Operating Systems - Personal Web Server
... Adaptability to a specific environment, like Unix can be in Minicomputer or PC Transparency Users are unaware of all details they need not know Security Protecting data from unauthorized access Integrity Protecting itself and users from damage or any other ill effect of other’s error or mali ...
... Adaptability to a specific environment, like Unix can be in Minicomputer or PC Transparency Users are unaware of all details they need not know Security Protecting data from unauthorized access Integrity Protecting itself and users from damage or any other ill effect of other’s error or mali ...
View the graphic
... • Class leading Advanced Malware Protection (AMP) and Next-Generation Intrusion Prevention System (IPS) capability ...
... • Class leading Advanced Malware Protection (AMP) and Next-Generation Intrusion Prevention System (IPS) capability ...
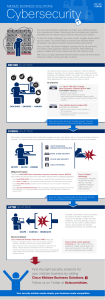
The Need for Information Security
... interdependent support systems • Internet service, communications, and ...
... interdependent support systems • Internet service, communications, and ...
security
... Hacking - Cracking Passwords • Cracking Passwords – remote access • Dictionary attack is trying to determine a decryption key or pass-phrase by searching a large number of possibilities • Remote access to a user’s account allows files to be copied or corrupted. • Hacking used to be a game – now it ...
... Hacking - Cracking Passwords • Cracking Passwords – remote access • Dictionary attack is trying to determine a decryption key or pass-phrase by searching a large number of possibilities • Remote access to a user’s account allows files to be copied or corrupted. • Hacking used to be a game – now it ...
TMDE Web Site
... • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
... • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
AccessControlSimulation
... IRS has implemented an access authorization control for a system used to process electronic tax payment information; however, users had the capability to circumvent this control and gain access to this system’s server. ...
... IRS has implemented an access authorization control for a system used to process electronic tax payment information; however, users had the capability to circumvent this control and gain access to this system’s server. ...
Word
... - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or V.T.O.C. - sends message when disk is full or there is some other problem with writing data to the disk - virtual memory - CD-ROM, DVD-ROM - Flash drive Provides the Interface for Input and Output Devices ...
... - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or V.T.O.C. - sends message when disk is full or there is some other problem with writing data to the disk - virtual memory - CD-ROM, DVD-ROM - Flash drive Provides the Interface for Input and Output Devices ...
Blue Coat Mail Threat Defense
... © 2016 Blue Coat Systems, Inc. All rights reserved. Blue Coat, the Blue Coat logo, BlueTouch, CacheFlow, CloudSOC, ContentIQ, Elastica, IntelligenceCenter, PacketShaper, Perspecsys, PolicyCenter, ProxyOne, ProxySG, StreamIQ, and WinProxy are registered trademarks or trademarks of Blue Coat Systems, ...
... © 2016 Blue Coat Systems, Inc. All rights reserved. Blue Coat, the Blue Coat logo, BlueTouch, CacheFlow, CloudSOC, ContentIQ, Elastica, IntelligenceCenter, PacketShaper, Perspecsys, PolicyCenter, ProxyOne, ProxySG, StreamIQ, and WinProxy are registered trademarks or trademarks of Blue Coat Systems, ...
CIS 203 Artificial Intelligence
... combines data mining technology with security to more effectively evaluate security threats.” 3) “File and System-based heuristics allow anti-virus solutions to recognize and react to an attack in real time, thus preventing it from infecting the user even when the signature file is not updated. Heur ...
... combines data mining technology with security to more effectively evaluate security threats.” 3) “File and System-based heuristics allow anti-virus solutions to recognize and react to an attack in real time, thus preventing it from infecting the user even when the signature file is not updated. Heur ...
Web Application Security Vulnerabilities Yen
... web applications allow administrators to access the site using a web interface. If these administrative functions are not very carefully protected, an attacker can gain full access to all aspects of a site. ...
... web applications allow administrators to access the site using a web interface. If these administrative functions are not very carefully protected, an attacker can gain full access to all aspects of a site. ...
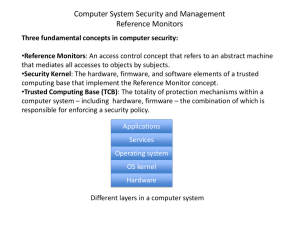
Operating System Security Fundamentals
... Use Secure FTP utility if possible Make two FTP directories: • One for uploads with write permissions only • One for downloads with read permissions only ...
... Use Secure FTP utility if possible Make two FTP directories: • One for uploads with write permissions only • One for downloads with read permissions only ...
