Technical Presentation
... A SIP Trunk is a concurrent call that is routed over the IP backbone of a carrier (ITSP) using VoIP technology. ...
... A SIP Trunk is a concurrent call that is routed over the IP backbone of a carrier (ITSP) using VoIP technology. ...
Ingate Firewall & SIParator Training
... A SIP Trunk is a concurrent call that is routed over the IP backbone of a carrier (ITSP) using VoIP technology. ...
... A SIP Trunk is a concurrent call that is routed over the IP backbone of a carrier (ITSP) using VoIP technology. ...
A Secure Way to Protect Your Network: IBM
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 1999. All rights reserved. Note to U.S Government Users - Doc ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 1999. All rights reserved. Note to U.S Government Users - Doc ...
DNS Security Considerations and the Alternatives to BIND
... The entire Internet depends on Domain Name System (DNS). Without DNS, the Internet users cannot access the Internet without resolving all the hostname into IP address while at the same time other external networks also cannot access your public servers. If the web server becomes inaccessible, people ...
... The entire Internet depends on Domain Name System (DNS). Without DNS, the Internet users cannot access the Internet without resolving all the hostname into IP address while at the same time other external networks also cannot access your public servers. If the web server becomes inaccessible, people ...
RADIUS Implementation and Deployment Best Practices
... (OTP), MD5-Challenge, Transport Level Security (TLS) for smart card and certificate support, as well as any future authentication technologies. EAP is a critical technology component for secure connections. In addition to support within PPP, EAP is also supported within the IEEE 802 link layer. IEEE ...
... (OTP), MD5-Challenge, Transport Level Security (TLS) for smart card and certificate support, as well as any future authentication technologies. EAP is a critical technology component for secure connections. In addition to support within PPP, EAP is also supported within the IEEE 802 link layer. IEEE ...
LISP Proxy Tunnel Router Redundancy Deployment July 23, 2012
... After creating a LISP map-cache entry, when the PITR receives EID-destined packets, it checks the LISP map-cache first. If there is a valid entry, it will be used for encapsulating the packet and then forwarded to the ETR. ...
... After creating a LISP map-cache entry, when the PITR receives EID-destined packets, it checks the LISP map-cache first. If there is a valid entry, it will be used for encapsulating the packet and then forwarded to the ETR. ...
Chapter 18 Networking
... The InetAddress Class Occasionally, you would like to know who is connecting to the server.You can use the InetAddress class to find the client's host name and IP address. The InetAddress class models an IP address.You can use the statement shown below to create an instance of InetAddress for the c ...
... The InetAddress Class Occasionally, you would like to know who is connecting to the server.You can use the InetAddress class to find the client's host name and IP address. The InetAddress class models an IP address.You can use the statement shown below to create an instance of InetAddress for the c ...
What do I do?
... • Expand infrastructure capabilities to address new markets Cisco based carriers can easily add new protocol capabilities to the core network, simultaneously supporting both H.323 and SIP on the Cisco gateways ...
... • Expand infrastructure capabilities to address new markets Cisco based carriers can easily add new protocol capabilities to the core network, simultaneously supporting both H.323 and SIP on the Cisco gateways ...
Firewalls - Andrew.cmu.edu - Carnegie Mellon University
... Gateways and Proxies These are paths through your firewall to allow services Proxies are intermediaries that regulate service through the firewall Application gateways and proxies allow specific application interfaces through the firewall Encryption is the bane of gateways and ...
... Gateways and Proxies These are paths through your firewall to allow services Proxies are intermediaries that regulate service through the firewall Application gateways and proxies allow specific application interfaces through the firewall Encryption is the bane of gateways and ...
Sohel Ahmed Syed Flat #402, Shivshankar 2, Contact Number: +91
... dependencies in configuring Windows AD SSO. Deploy the solution in Sandbox environment and present POC. Implemented Test and Production and DR BI4.1 SP04 environment clustered and distributed on Windows 2008 R2 with MSSQL as the reporting and CMS databases, Tomcat as the web application server, F5 l ...
... dependencies in configuring Windows AD SSO. Deploy the solution in Sandbox environment and present POC. Implemented Test and Production and DR BI4.1 SP04 environment clustered and distributed on Windows 2008 R2 with MSSQL as the reporting and CMS databases, Tomcat as the web application server, F5 l ...
