* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download lecture-7
Survey
Document related concepts
Transcript
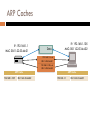
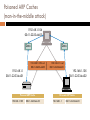
MAN-IN-THE-MIDDLE ATTACK STEGANOGRAPHY Lab#7 MAC Addresses and ARP 32-bit IP address: network-layer address used to get datagram to destination IP subnet MAC (or LAN or physical or Ethernet) address: Data link layer address used to get datagram from one interface to another physically-connected interface (same network) 48 bit MAC address (for most LANs) burned in the adapter ROM Some Network interface cards (NICs) can change their MAC 5-2 ARP: Address Resolution Protocol Question: how to determine MAC address of host B when knowing B’s IP address? 237.196.7.78 1A-2F-BB-76-09-AD 237.196.7.23 237.196.7.14 237.196.7.88 < IP address; MAC address; TTL> LAN 71-65-F7-2B-08-53 Each IP node (Host, Router) on LAN has ARP table ARP Table: IP/MAC address mappings for some LAN nodes 58-23-D7-FA-20-B0 0C-C4-11-6F-E3-98 TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min) 5-3 ARP ARP works by broadcasting requests and caching responses for future use The protocol begins with a computer broadcasting a message of the form who has <IP address1> tell <IP address2> When the machine with <IP address1> or an ARP server receives this message, its broadcasts the response <IP address1> is <MAC address> The requestor’s IP address <IP address2> is contained in the link header The Linux and Windows command arp - a displays the ARP table Internet Address Physical Address Type 128.148.31.1 00-00-0c-07-ac-00 dynamic 128.148.31.15 00-0c-76-b2-d7-1d dynamic 128.148.31.71 00-0c-76-b2-d0-d2 dynamic 128.148.31.75 00-0c-76-b2-d7-1d dynamic 128.148.31.102 00-22-0c-a3-e4-00 dynamic 128.148.31.137 00-1d-92-b6-f1-a9 dynamic ARP Spoofing The ARP table is updated whenever an ARP response is received Requests are not tracked ARP announcements are not authenticated Machines trust each other A rogue machine can spoof other machines ARP Poisoning (ARP Spoofing) According to the standard, almost all ARP implementations are stateless An arp cache updates every time that it receives an arp reply… even if it did not send any arp request! It is possible to “poison” an arp cache by sending gratuitous arp replies ARP Caches IP: 192.168.1.1 MAC: 00:11:22:33:44:01 Data IP: 192.168.1.105 MAC: 00:11:22:33:44:02 192.168.1.1 is at 00:11:22:33:44:01 192.168.1.105 is at 00:11:22:33:44:02 ARP Cache 192.168.1.105 00:11:22:33:44:02 ARP Cache 192.168.1.1 00:11:22:33:44:01 Poisoned ARP Caches (man-in-the-middle attack) 192.168.1.106 00:11:22:33:44:03 Data 192.168.1.105 is at 00:11:22:33:44:03 Data 192.168.1.1 is at 00:11:22:33:44:03 192.168.1.1 00:11:22:33:44:01 192.168.1.105 00:11:22:33:44:02 Poisoned ARP Cache 192.168.1.105 00:11:22:33:44:03 Poisoned ARP Cache 192.168.1.1 00:11:22:33:44:03 ARP Spoofing Using static entries solves the problem but it is almost impossible to manage! Check multiple occurrence of the same MAC i.e., One MAC mapping to multiple IP addresses (see previous slide’s example) Software detection solutions Anti-arpspoof, Xarp, Arpwatch Ettercap Ettercap is a freely available program that can be used to exploit the weakness of the ARP protocol. While it can be used by attackers to launch MITM attacks, it can also be used to monitor the network and detect if there are poisoners on the network. Lab objectives At the end of this lab, you’ll be able to Define ARP poisoning and man-in-the-middle attacks. Explain how Ettercap can be used to execute an MITM attack. Describe the attack signature of an MITM attack. Steganography Steganography The term steganography comes from the Greek word steganos, which means “hidden” or “covered.” Steganography is the hiding of information. Unlike cryptography, the information is not scrambled or encoded—it is simply hidden. On a computer system, steganography will hide one file inside another. Most often a text file will be hidden in an image or an MP3 file. This ability to hide information, sometimes in plain sight, poses a significant threat to the confidentiality of information. In this lab, you will create a text file with sensitive information and hide it in an image file, and then post it to a web site. Lab objectives Explain what steganography is. Describe the process of hiding information. DNS Spoofing Domain names The existing internet domain name space , however, is a structural system divided into seven top-level domains: Com: commercial organizations. Edu: Educational organizations. Gov : Government organizations Mil : Military organizations Net : Networking organizations Org : noncommercial organizations Domain zones The domain name space structure is said to be similar to a tree , as the top level domains are divided into other sub-domains each domain consists of several zones Name servers generally have complete information about some part of the domain name space, called a zone, which they load from a file or from another name server. The name server is then said to have authority for that zone. Domain names and zones DNS Translation of a domain name into an equivalent IP address is called name resolution and it is the main purpose of the DNS protocol . A host asking for DNS name resolution is called a resolver. if the requested host name is contained by the name server’s database , the server is said to be an authority for that host. When an incoming request specifies a name for which a server is an authority , the server answers the request directly by looking for the name in its local database . Recursive vs. iterative if the name was out of the server authority two approaches are used to dealing with this problem . ‘recursive’ in which the server pursues the query for the client at another server , ‘iterative’ in which the server refers the client to another server and let the client pursue the query. Type Each question has a query type and a query ID , and each response has an answer type. The most common query type is an A type . which names that an IP address is desired for the requeried name? The NS name is made to find out the authoritive name server for a domain. AXFR type request from the secondary DNS to a primary to update the secondary database . DNS Caching Caching is expected to improve the overall responsiveness of the system by ensuring that answers to questions are known and stored locally and that the query load placed on the authoritative servers is minimized. So the next time you are requesting the same domain.com address, it instantly returns the answer, without having to contact your ISP's DNS server to ask it for the translation DNS Forwarding Forwarding Even a caching name server does not necessarily perform the complete recursive lookup itself , Instead it can forward some or all of the queries that are cannot satisfy from its cache to another caching name server , commonly referred to as a forwarde http://williams.comp.ncat.edu/IA_visualization_labs/security_visual_tools/SYNFloodDemo/SFattack.swf http://williams.comp.ncat.edu/IA_visualization_labs/security_visual_tools/SYNFloodDemo/Prevent.swf http://williams.comp.ncat.edu/IA_visualization_labs/security_visual_tools/SYNFloodDemo/Mainmenu.swf http://williams.comp.ncat.edu/IA_visualization_labs/security_visual_tools/packet_sniffer/packet_sniffer_de mo.html http://scisweb.ulster.ac.uk/~kevin/com320/labs/wireshark/lab-DNS.pdf http://users.ece.gatech.edu/owen/Academic/ECE4112/Spring2004/lab3.pdf http://www.dev-point.com/vb/t302098.html http://www.cisco.com/c/dam/en/us/products/collateral/interfaces-modules/servicesmodules/prod_presentation0900aecd805c756c.pdf http://www.macs.hw.ac.uk/~hwloidl/Courses/F21CN/Labs/CryptoI/Crypto_Encryption.pdf http://blog.pluralsight.com/videos/ethical-hacking-how-to-create-a-dos-attack