Physical Security
... and be able to analyze traffic according to protocol, type, amount, source, destination, content, traffic already seen, and other factors. – This analysis must happen quickly, and the NIDS must be able to handle traffic at whatever speed the network operates to be effective. ...
... and be able to analyze traffic according to protocol, type, amount, source, destination, content, traffic already seen, and other factors. – This analysis must happen quickly, and the NIDS must be able to handle traffic at whatever speed the network operates to be effective. ...
conklin_4e_PPT_ch11
... • Most operating systems use the concepts of permissions and rights to control and safeguard access to resources. • Windows operating system provides an example. – Uses the concepts of permissions and rights to control access to files, folders, and information resources – Uses user rights or privile ...
... • Most operating systems use the concepts of permissions and rights to control and safeguard access to resources. • Windows operating system provides an example. – Uses the concepts of permissions and rights to control access to files, folders, and information resources – Uses user rights or privile ...
Guidance on the Use of E-Mail when Sending Person
... External mail systems which are mainly web based email services are generally available for anyone with an internet connection, and are widely used for personal email communication for example Googlemail, Hotmail, Yahoo mail etc. Encryption Encryption is the process of transforming information to ma ...
... External mail systems which are mainly web based email services are generally available for anyone with an internet connection, and are widely used for personal email communication for example Googlemail, Hotmail, Yahoo mail etc. Encryption Encryption is the process of transforming information to ma ...
Era of Spybots - A Secure Design Solution Using
... This paper is presented in the form of a case study. It utilizes a fictitious company, GIAC Enterprises, a growing small retail company whose clients span the nation. In early spring GIACE was compromised with the Spybot worm which caused a business outage. ...
... This paper is presented in the form of a case study. It utilizes a fictitious company, GIAC Enterprises, a growing small retail company whose clients span the nation. In early spring GIACE was compromised with the Spybot worm which caused a business outage. ...
MPT SP2 v2 - Raven Computers Ltd
... download service CDs available on request via the website (no cost) ...
... download service CDs available on request via the website (no cost) ...
Networking in 5-50 Years
... Maturity cost dominates can get any number of bits anywhere, but at considerable cost and complexity casually usable bit density still very low ...
... Maturity cost dominates can get any number of bits anywhere, but at considerable cost and complexity casually usable bit density still very low ...
Document
... data breach incident at Service Providers & Merchants. Compliance is incidental, end objective is security. ...
... data breach incident at Service Providers & Merchants. Compliance is incidental, end objective is security. ...
Data Exfiltration and DNS
... operation (protocols, data formats, etc.).The number of resources (for example mailboxes), the number of locations for resources, and the diversity of such an environment cause formidable problems when we wish to create consistent methods for referencing particular resources that are similar but sca ...
... operation (protocols, data formats, etc.).The number of resources (for example mailboxes), the number of locations for resources, and the diversity of such an environment cause formidable problems when we wish to create consistent methods for referencing particular resources that are similar but sca ...
The Importance of Cybersecurity
... overwhelming workload pressures already on IT/OT personnel, make it difficult for them to address cyber intrusion attempts quickly and appropriately. Moreover, the addition of technologies such as server virtualization, mobile devices (smart phones, tables, laptop computers, etc.), smart grid applic ...
... overwhelming workload pressures already on IT/OT personnel, make it difficult for them to address cyber intrusion attempts quickly and appropriately. Moreover, the addition of technologies such as server virtualization, mobile devices (smart phones, tables, laptop computers, etc.), smart grid applic ...
Lecture Notes - Computer Science & Engineering
... Hutchins et al, Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains, White paper,http://www.lockheedmartin.com/content/dam/lockheed/data/corporate/d ...
... Hutchins et al, Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains, White paper,http://www.lockheedmartin.com/content/dam/lockheed/data/corporate/d ...
3 - Fujitsu
... Private Network. On the Stealth Data Center however, the VPN port of the server process is disabled, and an attacker receives no reply to a port scan, and so also no information on where a point of attack may be located. The current implementation supports the set-up of VPNs (Virtual Private Network ...
... Private Network. On the Stealth Data Center however, the VPN port of the server process is disabled, and an attacker receives no reply to a port scan, and so also no information on where a point of attack may be located. The current implementation supports the set-up of VPNs (Virtual Private Network ...
TELIA YHTEYS KOTIIN MOBIILI SERVICE DESCRIPTION
... block access to network services used for unauthorised distribution of content protected by copyright. Such restrictions may be implemented in such a manner that the user’s access to network addresses will be blocked or that addresses of some network servers will not be transmitted to the service us ...
... block access to network services used for unauthorised distribution of content protected by copyright. Such restrictions may be implemented in such a manner that the user’s access to network addresses will be blocked or that addresses of some network servers will not be transmitted to the service us ...
