HP Intelligent Management Center v7.1 Basic Getting Started Guide
... 2 Exploring IMC Basic...................................................................................5 Logging in to IMC Basic............................................................................................................5 Understanding the GUI........................................ ...
... 2 Exploring IMC Basic...................................................................................5 Logging in to IMC Basic............................................................................................................5 Understanding the GUI........................................ ...
HoneyPot1 - Security Research
... •Attack Strategies: find out reasons and strategies why and how attacks happen •Attack Tools: detailed information of attack tools •Increased knowledge: knowing how to respond & prevent future attacks •Identification and Classification: Find out who is attacking you and profile them ...
... •Attack Strategies: find out reasons and strategies why and how attacks happen •Attack Tools: detailed information of attack tools •Increased knowledge: knowing how to respond & prevent future attacks •Identification and Classification: Find out who is attacking you and profile them ...
Lecture Notes - Computer Science & Engineering
... – AntiSniff (L0pht Heavy Industries, Inc. ): remotely detects computers that are packet sniffing, regardless of the OS Interesting read: S. Truth, How to Test for Sniffing Vulnerabilities, http://web.securityinnovation.com/appsecweekly/blog/bid/63274/How-to-Test-for-SniffingVulnerabilities ...
... – AntiSniff (L0pht Heavy Industries, Inc. ): remotely detects computers that are packet sniffing, regardless of the OS Interesting read: S. Truth, How to Test for Sniffing Vulnerabilities, http://web.securityinnovation.com/appsecweekly/blog/bid/63274/How-to-Test-for-SniffingVulnerabilities ...
Chapter 10
... – Access control: Who is allowed to log on to and access site? – Secrecy: Who is permitted to view selected information? – Data integrity: Who is allowed to change data? – Audit: Who or what causes specific events to occur, and when? ...
... – Access control: Who is allowed to log on to and access site? – Secrecy: Who is permitted to view selected information? – Data integrity: Who is allowed to change data? – Audit: Who or what causes specific events to occur, and when? ...
LogMeIn Security – an In-Depth Look
... Server. The attacker, in this case, can sit between the two parties while reading, or possibly modifying, the data in transit. This is known as a “Man In The Middle”, or MITM attack and is especially hard to protect against. LogMeIn utilizes SSL/TLS certificates to verify Server identities and thus ...
... Server. The attacker, in this case, can sit between the two parties while reading, or possibly modifying, the data in transit. This is known as a “Man In The Middle”, or MITM attack and is especially hard to protect against. LogMeIn utilizes SSL/TLS certificates to verify Server identities and thus ...
CH10
... – Execute like other client computer programs – Have access to full system resources • Cause secrecy, integrity, and necessity violations ...
... – Execute like other client computer programs – Have access to full system resources • Cause secrecy, integrity, and necessity violations ...
Physical Security
... the Internet, from web servers to browsers. • When a secure connection is needed, SSL/TLS is used and appears in the address as https://. • If the protocol is https:, your connection is secure. • If the protocol is http:, then the connection is carried by plaintext for anyone to see. ...
... the Internet, from web servers to browsers. • When a secure connection is needed, SSL/TLS is used and appears in the address as https://. • If the protocol is https:, your connection is secure. • If the protocol is http:, then the connection is carried by plaintext for anyone to see. ...
SNMP
... Individual message exchange times are larger in TLS/TCP than under UDP. This is because of the TLS/TCP session has to implement the TLS record protocol when sending and receiving data. Thus for each message, the following takes place: Fragment data/reassemble data ...
... Individual message exchange times are larger in TLS/TCP than under UDP. This is because of the TLS/TCP session has to implement the TLS record protocol when sending and receiving data. Thus for each message, the following takes place: Fragment data/reassemble data ...
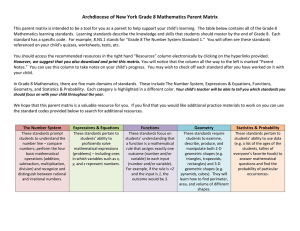
8th-Grade-Math-WORD - Build Bold Futures
... because 3x + 2y cannot simultaneously be 5 and 6. c. Solve real-world and mathematical problems leading to two linear equations in two variables. For example, given coordinates for two pairs of points, determine whether the line through the first pair of points intersects the line through the second ...
... because 3x + 2y cannot simultaneously be 5 and 6. c. Solve real-world and mathematical problems leading to two linear equations in two variables. For example, given coordinates for two pairs of points, determine whether the line through the first pair of points intersects the line through the second ...
Cafe Cracks: Attacks on Unsecured Wireless Networks
... It is possible that users will have some of their own network parameters, such as DNS server, manually configured. To still perform DNS attacks the attack machine will need to be able to perform packet redirects as part of its routing capabilities. For example, since all DNS request traffic runs on ...
... It is possible that users will have some of their own network parameters, such as DNS server, manually configured. To still perform DNS attacks the attack machine will need to be able to perform packet redirects as part of its routing capabilities. For example, since all DNS request traffic runs on ...
Document
... In economics, the 'Total Revenue Test' is a means for determining whether demand is elasticity (economics)|elastic or inelastic. If an increase in price causes an increase in total revenue, then demand can be said to be inelastic, since the increase in price does not have a large impact on quantity ...
... In economics, the 'Total Revenue Test' is a means for determining whether demand is elasticity (economics)|elastic or inelastic. If an increase in price causes an increase in total revenue, then demand can be said to be inelastic, since the increase in price does not have a large impact on quantity ...
Firewall Toolkit (FWTK)
... For applications to work with the SOCKS proxy server, they must be "SOCKS-ified." Most of the work involved in doing this has been packaged into the SOCKS software development kit (SDK). SOCKS has evolved over time and gone through several revisions. SOCKS version 4 was the first popular version ...
... For applications to work with the SOCKS proxy server, they must be "SOCKS-ified." Most of the work involved in doing this has been packaged into the SOCKS software development kit (SDK). SOCKS has evolved over time and gone through several revisions. SOCKS version 4 was the first popular version ...
CHAPTER 1 Networking Concepts
... SET (Secure Electronic Transaction) SET is an open encryption and security specification designed to protect credit card transactions on the Internet ...
... SET (Secure Electronic Transaction) SET is an open encryption and security specification designed to protect credit card transactions on the Internet ...
Penetration Testing Report - Network Intelligence India
... Implement access control on SQL server – Give appropriate privileges to authorized users only. Change Firewall ACL configuration: If port 110 is not required to be open on the Internet, modify the ACL to block all incoming traffic. Upgrade phpBB: Upgrade phpBB to prevent critical attacks exploiting ...
... Implement access control on SQL server – