離散對數密碼系統 - 國立交通大學資訊工程學系NCTU Department of
... Algorithms for Discrete Logarithm • Shanks’ algorithm (1972) – Compute L1 = {(i, gmi), i = 0, 1, …, m-1} L2 = {(i, ag-i), i = 0, 1, …, m-1} – where m = ceiling((p-1) ½) Sort L1 and L2 with respect to the 2nd coordinate. – Find the same 2nd coordinate from L1 and L2, say, (q, gmq), (r, ag-r), to get ...
... Algorithms for Discrete Logarithm • Shanks’ algorithm (1972) – Compute L1 = {(i, gmi), i = 0, 1, …, m-1} L2 = {(i, ag-i), i = 0, 1, …, m-1} – where m = ceiling((p-1) ½) Sort L1 and L2 with respect to the 2nd coordinate. – Find the same 2nd coordinate from L1 and L2, say, (q, gmq), (r, ag-r), to get ...
154 kb - Mahopac Central School District
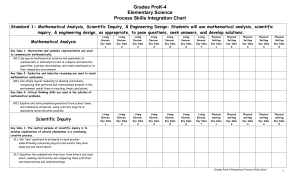
... recognizing that patterns and relationships present in the environment assist them in reaching these conclusions. Key Idea 3: Critical thinking skills are used in the solution of mathematical problems. M3.1 Explore and solve problems generated from school, home, and community situations, using concr ...
... recognizing that patterns and relationships present in the environment assist them in reaching these conclusions. Key Idea 3: Critical thinking skills are used in the solution of mathematical problems. M3.1 Explore and solve problems generated from school, home, and community situations, using concr ...
EE579T-Class 4
... Similar in theory to Enigma. Designed for strategic (fixed station) use; note direct punching of teletypewriter paper tape for transmission. ...
... Similar in theory to Enigma. Designed for strategic (fixed station) use; note direct punching of teletypewriter paper tape for transmission. ...
LifeCare PCA Infusion System With Hospira MedNet Software
... A dose set between the Upper and Lower Soft Limits is in an acceptable range per your facility’s best practices. If a dose is programmed outside of the Upper and Lower Soft Limits, an override alert will appear. Soft Limits can be overridden. The LifeCare PCA® Infusion System with Hospira MedNet® S ...
... A dose set between the Upper and Lower Soft Limits is in an acceptable range per your facility’s best practices. If a dose is programmed outside of the Upper and Lower Soft Limits, an override alert will appear. Soft Limits can be overridden. The LifeCare PCA® Infusion System with Hospira MedNet® S ...
Enriched Pre-Algebra Chapter 4 Test Review Short Answer Each
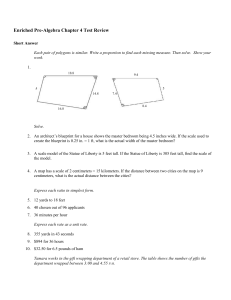
... Write a proportion to determine the missing measure. Round to the nearest tenth, if necessary. 14. The Eiffel Tower in Paris casts a shadow that is about 558.7 feet long. At the same time, a nearby tourist casts a shadow that is 3.4 feet long. If the tourist is 6 feet tall, what is the height of the ...
... Write a proportion to determine the missing measure. Round to the nearest tenth, if necessary. 14. The Eiffel Tower in Paris casts a shadow that is about 558.7 feet long. At the same time, a nearby tourist casts a shadow that is 3.4 feet long. If the tourist is 6 feet tall, what is the height of the ...
21. immobilizer system (hiss)
... • Keep the immobilizer key away from the other vehicle's immobilizer key when using it. The jamming of the key code signal may occur and the proper operation of the system will be obstructed. • The key has built-in electronic part (transponder). Do not drop and strike the key against a hard material ...
... • Keep the immobilizer key away from the other vehicle's immobilizer key when using it. The jamming of the key code signal may occur and the proper operation of the system will be obstructed. • The key has built-in electronic part (transponder). Do not drop and strike the key against a hard material ...
CH10
... – Unique message fingerprint – Good hash algorithm design • Probability of collision is extremely small (two different messages resulting in same hash value) ...
... – Unique message fingerprint – Good hash algorithm design • Probability of collision is extremely small (two different messages resulting in same hash value) ...
FinalNailWEP
... Each IV (initialization vector) produces a different seed different keystream IV = 24 bits therefore 224 different keystreams Possible to know one keystream (IV/Key produced) and transmit everything with it (thus an attacker need only know one keystream to transmit) ...
... Each IV (initialization vector) produces a different seed different keystream IV = 24 bits therefore 224 different keystreams Possible to know one keystream (IV/Key produced) and transmit everything with it (thus an attacker need only know one keystream to transmit) ...