Forensic Analysis Reveals Data Leaks in HIPAA
... deployed automated password-guessing software to gain access to the Windows server through a Remote Desktop (“RDP”)4 software connection. Once the software successfully determined the password, a hacker manually logged into the server using the RDP connection. The primary server used for managing pa ...
... deployed automated password-guessing software to gain access to the Windows server through a Remote Desktop (“RDP”)4 software connection. Once the software successfully determined the password, a hacker manually logged into the server using the RDP connection. The primary server used for managing pa ...
Mobile Agent Security - Indian Institute of Technology
... A mobile agent is not bound to the system where it begins execution. It has the unique ability to transport itself from one system in a network to another. This submission is primarily concerned with mobile agents. The ability to travel permits a mobile agent to move to a destination agent system th ...
... A mobile agent is not bound to the system where it begins execution. It has the unique ability to transport itself from one system in a network to another. This submission is primarily concerned with mobile agents. The ability to travel permits a mobile agent to move to a destination agent system th ...
Advanced Operating Systems, CSci555
... Base conditions require presentation or availability of credential – Matching the condition brings in additional policy elements. ...
... Base conditions require presentation or availability of credential – Matching the condition brings in additional policy elements. ...
A Stateful Intrustion Detection System for World
... times a failed request originated from a subnet Cookie Stealing Scenario: Records initial use of session cookie by a remote client by mapping cookie to an IP address. ...
... times a failed request originated from a subnet Cookie Stealing Scenario: Records initial use of session cookie by a remote client by mapping cookie to an IP address. ...
Waukesha County Technical College
... You have decided to implement biometrics as part of your security system. Before purchasing a locking system that uses biometrics to control access to secure areas, you need to decide what will be used to authenticate users. What types rely solely on biometric authentication? ...
... You have decided to implement biometrics as part of your security system. Before purchasing a locking system that uses biometrics to control access to secure areas, you need to decide what will be used to authenticate users. What types rely solely on biometric authentication? ...
Methods of Attack
... form of spyware used to record information about an Internet user when they visit websites may be useful or desirable many web sites require that cookies be enabled in order to allow the user to connect ...
... form of spyware used to record information about an Internet user when they visit websites may be useful or desirable many web sites require that cookies be enabled in order to allow the user to connect ...
Securing The Cloud
... Password attack— As its name implies, this attack intends to acquire passwords to important assets so as to cause further damage. Password attacks can be achieved through other methods previously mentioned, such as IP spoofing, or they can be achieved via brute force ...
... Password attack— As its name implies, this attack intends to acquire passwords to important assets so as to cause further damage. Password attacks can be achieved through other methods previously mentioned, such as IP spoofing, or they can be achieved via brute force ...
layered security.
... Legal & Corporate Affairs – Reports to CEO Corporate Services – Technology and ...
... Legal & Corporate Affairs – Reports to CEO Corporate Services – Technology and ...
Final presentation
... The two routed is more difficult to intruders to attack, because he should subvert both of routers to access system. Only application gateway, E-mail server, and information server would be known as system by Internet, no other system name would be known in DNS database, which would be accessible to ...
... The two routed is more difficult to intruders to attack, because he should subvert both of routers to access system. Only application gateway, E-mail server, and information server would be known as system by Internet, no other system name would be known in DNS database, which would be accessible to ...
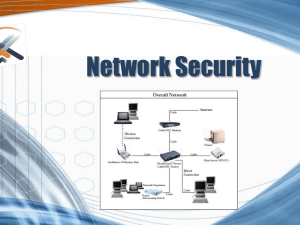
Network Security
... • The goal of access control is to prevent attackers from gaining access, and stops them if they do. • The best way to accomplish this is by: – Determine who needs access to the resources located on the server. – Decide the access permissions for each resource. – Implement specific access control po ...
... • The goal of access control is to prevent attackers from gaining access, and stops them if they do. • The best way to accomplish this is by: – Determine who needs access to the resources located on the server. – Decide the access permissions for each resource. – Implement specific access control po ...
Information Technology (IT) Security Policy
... policies, standards and guidelines is to define the security controls necessary to safeguard HSE information systems and ensure the security, confidentiality, availability and integrity of the information held therein. This policy is mandatory and by accessing any information or Information Technolo ...
... policies, standards and guidelines is to define the security controls necessary to safeguard HSE information systems and ensure the security, confidentiality, availability and integrity of the information held therein. This policy is mandatory and by accessing any information or Information Technolo ...
1. The Threat Environment: Attackers and their Attacks
... ◦ In addition, direct-propagation worms can jump from one computer to another without human intervention on the receiving computer ◦ Computer must have a vulnerability for direct propagation to work ...
... ◦ In addition, direct-propagation worms can jump from one computer to another without human intervention on the receiving computer ◦ Computer must have a vulnerability for direct propagation to work ...