Building an in-depth defense with Vectra and sandbox security
... Command and control Once the exploit is downloaded and activated, it will initiate communication with the command-and-control (C&C) servers that the attacker uses to remotely control each phase of the cyber attack. The attacker uses the C&C servers to send commands to and receive responses from host ...
... Command and control Once the exploit is downloaded and activated, it will initiate communication with the command-and-control (C&C) servers that the attacker uses to remotely control each phase of the cyber attack. The attacker uses the C&C servers to send commands to and receive responses from host ...
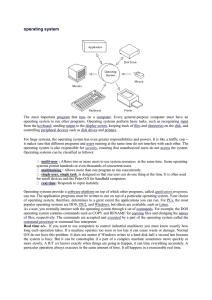
operating system
... The most important program that runs on a computer. Every general-purpose computer must have an operating system to run other programs. Operating systems perform basic tasks, such as recognizing input from the keyboard, sending output to the display screen, keeping track of files and directories on ...
... The most important program that runs on a computer. Every general-purpose computer must have an operating system to run other programs. Operating systems perform basic tasks, such as recognizing input from the keyboard, sending output to the display screen, keeping track of files and directories on ...
MetaOS Concept • MetaOS developed by Ambient Computing to
... • Applies operating system approach to groups of distributed, network-embedded devices • Smart devices and standalone software are abstracted in the same way as resources and peripherals are in traditional operating systems • Supports easy deployment of new services by providing common way to integr ...
... • Applies operating system approach to groups of distributed, network-embedded devices • Smart devices and standalone software are abstracted in the same way as resources and peripherals are in traditional operating systems • Supports easy deployment of new services by providing common way to integr ...
Networking & Security
... DNS (Recursive Domain Name Look-up is possible is getting a map of IP addresses and the services each IP station is running). Open TCP ports can be spidered. Internet Control Message Protocol (ICMP) message types can be changed. Network can be flooded with junk. ...
... DNS (Recursive Domain Name Look-up is possible is getting a map of IP addresses and the services each IP station is running). Open TCP ports can be spidered. Internet Control Message Protocol (ICMP) message types can be changed. Network can be flooded with junk. ...
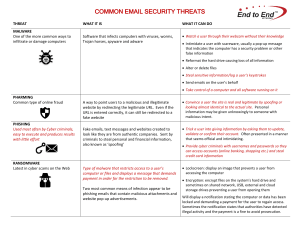
COMMON EMAIL SECURITY THREATS
... Intimidate a user with scareware, usually a pop-up message that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive information/log a user’s keystrokes Send emails on the user ...
... Intimidate a user with scareware, usually a pop-up message that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive information/log a user’s keystrokes Send emails on the user ...
18_DataCenter_Security_Overview
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
18_DataCenter_Security_Overview
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
MALWARE ALERT: PROTECT YOUR BUSINESS AND RAISE
... Generally, yes. Hackers usually seek the path of least resistance: they almost always exploit the human factor. E-mails containing a malware attachment are the most frequent method nowadays, but hackers use a variety of means. For example: ...
... Generally, yes. Hackers usually seek the path of least resistance: they almost always exploit the human factor. E-mails containing a malware attachment are the most frequent method nowadays, but hackers use a variety of means. For example: ...
TrendMicro Titanium - A New Concept in Security by Ira Wilsker
... securely delete files such that they are unrecoverable, and complies with government data security standards. Data Theft Prevention protects sensitive data including credit card numbers, passwords, and email addresses from hackers and spyware, which may attempt to steal such vital personal informati ...
... securely delete files such that they are unrecoverable, and complies with government data security standards. Data Theft Prevention protects sensitive data including credit card numbers, passwords, and email addresses from hackers and spyware, which may attempt to steal such vital personal informati ...
How does it get written up?
... Where’s the vulnerability Why does the problem exist How can it be exploited For an attack or exploit, what sort of damage does it do • Any forensics: logs or other evidence of exploitation ...
... Where’s the vulnerability Why does the problem exist How can it be exploited For an attack or exploit, what sort of damage does it do • Any forensics: logs or other evidence of exploitation ...
Intrusion Detection Prevention Systems
... IDPS technologies was the use of protocol analyzers. • Protocol analyzers can natively decode applicationlayer network protocols, like HTTP or FTP. Once the protocols are fully decoded, the IPS analysis engine can evaluate different parts of the protocol for anomalous behavior or exploits against pr ...
... IDPS technologies was the use of protocol analyzers. • Protocol analyzers can natively decode applicationlayer network protocols, like HTTP or FTP. Once the protocols are fully decoded, the IPS analysis engine can evaluate different parts of the protocol for anomalous behavior or exploits against pr ...