Application research and analysis based on Bitlocker
... password file in the way of document, there are 48 plaintext passwords thatare divided into 8 groups, each group of 6 numbers, you can view and print save. Compared with password, Bitlocker is holding the recovery key, while the corresponding one is the startup key. When necessary, the user can use ...
... password file in the way of document, there are 48 plaintext passwords thatare divided into 8 groups, each group of 6 numbers, you can view and print save. Compared with password, Bitlocker is holding the recovery key, while the corresponding one is the startup key. When necessary, the user can use ...
WWW Tutorial
... autonomously, routing or delivering datagrams without any coordination from the sender. ...
... autonomously, routing or delivering datagrams without any coordination from the sender. ...
SALSA-Concurrency - Computer Science at RPI
... resultActor <- output( token ); Send the find( phrase ) message to each actor in actors[] then after all have completed send the result to resultActor as the argument of an output( … ) message. ...
... resultActor <- output( token ); Send the find( phrase ) message to each actor in actors[] then after all have completed send the result to resultActor as the argument of an output( … ) message. ...
Specificationsfor
... • For multi-tenant residential apartment buildings, Connexus Energy will install a lock box. Property management will provide keys for access to the building and mechanical room where meters are housed. Keys will be placed in the lock box for use by Connexus Energy personnel. When locks are changed ...
... • For multi-tenant residential apartment buildings, Connexus Energy will install a lock box. Property management will provide keys for access to the building and mechanical room where meters are housed. Keys will be placed in the lock box for use by Connexus Energy personnel. When locks are changed ...
Basic First Aid Kit - AFD
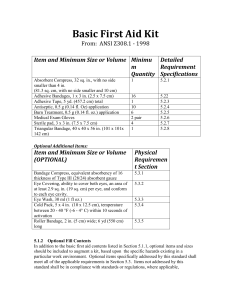
... 5.2.2 Adhesive Bandage. Each adhesive bandage shall consist of non-adherent absorbent pad attached to the central area of a strip of adhesive material. The adhesive strip shall be 3.0 in +/- 1/16 in. (76 mm +/- 1.6 mm) by 1.0 in. +/- 1/32 in. (25.4 mm +/- 0.8 cm). The absorbent pad shall have an are ...
... 5.2.2 Adhesive Bandage. Each adhesive bandage shall consist of non-adherent absorbent pad attached to the central area of a strip of adhesive material. The adhesive strip shall be 3.0 in +/- 1/16 in. (76 mm +/- 1.6 mm) by 1.0 in. +/- 1/32 in. (25.4 mm +/- 0.8 cm). The absorbent pad shall have an are ...
ppt
... • Proof: for any one-way function f: {0,1}n → {0,1}n consider the language Lf : – Consisting of strings of the form {y, b1, b2…bk} – There is an x {0,1}n such that y=f(x) and – The first k bits of x are b1, b2…bk Lf is NP – guess x and check If Lf is P then f is invertible in polynomial time: ...
... • Proof: for any one-way function f: {0,1}n → {0,1}n consider the language Lf : – Consisting of strings of the form {y, b1, b2…bk} – There is an x {0,1}n such that y=f(x) and – The first k bits of x are b1, b2…bk Lf is NP – guess x and check If Lf is P then f is invertible in polynomial time: ...
Rivest-Shamir
... • Now say we want to encrypt message m = 7 • c = Me mod N = 73 mod 33 = 343 mod 33 = 13 – Hence the ciphertext c = 13 ...
... • Now say we want to encrypt message m = 7 • c = Me mod N = 73 mod 33 = 343 mod 33 = 13 – Hence the ciphertext c = 13 ...
Experience Mining Google’s Production Console Logs
... Two-Stage Detection. Message count vectors, however, assume that we have access to all messages about a single identifier at once. This is unrealistic especially in a system that stays up for months. We used frequent pattern mining techniques to segment the long-lasting sequence into subsequences, o ...
... Two-Stage Detection. Message count vectors, however, assume that we have access to all messages about a single identifier at once. This is unrealistic especially in a system that stays up for months. We used frequent pattern mining techniques to segment the long-lasting sequence into subsequences, o ...
A Survey of BGP Security: Issues and Solutions
... Verify Routes Before/After Accepting Them Verify Entire Route/First Hop/Not At All ...
... Verify Routes Before/After Accepting Them Verify Entire Route/First Hop/Not At All ...
Introduction to Information Security Chapter N
... create the ciphertext This can be done at the bit level or at the byte (character) level transposition ciphers move these bits or bytes to another location in the block, so that bit 1 becomes bit 4, bit 2 becomes bit 7 etc ...
... create the ciphertext This can be done at the bit level or at the byte (character) level transposition ciphers move these bits or bytes to another location in the block, so that bit 1 becomes bit 4, bit 2 becomes bit 7 etc ...
