* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Agenda
Deep packet inspection wikipedia , lookup
Trusted Computing wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Cryptography wikipedia , lookup
Web of trust wikipedia , lookup
Authentication wikipedia , lookup
Access control wikipedia , lookup
Proxy server wikipedia , lookup
Certificate authority wikipedia , lookup
Mobile security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Computer security wikipedia , lookup
Unix security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
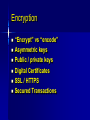
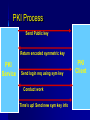
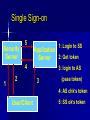
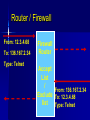
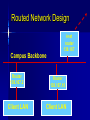
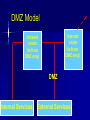
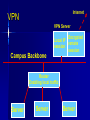
Class 6 Agenda Midterm Review – Questions – Toyota Case Computer Security Basics – Identification & Authentication – SSL encryption and Internet security – Network Security Text Chapter : Strategy & Technology Computer Security Basics Access Control – Identification – Authentication – Permissions/Access Issues Role-based access “Row-level” access Mechanisms Directories Groups, attributes Logs Encryption “Encrypt” vs “encode” Asymmetric keys Public / private keys Digital Certificates SSL / HTTPS Secured Transactions PKI Process Send Public key Return encoded symmetric key PKI Service Send login req using sym key Conduct work Time’s up! Send new sym key info PKI Client Network Security Basics Single sign-on – Trusted machine model – Tokens Firewalls – Routers as firewalls – True firewalls “Castles and Roads” Virtual Private Network DMZ – 2-router model Single Sign-on Security Server 5 1: Login to SS Application 2: Get token Server 4 1 2 3: login to AS 3 (pass token) 4: AS chk’s token User/Client 5: SS ok’s token Router / Firewall From: 12.3.4.68 To: 136.167.2.34 Type: Telnet Firewall Router Accept List / From: 136.167.2.34 Exclude To: 12.3.4.68 list Type: Telnet Routed Network Design I-net router 136.167 Campus Backbone Router 136.167.2 Client LAN Router 136.167.10 Client LAN DMZ Model Internet router (to/from DMZ only) Intranet router (to/from DMZ only) DMZ Internal Services External Services VPN / Remote Access Goals – Privacy – IP address domains VPN Mechanism – Proxy server – “Tunneling” VPN Problems – Encryption performance Internet VPN VPN Server Encrypted Local IP session remote session Campus Backbone Router Enabling local traffic Server Server Server Text: Strategy & Technology “IT doesn’t matter!” Comments? What makes sustainable advantage? What technical aspects (ref class 1) effect sustainable advantage? How important is the “portal” factor? Wednesday Computer Center Tour – Meet at 197 Foster St @ 6:30 Tech Brief: Collaboration Basics Text Chapter: Peer Production Project Planning time – (Outline due to me by COB Friday)