154 kb - Mahopac Central School District
... descriptions of objects and events and to from their own tentative explanations of what they have observed. Key Idea 2: Beyond the use of reasoning & consensus, scientific inquiry involves the testing of proposed explanations involving the use of conventional techniques & procedures & usually requir ...
... descriptions of objects and events and to from their own tentative explanations of what they have observed. Key Idea 2: Beyond the use of reasoning & consensus, scientific inquiry involves the testing of proposed explanations involving the use of conventional techniques & procedures & usually requir ...
Internet Control Message Protocol
... As you have seen today and over the last two days, many problems can occur in routing a message from sender to receiver. The TTL timer might expire; fragmented datagrams might not arrive with all segments intact; a gateway might misroute a datagram, and so on. Letting the sending device know of a pr ...
... As you have seen today and over the last two days, many problems can occur in routing a message from sender to receiver. The TTL timer might expire; fragmented datagrams might not arrive with all segments intact; a gateway might misroute a datagram, and so on. Letting the sending device know of a pr ...
256 Bit Key — Is It Big Enough?
... usually called “offline” attacks since the attacker doesn’t use the Host or Client system to try each possibility. Instead, the attacker uses external computers to mimic the computation of the authentication device to guess the stored secret, trying to generate a sequence of bits which matches that ...
... usually called “offline” attacks since the attacker doesn’t use the Host or Client system to try each possibility. Instead, the attacker uses external computers to mimic the computation of the authentication device to guess the stored secret, trying to generate a sequence of bits which matches that ...
Fundamental Principles of Counting
... Two ways to count the same set of objects • Often there are two ways to count the same set of objects and this leads to an interesting result since the two ways must give the same answer. This is known as a combinatorial argument. • Problem. How many subsets of a given set with n elements are there ...
... Two ways to count the same set of objects • Often there are two ways to count the same set of objects and this leads to an interesting result since the two ways must give the same answer. This is known as a combinatorial argument. • Problem. How many subsets of a given set with n elements are there ...
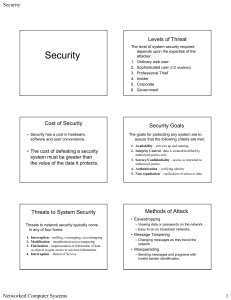
Slides on Security
... • Encryption can be used to secure messages sent over a network. • Encryption can also be used to secure data stored on a computer. • Think of a data file as a very slow message. ...
... • Encryption can be used to secure messages sent over a network. • Encryption can also be used to secure data stored on a computer. • Think of a data file as a very slow message. ...
Packaging Information: Data Compression and
... No attempt is made to keep secret the actual encryption and decryption algorithms for public key methods -- security depends on only the recipient knowing his or her private key Public key ciphers are more secure than secret key ciphers, but are not as efficient since they require longer keys and mo ...
... No attempt is made to keep secret the actual encryption and decryption algorithms for public key methods -- security depends on only the recipient knowing his or her private key Public key ciphers are more secure than secret key ciphers, but are not as efficient since they require longer keys and mo ...
Name: Section 11.1 – Permutations and Combinations Warm up
... Problem 1 – How many standard PA license plate possibilities are there if PA uses 3 letters followed by 4 numbers? ...
... Problem 1 – How many standard PA license plate possibilities are there if PA uses 3 letters followed by 4 numbers? ...
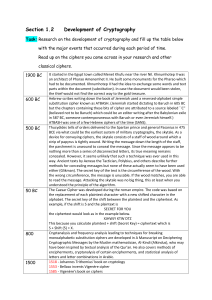
compatible-development-of
... an architect of Pharao Amenemhet II. He built some monuments for the Pharao which had to be documented. Khnumhotep II had the idea to exchange some words and text parts within the document (substitution). In case the document would been stolen, the thief would not find the correct way to the gold tr ...
... an architect of Pharao Amenemhet II. He built some monuments for the Pharao which had to be documented. Khnumhotep II had the idea to exchange some words and text parts within the document (substitution). In case the document would been stolen, the thief would not find the correct way to the gold tr ...
Chapter 8: Network Security
... exploits vulnerabilities in end-systems. Worms, pieces of self-replicating code that spread over networks, have been known for several decades and continue to cause problems, as do their relatives, viruses, which are spread by the transmission of “infected” files. Infected machines can then be arran ...
... exploits vulnerabilities in end-systems. Worms, pieces of self-replicating code that spread over networks, have been known for several decades and continue to cause problems, as do their relatives, viruses, which are spread by the transmission of “infected” files. Infected machines can then be arran ...
E-Commerce Security
... who they claim to be? • Privacy: Are the contents of a message secret and only known to the sender and receiver? • Integrity: Have the contents of a message been modified during transmission? • Nonrepudiation: Can the sender of a message deny that they actually sent the message? ...
... who they claim to be? • Privacy: Are the contents of a message secret and only known to the sender and receiver? • Integrity: Have the contents of a message been modified during transmission? • Nonrepudiation: Can the sender of a message deny that they actually sent the message? ...
Public Key Encryption and Digital Signatures
... – If an intruder intercepts a request from A for B’s public key, the intruder can masquerade as B and receive messages from B intended for A. The intruder can send those same or different messages to B, pretending to be A. – Prevention requires authentication of the public key to be used. ...
... – If an intruder intercepts a request from A for B’s public key, the intruder can masquerade as B and receive messages from B intended for A. The intruder can send those same or different messages to B, pretending to be A. – Prevention requires authentication of the public key to be used. ...
Risk Management
... 20th Century Cryptography Development of Crypt in the 1900s Manual Methods – Slow – Laborious – Error-Prone Need to mechanise Importance of technology for design Nature of technological constraints ...
... 20th Century Cryptography Development of Crypt in the 1900s Manual Methods – Slow – Laborious – Error-Prone Need to mechanise Importance of technology for design Nature of technological constraints ...
Implementing Security for Electronic Commerce
... Comparing the hash value before and after transmission of a message, can determine whether the message has been changed or not. ...
... Comparing the hash value before and after transmission of a message, can determine whether the message has been changed or not. ...
Grill (cryptology)

The grill method (Polish: metoda rusztu), in cryptology, was a method used chiefly early on, before the advent of the cyclometer, by the mathematician-cryptologists of the Polish Cipher Bureau (Biuro Szyfrów) in decrypting German Enigma machine ciphers. The Enigma rotor cipher machine changes plaintext characters into cipher text using a different permutation for each character, and so implements a polyalphabetic substitution cipher.