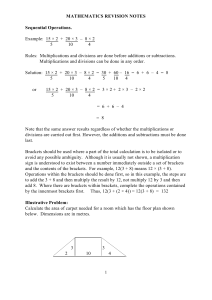
MATHEMATICS REVISION NOTES Sequential Operations. Example
... For numbers where the pre-exponential term is not 1, the pre-exponential term must be shown. Thus 120,000,000 can be written as 120 × 106 or 12 × 107 or as 1.2 × 108 . In scientific notation, the pre-exponential term is usually written as less than 10 so that in this example it would be 1.2 × 108 or ...
... For numbers where the pre-exponential term is not 1, the pre-exponential term must be shown. Thus 120,000,000 can be written as 120 × 106 or 12 × 107 or as 1.2 × 108 . In scientific notation, the pre-exponential term is usually written as less than 10 so that in this example it would be 1.2 × 108 or ...
Cryptanalysis of Shieh-Lin-Yang
... The message m is first signed by an initiator U1, and then is sent separately to all signer. Finally,U1 is responsible for combining these individual signature into a multisignature. ...
... The message m is first signed by an initiator U1, and then is sent separately to all signer. Finally,U1 is responsible for combining these individual signature into a multisignature. ...
Cryptographic hashing - comp
... Consider a message m is split into blocks m1, m2, …, mk without padding and hashed to a value h(m). Choose a message m’ that splits into the block m1, m2, …, mk, mk+1 (the first k blocks are identical to m’s). Therefore, h(m) is the intermediate hash value after k blocks in the computation of h(m’). ...
... Consider a message m is split into blocks m1, m2, …, mk without padding and hashed to a value h(m). Choose a message m’ that splits into the block m1, m2, …, mk, mk+1 (the first k blocks are identical to m’s). Therefore, h(m) is the intermediate hash value after k blocks in the computation of h(m’). ...
Chapter 1 Security Problems in Computing
... Choose a multiplier w and a modulus n, where n > S1 + … + SM and w is relprime to n. Note: Usually n is a prime, which is relprime to any number < n. Example: w = 19 and n = 303. ...
... Choose a multiplier w and a modulus n, where n > S1 + … + SM and w is relprime to n. Note: Usually n is a prime, which is relprime to any number < n. Example: w = 19 and n = 303. ...
Guide to Operating System Security
... encryption permitted by OS Use longest encryption keys possible Inventory encryption and authentication methods used by OS; close any holes Have administrators use personal accounts with administrative privileges (rather than use ...
... encryption permitted by OS Use longest encryption keys possible Inventory encryption and authentication methods used by OS; close any holes Have administrators use personal accounts with administrative privileges (rather than use ...
CIS 5357 - FSU Computer Science
... ciphertext (A,B), but may allow you to decrypt a different ciphertext: – Compute • (A’, B’) = (A, k B) mod p – If you get • m’ = Dec (A’, B’), ...
... ciphertext (A,B), but may allow you to decrypt a different ciphertext: – Compute • (A’, B’) = (A, k B) mod p – If you get • m’ = Dec (A’, B’), ...
IPSec
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
One-time pad
In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked if used correctly. In this technique, a plaintext is paired with a random secret key (also referred to as a one-time pad). Then, each bit or character of the plaintext is encrypted by combining it with the corresponding bit or character from the pad using modular addition. If the key is truly random, is at least as long as the plaintext, is never reused in whole or in part, and is kept completely secret, then the resulting ciphertext will be impossible to decrypt or break. It has also been proven that any cipher with the perfect secrecy property must use keys with effectively the same requirements as OTP keys. However, practical problems have prevented one-time pads from being widely used.First described by Frank Miller in 1882, the one-time pad was re-invented in 1917. On July 22, 1919, U.S. Patent 1,310,719 was issued to Gilbert S. Vernam for the XOR operation used for the encryption of a one-time pad. It is derived from the Vernam cipher, named after Gilbert Vernam, one of its inventors. Vernam's system was a cipher that combined a message with a key read from a punched tape. In its original form, Vernam's system was vulnerable because the key tape was a loop, which was reused whenever the loop made a full cycle. One-time use came later, when Joseph Mauborgne recognized that if the key tape were totally random, then cryptanalysis would be impossible.The ""pad"" part of the name comes from early implementations where the key material was distributed as a pad of paper, so that the top sheet could be easily torn off and destroyed after use. For ease of concealment, the pad was sometimes reduced to such a small size that a powerful magnifying glass was required to use it. The KGB used pads of such size that they could fit in the palm of one's hand, or in a walnut shell. To increase security, one-time pads were sometimes printed onto sheets of highly flammable nitrocellulose, so that they could be quickly burned after use.There is some ambiguity to the term because some authors use the terms ""Vernam cipher"" and ""one-time pad"" synonymously, while others refer to any additive stream cipher as a ""Vernam cipher"", including those based on a cryptographically secure pseudorandom number generator (CSPRNG).