IPsec – An Introduction
... IPsec Negotiation Using IKE IKE negotiates IPsec tunnels between IPsec peers using one of three main methods: 1. Main mode using preshared key authentication followed by quick mode negotiation 2. Main mode using digital signature authentication followed by quick mode negotiation ...
... IPsec Negotiation Using IKE IKE negotiates IPsec tunnels between IPsec peers using one of three main methods: 1. Main mode using preshared key authentication followed by quick mode negotiation 2. Main mode using digital signature authentication followed by quick mode negotiation ...
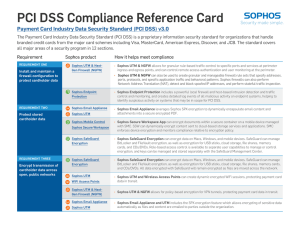
PCI DSS Compliance Reference Card
... PCI DSS Compliance Reference Card Payment Card Industry Data Security Standard (PCI DSS) v3.0 The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, Maste ...
... PCI DSS Compliance Reference Card Payment Card Industry Data Security Standard (PCI DSS) v3.0 The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, Maste ...
Cisco VG200: Cisco IP Telephony Voice Gateway
... only. It is not intended, tested or supported for applications such as H.323 toll bypass or as a SIP GW. The Cisco VG200 Voice-over-IP (VoIP) Gateway is a next-generation voice-conversion device that provides powerful interoperability and advanced features in an affordable package— taking advantage ...
... only. It is not intended, tested or supported for applications such as H.323 toll bypass or as a SIP GW. The Cisco VG200 Voice-over-IP (VoIP) Gateway is a next-generation voice-conversion device that provides powerful interoperability and advanced features in an affordable package— taking advantage ...
TCOM 507 Class 2
... there is no call setup delay which makes them most suited for interactive data applications or high traffic volumes . As such PAMA is used typically to connect high data traffic sites within an organization. SCPC (Single Channel Per Carrier) refers to the usage of a single satellite carrier for carr ...
... there is no call setup delay which makes them most suited for interactive data applications or high traffic volumes . As such PAMA is used typically to connect high data traffic sites within an organization. SCPC (Single Channel Per Carrier) refers to the usage of a single satellite carrier for carr ...
Ingate Firewall & SIParator Training
... Provide SIP Protocol error checking and fixes Protocol non-conformances Routing Rules and Policies to direct traffic Contains extensive list of features devoted to SIP non-conformances ...
... Provide SIP Protocol error checking and fixes Protocol non-conformances Routing Rules and Policies to direct traffic Contains extensive list of features devoted to SIP non-conformances ...
2 Huawei LTE PTT Broadband Trunking Solution
... is also developed from the analog technology to the digital technology and from only having voice services to having voice and data services. The 1G trunking communications network is an analog system that uses FDMA and provides only voice services. The 2G trunking communications network is a digita ...
... is also developed from the analog technology to the digital technology and from only having voice services to having voice and data services. The 1G trunking communications network is an analog system that uses FDMA and provides only voice services. The 2G trunking communications network is a digita ...
Presentation
... Review effects on telephony infrastructure from other device upgrades such as LANs, WANs, voice gateways, and phones Use Cisco® multilevel administration access to provide multiple levels of security to Cisco CallManager administration A project manager and project champion at the senior manag ...
... Review effects on telephony infrastructure from other device upgrades such as LANs, WANs, voice gateways, and phones Use Cisco® multilevel administration access to provide multiple levels of security to Cisco CallManager administration A project manager and project champion at the senior manag ...
Spectrum Rules - ပြည်ထောင်စုသမ္မတမြန်မာနိုင်ငံ
... m) “Effective Date” means the date on which these Rules become legally effective. n) “End User” means a Person, other than an Other Licensee, to whom a Licensee provides a Telecommunications Service. o) “Expiry Date” means the date on which the then-current term of a Licence ends, unless previously ...
... m) “Effective Date” means the date on which these Rules become legally effective. n) “End User” means a Person, other than an Other Licensee, to whom a Licensee provides a Telecommunications Service. o) “Expiry Date” means the date on which the then-current term of a Licence ends, unless previously ...
Cisco AS5300/Voice Gateway
... This feature enables real-time fax transmission between Group III fax machines operating at up to 14,400 bps. The Cisco AS5300/Voice Gateway voice feature card interfaces with the source and target fax machines by appearing to be a fax machine. Real-Time Fax Relay accommodates delays in the networks ...
... This feature enables real-time fax transmission between Group III fax machines operating at up to 14,400 bps. The Cisco AS5300/Voice Gateway voice feature card interfaces with the source and target fax machines by appearing to be a fax machine. Real-Time Fax Relay accommodates delays in the networks ...
J Series Ethernet Radio User Manual
... radiated power (EIRP). Therefore, the sum of the transmitted power (in dBm), the cabling loss and the antenna gain (in dBi) cannot exceed 36 dBm. FCC Point to Point : More EIRP may be allowed for fixed point to point links. With the transmitter set to 27dBm, an antenna gain (subtracting cable loss) ...
... radiated power (EIRP). Therefore, the sum of the transmitted power (in dBm), the cabling loss and the antenna gain (in dBi) cannot exceed 36 dBm. FCC Point to Point : More EIRP may be allowed for fixed point to point links. With the transmitter set to 27dBm, an antenna gain (subtracting cable loss) ...
NeXt generation/dynamic spectrum access/cognitive radio wireless
... Maintaining seamless communication requirements during the transition to better spectrum ...
... Maintaining seamless communication requirements during the transition to better spectrum ...