Chapter 14 Network Security - Northern Arizona University
... • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by th ...
... • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by th ...
Chapter 14 Network Security
... • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by th ...
... • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by th ...
Caldicott - Acute Trusts Knowledge base
... media, encrypted transfer, strong access controls and user identification and authentication, and secured wireless networks should all be considered to counter opportunist technical hacking/cracking. It is recommended that ‘two factor’ authentication is used and token-based, biometric, smartcard, et ...
... media, encrypted transfer, strong access controls and user identification and authentication, and secured wireless networks should all be considered to counter opportunist technical hacking/cracking. It is recommended that ‘two factor’ authentication is used and token-based, biometric, smartcard, et ...
Research Scientist – Prague, Czech Republic Cisco Systems
... techniques (statistical analysis, autonomic/agent-based computing, ensemble classification, graph theory, gametheoretic self-optimization) within the framework of distributed, intelligent, and forward-thinking security architecture. Cisco SCO solutions are deployed as an appliance, with an optional ...
... techniques (statistical analysis, autonomic/agent-based computing, ensemble classification, graph theory, gametheoretic self-optimization) within the framework of distributed, intelligent, and forward-thinking security architecture. Cisco SCO solutions are deployed as an appliance, with an optional ...
Internet Vulnerabilities & Criminal Activity
... site may belong to the same attacker Why not go after the author? Prosecution requires: Knowledge Intent Damages & monetary loss ...
... site may belong to the same attacker Why not go after the author? Prosecution requires: Knowledge Intent Damages & monetary loss ...
Web tracking resolution
... Web tracking allows organisations to monitor almost every single aspect of user behaviour on the Web. The type of information that can be collected through tracking (e.g., IP addresses, device identi?iers, etc.) can lead to the identi?ication of a particular ...
... Web tracking allows organisations to monitor almost every single aspect of user behaviour on the Web. The type of information that can be collected through tracking (e.g., IP addresses, device identi?iers, etc.) can lead to the identi?ication of a particular ...
6.01 RCNET Module
... other software runs, or messages between different users of communication software. Malware- Software or firmware intended to perform an unauthorized process that will have adverse impact on the confidentiality, integrity, or availability of an information system. A virus, worm, trojan horse, or oth ...
... other software runs, or messages between different users of communication software. Malware- Software or firmware intended to perform an unauthorized process that will have adverse impact on the confidentiality, integrity, or availability of an information system. A virus, worm, trojan horse, or oth ...
How UTM Solutions Provide the Most Complete
... Adware is a software application which installs itself, often without the user's permission, and displays advertising banners while the program is running. They may appear as pop-up windows or as a bar that appears on a computer screen. It may also change browser properties such as the homepage. Spy ...
... Adware is a software application which installs itself, often without the user's permission, and displays advertising banners while the program is running. They may appear as pop-up windows or as a bar that appears on a computer screen. It may also change browser properties such as the homepage. Spy ...
Shawn Bracken - CISSP103 Chester StMenlo Park, CA 94025
... Supported HP-UX Trusted Systems secure accounting/auditing and kernel configuration Our team was the 3rd layer support known as "backline" which handled the more difficult and time-consuming calls. Most customers were large production systems requiring high uptime. 1997 to 1998, Network Securi ...
... Supported HP-UX Trusted Systems secure accounting/auditing and kernel configuration Our team was the 3rd layer support known as "backline" which handled the more difficult and time-consuming calls. Most customers were large production systems requiring high uptime. 1997 to 1998, Network Securi ...
Survey of online attacks on E-Commerce sites
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
Securing the Network - Austin Community College
... a neighborhood for vulnerable homes, such as an unoccupied residence or a house with an easy-to-open door or window. In many cases, intruders look for vulnerable services that they can exploit later when less likelihood that anyone is looking exists. ...
... a neighborhood for vulnerable homes, such as an unoccupied residence or a house with an easy-to-open door or window. In many cases, intruders look for vulnerable services that they can exploit later when less likelihood that anyone is looking exists. ...
Protecting against spear-phishing
... enterprises invest heavily in, for example, anti-virus solutions – signature-based software to keep out known malware – the ...
... enterprises invest heavily in, for example, anti-virus solutions – signature-based software to keep out known malware – the ...
Chap 3
... Self-contained program that uses security flaws such as buffer overflows to remotely compromise a victim and replicate itself to that system Do not infect other executable programs Account for 80% of all malicious activity on Internet Examples: Code Red, Code Red II, Nimda ...
... Self-contained program that uses security flaws such as buffer overflows to remotely compromise a victim and replicate itself to that system Do not infect other executable programs Account for 80% of all malicious activity on Internet Examples: Code Red, Code Red II, Nimda ...