* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Implementing Security for Electronic Commerce
Cross-site scripting wikipedia , lookup
Security-focused operating system wikipedia , lookup
Unix security wikipedia , lookup
Quantum key distribution wikipedia , lookup
Computer security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Trusted Computing wikipedia , lookup
Grill (cryptology) wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Cryptographic hash function wikipedia , lookup
Cryptanalysis wikipedia , lookup
One-time pad wikipedia , lookup
Public-key cryptography wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Mobile security wikipedia , lookup
Diffie–Hellman key exchange wikipedia , lookup
Cryptography wikipedia , lookup
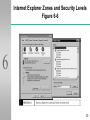
Post-quantum cryptography wikipedia , lookup
Digital signature wikipedia , lookup
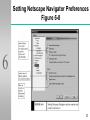
Web of trust wikipedia , lookup
Chapter 6 6 Implementing Security for Electronic Commerce Electronic Commerce 1 Objectives Security 6 measures that can reduce or eliminate intellectual property theft Securing client computers from attack by viruses and by ill-intentioned programs and scripts downloaded in Web pages Authenticate users to servers and authenticate servers 2 Objectives Available 6 protection mechanisms to secure information sent between a client and a server Message integrity security, preventing another program from altering information as it travels across the Internet 3 Objectives Safeguards 6 that are available so commerce servers can authenticate users Protecting intranets with firewalls and corporate servers against being attacked through the Internet The role Secure Socket Layer, Secure HTTP and secure electronic transaction protocols play in protecting e-commerce 4 Minimum Requirements for Secure Electronic Commerce 6 5 Protecting Intellectual Property The 6 dilemma for digital property is how to display and make available intellectual property on the Web while protecting those copyrighted works Intellectual Property Protection in Cyberspace recommends: Host name blocking Packet filtering Proxy servers 6 Companies Providing Intellectual Property Protection Software ARIS 6 Technologies Digital audio watermarking systems Embedded code in audio file uniquely identifying the intellectual property Digimarc Corporation Watermarking for various file formats Controls software and playback devices 7 Companies Providing Intellectual Property Protection Software SoftLock Services Allows authors and publishers to lock files containing digital information for sale on the Web Posts files to the Web that must be unlocked with a purchased ‘key’ before viewing 6 8 Protecting Client Computers Active 6 content, delivered over the Internet in dynamic Web pages, can be one of the most serious threats to client computers Threats can hide in Web pages Downloaded graphics and plug-ins E-mail attachments 9 Protecting Client Computers Cookies 6 Small pieces of text stored on your computer and contain sensitive information that is not encrypted Anyone can read and interpret cookie data Do not harm client machines directly, but potentially could still cause damage Misplaced trust Web sites that aren’t really what they seem and trick the user into revealing sensitive data 10 Monitoring Active Content Netscape 6 Navigator and Microsoft Internet Explorer browsers are equipped to allow the user to monitor active content before allowing it to download Digital certificates provide assurance to clients and servers that the participant is authenticated 11 Digital Certificates Also 6 known as a digital ID Is an attachment to an e-mail message or a program embedded in a Web page It serves as a proof that the holder is the person or company identified by the certificate A means to send encrypted message encoded, so that others cannot read or duplicate it 12 Digital Certificates 6 IN case of downloaded software containing a digital ID, it identifies the software publisher, i.e., it assures that the holder of the software is a trusted name. A certification authority (CA) issues a digital certificate to an organization or an individual when provided with required information. A certificate authority also signs the certificate in the form of a public encrypted key, which unlocks the certificate for anyone who receives the certificate attached to the publisher’s code. CA guarantees the authenticity of the organization or individual. 13 Digital Certificates Key: A key is simply a number - a long binary number (1s and 0s) - which is used with the encryption algorithm to “lock” the characters of the message that is to be protected. Longer keys provide significantly better protection than shorter keys. 6 14 VeriSign -- A Certification Authority 6 15 VeriSign 6 Is the Oldest and best-known Certification Authority (CA) Offers several classes of certificates Class 1 (lowest level) Bind e-mail address and associated public keys Class 2 Issued by an organization such as a bank to identify its customers. The certificate is still issued by a CA. Class 4 (highest level) Apply to servers and their organizations Offers assurance of an individual’s identity and relationship to a specified organization 16 Structure of a VeriSign Certificate Figure 6-4 6 17 Microsoft Internet Explorer Provides 6 client-side protection right inside the browser Reacts to ActiveX and Java-based content Authenticode verifies the identity of downloaded content The user decides to ‘trust’ code from individual companies 18 Security Warning and Certificate Validation Figure 6-5 6 19 Internet Explorer Zones and Security Levels Figure 6-6 6 20 Internet Explorer Security Zone Default Settings Figure 6-7 6 21 Netscape Navigator User 6 can decide to allow Navigator to download active content User can view the signature attached to Java and JavaSript Security is set in the Preferences dialog box Cookie options are also set in the Preferences dialog box 22 Setting Netscape Navigator Preferences Figure 6-8 6 23 A Typical Netscape Navigator Java Security Alert Figure 6-9 6 24 Viewing a Content Provider’s Certificate Figure 6-10 6 25 Dealing with Cookies Can 6 be set to expire within 10, 20, or 30 days Retrievable only by the site that created them Collect information so that the user doesn’t have to continually enter usernames and passwords to access Web sites 26 Dealing with Cookies Earlier 6 browsers simply stored cookies without comment Today’s browsers allow options to: Store cookies without permission or warning Receive a warning that a cookie is about to be stored Unconditionally disallow cookies altogether 27 Protecting Electronic Commerce Channels: Communication Path Protecting 6 assets while they are in transit between client computers and remote servers Providing channel security includes Channel secrecy Guaranteeing message integrity Ensuring channel availability Authentication 28 Providing Transaction Privacy Encryption 6 The coding of information by using a mathematically based program and secret key to produce unintelligible characters. Original information is changed. Steganography Makes text invisible to the naked eye Cryptography Converts text to strings that appear to have no meaning 29 Encryption 6 40-bit keys are considered minimal,128-bit keys provide much more secure encryption Encryption can be subdivided into three functions Hash Coding Asymmetric (Public-key) Encryption Uses a hash algorithm to calculate a number called “hash value” from the original message string. Encodes by using two mathematically related keys Symmetric (Private-key) Encryption Encodes by using one key, both sender and receiver must know 30 Hash Coding 6 Uses a hash algorithm to calculate a number called hash value from the original message string. Typically, the algorithm uses all 1s and 0s that comprise a message, and come up with a value. Thus two messages should never have the same hash value. Comparing the hash value before and after transmission of a message, can determine whether the message has been changed or not. 31 Asymmetric (or Public-key) Encryption 6 Encodes messages by using two mathematicallyrelated numeric keys: a public key and a private key. The public key is freely available to anyone (public) who wants to communicate with the holder of both keys. It is used to encrypt messages. The private key belongs to the key owner in secret, and is used to decrypt an encrypted message. If Jack wants to send a message to Jill, then Jack obtains Jill’s public key, encrypts the message with it, and sends it. Only Jill can decrypt this message with her private key. 32 Symmetric (or Private-key) Encryption 6 Encodes a message using a single numeric key (private key) to encode and decode data. Because same key is used, both the sender and the receiver must know the key. Thus it is not suitable for public communication over the Internet. But, it might be suitable for highly secured communication such as that in defense sector or between two business partners. 33 Hash Coding, Private-key, and Public-key Encryption 6 34 Significant Encryption Algorithms and Standards 6 35