Organizations That Use TLS/SSL
... For organizations that store or process payment information, such as donor credit card numbers, implementing TLS/SSL may be a requirement of the Payment Card Industry Data Security Standard (PCI DSS). This standard was created by the PCI Security Standards Council, a group of several major payment c ...
... For organizations that store or process payment information, such as donor credit card numbers, implementing TLS/SSL may be a requirement of the Payment Card Industry Data Security Standard (PCI DSS). This standard was created by the PCI Security Standards Council, a group of several major payment c ...
How to Install and Configure Patch Manager 2.0?
... With SolarWinds Patch Manager, you can easily discover systems that are not running the latest updates, and you can patch them accordingly. Once you deploy the update, you can run reports to check how successful your patching was and if there still any vulnerable computers and applications on the n ...
... With SolarWinds Patch Manager, you can easily discover systems that are not running the latest updates, and you can patch them accordingly. Once you deploy the update, you can run reports to check how successful your patching was and if there still any vulnerable computers and applications on the n ...
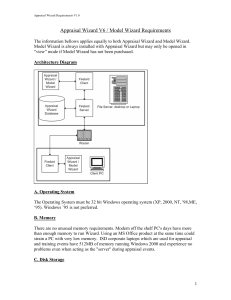
Appraisal Wizard Requirements
... The processor should be at least a Pentium. Faster is always better, but certainly a 400 MHZ Pentium or better will provide acceptable response. If the PC is also acting as a server for other Appraisal Wizard clients, this could become a factor in performance so a higher processor speed is recommend ...
... The processor should be at least a Pentium. Faster is always better, but certainly a 400 MHZ Pentium or better will provide acceptable response. If the PC is also acting as a server for other Appraisal Wizard clients, this could become a factor in performance so a higher processor speed is recommend ...
PDF
... path to the endpoint. An example is a video-on-demand flow from a video server to a set-top box, which is a computer that acts as a receiver and decodes the incoming video signal from the video server. Because set-top boxes may not support RSVP natively, you cannot configure end-to-end RSVP reservat ...
... path to the endpoint. An example is a video-on-demand flow from a video server to a set-top box, which is a computer that acts as a receiver and decodes the incoming video signal from the video server. Because set-top boxes may not support RSVP natively, you cannot configure end-to-end RSVP reservat ...
Acceptable Use Policy
... Delaware limited liability company (“ETAN”) services, and to promote the security and availability of ETAN’s network and computing infrastructure to its clients ("Clients") and third parties. This AUP applies to each Client's use of ETAN Services ("Services") and ETAN infrastructure (Servers) that i ...
... Delaware limited liability company (“ETAN”) services, and to promote the security and availability of ETAN’s network and computing infrastructure to its clients ("Clients") and third parties. This AUP applies to each Client's use of ETAN Services ("Services") and ETAN infrastructure (Servers) that i ...
3 - Fujitsu
... On the other hand, authorised users for which a connection is provided can establish a link as usual – such as to a web service or via a Virtual Private Network. On the Stealth Data Center however, the VPN port of the server process is disabled, and an attacker receives no reply to a port scan, and ...
... On the other hand, authorised users for which a connection is provided can establish a link as usual – such as to a web service or via a Virtual Private Network. On the Stealth Data Center however, the VPN port of the server process is disabled, and an attacker receives no reply to a port scan, and ...
Chapter 4
... A user may change the network address of a w/s and may make it look as another w/s A user may eavesdrop on a session and mount a replay attack later ...
... A user may change the network address of a w/s and may make it look as another w/s A user may eavesdrop on a session and mount a replay attack later ...
The Inexact Science of Internet Filtering for the K
... for that matter). Start blocking uncategorized URLs (or preferably all URLs not explicitly allowed), allow the “very safe” categories and supplement with your URL whitelists. “Very safe” == Education, Kid’s Sites, etc. Many other categories are borderline for wholesale allowing, e.g. Blogs & Forums, ...
