network security implementation and data communications for e-finance websites. He is certified in the follow ...
... tests for financial institutions across the southeastern United States. He also was previously employed as a senior network engineer with an online banking company, where he was responsible for network security implementation and data communications for e-finance websites. He is certified in the follow ...
Chapter 12 PowerPoint
... Only one IPSec policy can be assigned per computer. Define policies for computers, not for users. Define the protocol requirements so that explicit filters can be defined, and determine attributes for each required filter. IPSec encrypted traffic cannot be identified if it ...
... Only one IPSec policy can be assigned per computer. Define policies for computers, not for users. Define the protocol requirements so that explicit filters can be defined, and determine attributes for each required filter. IPSec encrypted traffic cannot be identified if it ...
“Computers in Communication” by Gordon Brebner
... in communication. The end result is to allow the sharing of computer-based resources that are physically located in all parts of the world. From the point of view of most users, the mechanisms by which computers communicate are best kept hidden. However, without these mechanisms, no sharing of resou ...
... in communication. The end result is to allow the sharing of computer-based resources that are physically located in all parts of the world. From the point of view of most users, the mechanisms by which computers communicate are best kept hidden. However, without these mechanisms, no sharing of resou ...
IPv6 Infrastructure Security
... Microsoft Windows • XP – w/SP2 - must install IPv6 protocol – Uses M-EUI-64 Interface address, no client DHCPv6 support ...
... Microsoft Windows • XP – w/SP2 - must install IPv6 protocol – Uses M-EUI-64 Interface address, no client DHCPv6 support ...
Firewalls - Andrew.cmu.edu - Carnegie Mellon University
... • allow news reading but not news posting • allow login from inside to outside but not vice versa • allow file transfer to a single system in your domain ...
... • allow news reading but not news posting • allow login from inside to outside but not vice versa • allow file transfer to a single system in your domain ...
Configuring VoIP for SonicOS Standard
... as an application on the network makes those threats even more dangerous. By adding VoIP components to your network, you’re also adding new security requirements. VoIP encompasses a number of complex standards that leave the door open for bugs and vulnerabilities within the software implementation. ...
... as an application on the network makes those threats even more dangerous. By adding VoIP components to your network, you’re also adding new security requirements. VoIP encompasses a number of complex standards that leave the door open for bugs and vulnerabilities within the software implementation. ...
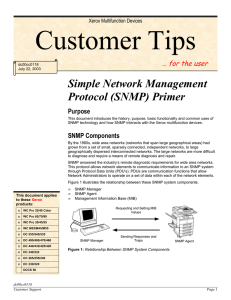
Simple Network Management Protocol (SNMP) Primer
... Read-Only: When the Community String is set to Read-Only, the information in the MIB can only be read and not modified. A client is only allowed to issue getRequest and getNextRequest commands with the Read-Only community name. Read-Write: A Read-Write setting allows the value of the MIB object to b ...
... Read-Only: When the Community String is set to Read-Only, the information in the MIB can only be read and not modified. A client is only allowed to issue getRequest and getNextRequest commands with the Read-Only community name. Read-Write: A Read-Write setting allows the value of the MIB object to b ...
Reference Manual for the 54 Mbps Wireless Router WGR614 v6 202-10099-01, April 2005
... Network, Routing, Firewall, and Basics Related Publications ...................................................................................................... B-1 Basic Router Concepts .................................................................................................. B-1 What is ...
... Network, Routing, Firewall, and Basics Related Publications ...................................................................................................... B-1 Basic Router Concepts .................................................................................................. B-1 What is ...
Technical Presentation
... SIP Protocol is an Application Layer Protocol Network Address Translation (NAT) resides at the Transport Layer (TCP/IP) NAT will not change the SIP addressing within the TCP/UDP datagram Firewalls are a NATing device and BLOCK all Incoming SIP Traffic to the LAN Any NAT device, either Far End (remot ...
... SIP Protocol is an Application Layer Protocol Network Address Translation (NAT) resides at the Transport Layer (TCP/IP) NAT will not change the SIP addressing within the TCP/UDP datagram Firewalls are a NATing device and BLOCK all Incoming SIP Traffic to the LAN Any NAT device, either Far End (remot ...
Ingate Firewall & SIParator Training
... SIP Protocol is an Application Layer Protocol Network Address Translation (NAT) resides at the Transport Layer (TCP/IP) NAT will not change the SIP addressing within the TCP/UDP datagram Firewalls are a NATing device and BLOCK all Incoming SIP Traffic to the LAN Any NAT device, either Far End (remot ...
... SIP Protocol is an Application Layer Protocol Network Address Translation (NAT) resides at the Transport Layer (TCP/IP) NAT will not change the SIP addressing within the TCP/UDP datagram Firewalls are a NATing device and BLOCK all Incoming SIP Traffic to the LAN Any NAT device, either Far End (remot ...
Cisco SAFE Reference Guide
... While the target audience is technical in nature, business decision makers, senior IT leaders, and systems architects can benefit from understanding the design driving principles and fundamental security concepts. ...
... While the target audience is technical in nature, business decision makers, senior IT leaders, and systems architects can benefit from understanding the design driving principles and fundamental security concepts. ...
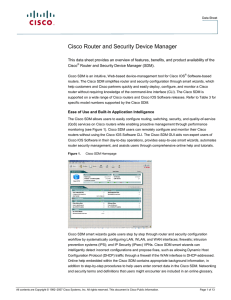
Cloud and Network Services
... workflow by systematically configuring LAN, WLAN, and WAN interfaces; firewalls; intrusion prevention systems (IPS); and IP Security (IPsec) VPNs. Cisco SDM smart wizards can intelligently detect incorrect configurations and propose fixes, such as allowing Dynamic Host Configuration Protocol (DHCP) ...
... workflow by systematically configuring LAN, WLAN, and WAN interfaces; firewalls; intrusion prevention systems (IPS); and IP Security (IPsec) VPNs. Cisco SDM smart wizards can intelligently detect incorrect configurations and propose fixes, such as allowing Dynamic Host Configuration Protocol (DHCP) ...
EE579S Computer Security
... • Security is something most users want, but that most know little about • Security gets in the way of using the computer system • The tighter the security, the harder the system is to use, and the more likely it is that the users will bypass security measures Spring 2011 © 2000-2011, Richard A. Sta ...
... • Security is something most users want, but that most know little about • Security gets in the way of using the computer system • The tighter the security, the harder the system is to use, and the more likely it is that the users will bypass security measures Spring 2011 © 2000-2011, Richard A. Sta ...