Communications System Analyzer Change Log
... requirement for calibrated receiver measurements below 10MHz. #4596 Before performing a field calibration, place the product in the Standard FM (Analog) mode of operation. #4906 TETRA constellation display may momentarily show erroneous results after a ‘Reset Averaging’ soft key press. #4950 In gene ...
... requirement for calibrated receiver measurements below 10MHz. #4596 Before performing a field calibration, place the product in the Standard FM (Analog) mode of operation. #4906 TETRA constellation display may momentarily show erroneous results after a ‘Reset Averaging’ soft key press. #4950 In gene ...
Recent Advances in 3GPP Rel-12
... Technical Reports (TRs) and Technical Specifications (TSs) on evolution of existing radio technologies or new radio technologies defined by 3GPP, such as HSPA/HSPA+, LTE and LTE-Advanced (LTE-A). 3GPP specifications are grouped into "Releases", and a mobile system can be implemented based on the set ...
... Technical Reports (TRs) and Technical Specifications (TSs) on evolution of existing radio technologies or new radio technologies defined by 3GPP, such as HSPA/HSPA+, LTE and LTE-Advanced (LTE-A). 3GPP specifications are grouped into "Releases", and a mobile system can be implemented based on the set ...
Mobile Broadband Wireless Access Systems (IEEE 802.20. TDD
... to the effect that the rights listed in Attachment 1 and 2, which are the Industrial Property Rights relating to this standard, are held by the parties also listed therein, and that to the users of this standard, in the case of Attachment 1 (selection of option 1), such holders shall not assert any ...
... to the effect that the rights listed in Attachment 1 and 2, which are the Industrial Property Rights relating to this standard, are held by the parties also listed therein, and that to the users of this standard, in the case of Attachment 1 (selection of option 1), such holders shall not assert any ...
WWG Draft Green Book v0.117 - ccsds cwe
... British National Space Centre (BNSC)/United Kingdom. ...
... British National Space Centre (BNSC)/United Kingdom. ...
Integrated Voice and Data Network
... Project 25 is a Standard developed by APCO (Association of Public Safety Communications Officials) primarily for the North American market. The Standard defines the Trunking and Common Air Interface (CAI) parameters for public safety systems, allowing competing manufacturers to offer interoperabilit ...
... Project 25 is a Standard developed by APCO (Association of Public Safety Communications Officials) primarily for the North American market. The Standard defines the Trunking and Common Air Interface (CAI) parameters for public safety systems, allowing competing manufacturers to offer interoperabilit ...
annex ii + iii: technical specifications + technical offer
... Terrestrial Trunked Radio (TETRA) is a digital trunked mobile radio standard developed by the European Telecommunications Standards Institute (ETSI). The purpose of the TETRA standard was to meet the needs of traditional Professional Mobile Radio (PMR) user organizations such as Public Safety, Trans ...
... Terrestrial Trunked Radio (TETRA) is a digital trunked mobile radio standard developed by the European Telecommunications Standards Institute (ETSI). The purpose of the TETRA standard was to meet the needs of traditional Professional Mobile Radio (PMR) user organizations such as Public Safety, Trans ...
MANET and TETRA, competing or supplementing technologies for
... – DM Dual Watch – Equipment can operate in DMO or TMO and receive incoming calls on the other mode ...
... – DM Dual Watch – Equipment can operate in DMO or TMO and receive incoming calls on the other mode ...
See the slides
... task in the process of chaotic encryption is to synchronize the transmitter and the receiver. Two ways to achieve this synchronization would be 1. Use two- transmission channel system :Here we have two separate channels, one to carry the encrypted signal and the other to carry the chaotic carrier wa ...
... task in the process of chaotic encryption is to synchronize the transmitter and the receiver. Two ways to achieve this synchronization would be 1. Use two- transmission channel system :Here we have two separate channels, one to carry the encrypted signal and the other to carry the chaotic carrier wa ...
SIP Trunking - Whitepaper
... have significantly come down in the recent years, they are still a significant source of expenses for multinational companies. With SIP trunking and least cost routing, these costs are significantly reduced. In addition, SIP trunking opens up new avenues for conferencing and collaboration b. Reduced ...
... have significantly come down in the recent years, they are still a significant source of expenses for multinational companies. With SIP trunking and least cost routing, these costs are significantly reduced. In addition, SIP trunking opens up new avenues for conferencing and collaboration b. Reduced ...
SSH - Information Services and Technology
... IP and TCP Attacks: SSH operates on top of TCP, therefore some of its weaknesses come from TCP/IP problems. of the SSH connection. ...
... IP and TCP Attacks: SSH operates on top of TCP, therefore some of its weaknesses come from TCP/IP problems. of the SSH connection. ...
Frequency Modulation
... Broadband transmission = • In general, broadband refers to telecommunication in which a wide band of frequencies is available to transmit information. • Because a wide band of frequencies is available, information can be multiplexed and sent on many different frequencies or channels within the band ...
... Broadband transmission = • In general, broadband refers to telecommunication in which a wide band of frequencies is available to transmit information. • Because a wide band of frequencies is available, information can be multiplexed and sent on many different frequencies or channels within the band ...
CableTesting - vspclil
... Since current Ethernet technology supports data rates of billions of bits per second, each bit must be recognized, even though duration of the bit is very small. The voltage level cannot be amplified at the receiver, nor can the bit duration be extended in order to recognize the data. This means tha ...
... Since current Ethernet technology supports data rates of billions of bits per second, each bit must be recognized, even though duration of the bit is very small. The voltage level cannot be amplified at the receiver, nor can the bit duration be extended in order to recognize the data. This means tha ...