... for that matter). Start blocking uncategorized URLs (or preferably all URLs not explicitly allowed), allow the “very safe” categories and supplement with your URL whitelists. “Very safe” == Education, Kid’s Sites, etc. Many other categories are borderline for wholesale allowing, e.g. Blogs & Forums, ...
CompTIA Network + - We Provide Solutions
... incoming and outgoing data traffic. Firewall security can be configured in any number of ways including packet filtering (scanning data packets as they come in), and permitting or denying access based on the originating Internet Protocol address or IP address. Sérgio de Sá – [email protected] ...
... incoming and outgoing data traffic. Firewall security can be configured in any number of ways including packet filtering (scanning data packets as they come in), and permitting or denying access based on the originating Internet Protocol address or IP address. Sérgio de Sá – [email protected] ...
3_firewall_m
... – incoming packet from 131.34.0.0 are blocked – incoming packet destined for any internal TELNET (port 23) are blocked – incoming packets destined to internal host 194.78.20.8 are blocked (this host for internal use) – outgoing packets destined for an HTTP server (port 80) are blocked. (i.e. does no ...
... – incoming packet from 131.34.0.0 are blocked – incoming packet destined for any internal TELNET (port 23) are blocked – incoming packets destined to internal host 194.78.20.8 are blocked (this host for internal use) – outgoing packets destined for an HTTP server (port 80) are blocked. (i.e. does no ...
Final presentation
... Only application gateway, E-mail server, and information server would be known as system by Internet, no other system name would be known in DNS database, which would be accessible to outside systems. Application gateway can use authentication software to authenticate all inbound connection. More fl ...
... Only application gateway, E-mail server, and information server would be known as system by Internet, no other system name would be known in DNS database, which would be accessible to outside systems. Application gateway can use authentication software to authenticate all inbound connection. More fl ...
lecture-7
... Translation of a domain name into an equivalent IP address is called name resolution and it is the main purpose of the DNS protocol . A host asking for DNS name resolution is called a resolver. if the requested host name is contained by the name server’s database , the server is said to be an author ...
... Translation of a domain name into an equivalent IP address is called name resolution and it is the main purpose of the DNS protocol . A host asking for DNS name resolution is called a resolver. if the requested host name is contained by the name server’s database , the server is said to be an author ...
5. Detailed working of RADIUS - Department of Computer Science
... 5. Detailed working of RADIUS Authentication and Authorization: Any user of a RADIUS configured client should present authentication information (for example, username and password). The client creates an Access-Request frame containing the username, password, ID of the client and the port ID that t ...
... 5. Detailed working of RADIUS Authentication and Authorization: Any user of a RADIUS configured client should present authentication information (for example, username and password). The client creates an Access-Request frame containing the username, password, ID of the client and the port ID that t ...
Application level gateway Firewalls - Mercer University
... Application level firewalls decide whether to drop a packet or send them through based on the application information. They do this by setting up various proxies on a single firewall for different applications. Both the client and the server connect to these proxies instead of connecting directly t ...
... Application level firewalls decide whether to drop a packet or send them through based on the application information. They do this by setting up various proxies on a single firewall for different applications. Both the client and the server connect to these proxies instead of connecting directly t ...
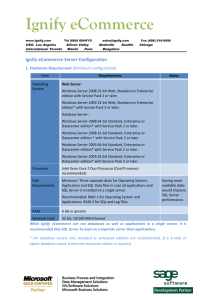
Ignify eCommerce Server Configuration
... Multiple Servers hosting front in Intranet. store should be configured as a Database would be in intranet. load balanced cluster. Configure firewall separating DMZ from intranet to allow SQL Manager and Services should Traffic (Port - 1433 usually) from be mapped to a single IP store application ser ...
... Multiple Servers hosting front in Intranet. store should be configured as a Database would be in intranet. load balanced cluster. Configure firewall separating DMZ from intranet to allow SQL Manager and Services should Traffic (Port - 1433 usually) from be mapped to a single IP store application ser ...
Proxy server
In computer networks, a proxy server is a server (a computer system or an application) that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource available from a different server and the proxy server evaluates the request as a way to simplify and control its complexity. Proxies were invented to add structure and encapsulation to distributed systems. Today, most proxies are web proxies, facilitating access to content on the World Wide Web and providing anonymity.