security_6
... software to send a flood of data packets to the target computer with the aim of overloading its resources. ...
... software to send a flood of data packets to the target computer with the aim of overloading its resources. ...
Why Cryptography is Harder Than It Looks
... • Vast knowledge and free time • Few financial resources and / or vendetta ...
... • Vast knowledge and free time • Few financial resources and / or vendetta ...
Security - UTRGV Faculty Web
... bob’s public key to encrypt, only bob with his private key can decrypt. ...
... bob’s public key to encrypt, only bob with his private key can decrypt. ...
E-Surveillance and User Privacy
... signature of allowed binaries – if not allowed, execution denied • Prevents unauthorized indirect branching • Protects from buffer overflow attacks • Cost – 35% performance hit! • Weakness – Does not protect against scripted (interpreted) code attacks – Perl, VB, etc ...
... signature of allowed binaries – if not allowed, execution denied • Prevents unauthorized indirect branching • Protects from buffer overflow attacks • Cost – 35% performance hit! • Weakness – Does not protect against scripted (interpreted) code attacks – Perl, VB, etc ...
Chapter 5 - Department of Computer Science and Information Systems
... Antivirus software is a defense strategy Antivirus software matches the contents of a file under examination against a database of virus “signatures” Thus, antivirus software cannot protect against viruses that have not been discovered earlier and recorded in the database One of the most likely plac ...
... Antivirus software is a defense strategy Antivirus software matches the contents of a file under examination against a database of virus “signatures” Thus, antivirus software cannot protect against viruses that have not been discovered earlier and recorded in the database One of the most likely plac ...
it user svq – level 2
... o Access control devices (e.g. locks, biometric controls, CCTV); o Limiting visibility of data (e.g. by positioning of monitors, using encryption); o Shielding (e.g. cable screening, Faraday cages); ...
... o Access control devices (e.g. locks, biometric controls, CCTV); o Limiting visibility of data (e.g. by positioning of monitors, using encryption); o Shielding (e.g. cable screening, Faraday cages); ...
CS 494/594 Computer and Network Security - UTK-EECS
... SQL injection, buffer overflow, directory traversal, cryptographic issues such as missing encryption/ authentication, using broken cryptographic schemes and improper authorization ...
... SQL injection, buffer overflow, directory traversal, cryptographic issues such as missing encryption/ authentication, using broken cryptographic schemes and improper authorization ...
CS 494/594 Computer and Network Security - UTK-EECS
... SQL injection, buffer overflow, directory traversal, cryptographic issues such as missing encryption/ authentication, using broken cryptographic schemes and improper authorization ...
... SQL injection, buffer overflow, directory traversal, cryptographic issues such as missing encryption/ authentication, using broken cryptographic schemes and improper authorization ...
Chapter 5 Protecting Information Resources
... ◦ Especially in recent years, with “hackers” becoming more numerous and adept at stealing and altering private information ◦ 1. Comprehensive security system ◦ 2. Threats: ...
... ◦ Especially in recent years, with “hackers” becoming more numerous and adept at stealing and altering private information ◦ 1. Comprehensive security system ◦ 2. Threats: ...
Networking and System Administration (NaSA) Bachelor of Science in
... The Networking and System Administration major is a timely program aimed at preparing graduates for careers and research opportunities in all fields related to reliable and distributed network computing. Career Paths Include: ...
... The Networking and System Administration major is a timely program aimed at preparing graduates for careers and research opportunities in all fields related to reliable and distributed network computing. Career Paths Include: ...
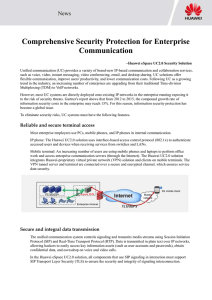
Comprehensive Security Protection for
... flexible communication, improve users' productivity, and lower communication costs. Following UC as a growing trend in the industry, an increasing number of enterprises are upgrading from their traditional Time-division Multiplexing (TDM) to VoIP networks. However, most UC systems are directly deplo ...
... flexible communication, improve users' productivity, and lower communication costs. Following UC as a growing trend in the industry, an increasing number of enterprises are upgrading from their traditional Time-division Multiplexing (TDM) to VoIP networks. However, most UC systems are directly deplo ...
Crime and Security in the Networked Economy Part 4
... Encrypting Communications Increases Security ...
... Encrypting Communications Increases Security ...
Document
... Use a network, or bot-net, of compromised, remotely controlled systems to coordinate attacks and to distribute phishing schemes, spam, and malware attacks. The services of these networks are sometimes made available on underground markets. ...
... Use a network, or bot-net, of compromised, remotely controlled systems to coordinate attacks and to distribute phishing schemes, spam, and malware attacks. The services of these networks are sometimes made available on underground markets. ...
Mullvad Barnprogram
... Mullvad Barnprogram - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
... Mullvad Barnprogram - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
Security Considerations for Health Care Organizations
... Presentation is for educational purposes only and does not constitute legal advice. If you require legal advice, you should consult with an attorney. ...
... Presentation is for educational purposes only and does not constitute legal advice. If you require legal advice, you should consult with an attorney. ...
Chapter 2: Attackers and Their Attacks
... Certain types of local area networks (LANs), such as Ethernet, must also have another address, called the media access control (MAC) address, to move information around the network Computers on a network keep a table that links an IP address with the corresponding address In ARP spoofing, a hack ...
... Certain types of local area networks (LANs), such as Ethernet, must also have another address, called the media access control (MAC) address, to move information around the network Computers on a network keep a table that links an IP address with the corresponding address In ARP spoofing, a hack ...
The wild world of malware: Keeping your
... likely to have IT personnel whose sole focus is network security. This paper examines the current drivers of malware development, details the characteristics of each, discusses how they manifest themselves on the network, and points to how each can be remedied. While the names of many forms of malwa ...
... likely to have IT personnel whose sole focus is network security. This paper examines the current drivers of malware development, details the characteristics of each, discusses how they manifest themselves on the network, and points to how each can be remedied. While the names of many forms of malwa ...
Maritime Cyber Vulnerabilities in the Energy Domain
... Maritime Cyber Vulnerabilities in the Energy Sector Center for Joint Operations of the Sea ODU Maritime Institute Students Crow, Fresco, Lee ...
... Maritime Cyber Vulnerabilities in the Energy Sector Center for Joint Operations of the Sea ODU Maritime Institute Students Crow, Fresco, Lee ...
Module3 - ITProGuru Blog
... Q. How do I securely connect my on-premises environment to the cloud? Azure Customer Site ...
... Q. How do I securely connect my on-premises environment to the cloud? Azure Customer Site ...
Web Application Security
... in the form of a script, to a different end user. Can occur to web applications that use input from a user (without validation) in the output the application generates (e.g.: Forums, Blogs) Other users may not aware of the risk because the script comes from a trusted website. Script can access ...
... in the form of a script, to a different end user. Can occur to web applications that use input from a user (without validation) in the output the application generates (e.g.: Forums, Blogs) Other users may not aware of the risk because the script comes from a trusted website. Script can access ...
Systems Security
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
Wireless Networking & Security
... Required support of TKIP and AES protocols "Hole 196" Attack: o Allows already authenticated user to spoof mac address of router using the Group Temporal Key (known to all clients) o Client responds using their Pairwise Transient Key, which is unique to them, allowing attacker to decrypt the clients ...
... Required support of TKIP and AES protocols "Hole 196" Attack: o Allows already authenticated user to spoof mac address of router using the Group Temporal Key (known to all clients) o Client responds using their Pairwise Transient Key, which is unique to them, allowing attacker to decrypt the clients ...