Position: Senior IA/Security Specialist, (Computer Network Defense
... robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system administration, analysis, design, implementation, and operation for NAVAIR RDT&E and NMCI/NGEN networks • Recommend solutions as authorized/needed in accordance with cyber ...
... robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system administration, analysis, design, implementation, and operation for NAVAIR RDT&E and NMCI/NGEN networks • Recommend solutions as authorized/needed in accordance with cyber ...
Attivo Networks Deception Platform Integrates with the Check Point
... Attivo Networks® has partnered with Check Point® Software Technologies to deliver a simplified solution for the real-time detection, analysis, and automated blocking of cyber attacks. With this joint solution, customers can use the Attivo ThreatDefend™ Deception and Response Platform to detect infec ...
... Attivo Networks® has partnered with Check Point® Software Technologies to deliver a simplified solution for the real-time detection, analysis, and automated blocking of cyber attacks. With this joint solution, customers can use the Attivo ThreatDefend™ Deception and Response Platform to detect infec ...
Chapter 1: Security Problems in Computing
... assessment, one asks what assets have value and should be protected. In some environments, such as banking there are many objects that have obvious value – big stacks of $100 bills, for example. As we saw in one of the stories above, there were also assets that had great value, although the value wa ...
... assessment, one asks what assets have value and should be protected. In some environments, such as banking there are many objects that have obvious value – big stacks of $100 bills, for example. As we saw in one of the stories above, there were also assets that had great value, although the value wa ...
D1S1_TSV404_Course_Intro_2011_v1
... ■ Intrusion detection must be used to monitor “holes” – If a VPN is used IDS cannot be done at the network perimeter ...
... ■ Intrusion detection must be used to monitor “holes” – If a VPN is used IDS cannot be done at the network perimeter ...
Breaking Trust On The Internet
... • Internet security is a branch of computer security specifically related to the Internet, often involving browser security but also network security on a more general level as it applies to other applications or operating systems on a whole. ...
... • Internet security is a branch of computer security specifically related to the Internet, often involving browser security but also network security on a more general level as it applies to other applications or operating systems on a whole. ...
ch 5 - sm.luth.se
... contains the next instruction to be executed. Stack pointe: Points to the top of the system stack. Status register: Allows the CPU to keep essential ...
... contains the next instruction to be executed. Stack pointe: Points to the top of the system stack. Status register: Allows the CPU to keep essential ...
Document
... Target: Users who primarily utilizes the web Platform: Netbooks License: Open Source (As of Nov 19, 2009) Called Chromium OS Anticipated Release Date: Second half of ...
... Target: Users who primarily utilizes the web Platform: Netbooks License: Open Source (As of Nov 19, 2009) Called Chromium OS Anticipated Release Date: Second half of ...
Breach Detection in Healthcare
... By having a unified view of security-related activity on network devices (IoT), firewalls, servers, desktops and breach detection, RedSocks provides, security operations teams with a much richer and more accurate knowledge base from which to observe, interpret and react to possible threats to the or ...
... By having a unified view of security-related activity on network devices (IoT), firewalls, servers, desktops and breach detection, RedSocks provides, security operations teams with a much richer and more accurate knowledge base from which to observe, interpret and react to possible threats to the or ...
CSC 386 Operating Systems Concepts
... 4. Understand how an operating system provides to user programs an illusion of exclusive access to the hardware, while facilitating collaborations between them. 5. Understand and compare scheduling algorithms designed for various operating system components. 6. Examine some popular scheduling algori ...
... 4. Understand how an operating system provides to user programs an illusion of exclusive access to the hardware, while facilitating collaborations between them. 5. Understand and compare scheduling algorithms designed for various operating system components. 6. Examine some popular scheduling algori ...
Glenbriar TakeStock! - Glenbriar Technologies Inc.
... •Accesses over 35,000 pages of data in real -time ...
... •Accesses over 35,000 pages of data in real -time ...
Security strategy
... documents and computer files. Organisations have a duty to protect the privacy of data which they hold about members of the public and their staff, and to process this data only in the manner for which it was intended. ...
... documents and computer files. Organisations have a duty to protect the privacy of data which they hold about members of the public and their staff, and to process this data only in the manner for which it was intended. ...
Countering Evolving Threats in Distributed Applications
... – Dynamic environment where software gets upgraded, new users are added, new machines are added ...
... – Dynamic environment where software gets upgraded, new users are added, new machines are added ...
billion billion
... As the “GREAT MIGRATION” to cloud begins, Cloud Security as a Service and Cloud Access Security Broker (CASB) products will become more pervasive. ...
... As the “GREAT MIGRATION” to cloud begins, Cloud Security as a Service and Cloud Access Security Broker (CASB) products will become more pervasive. ...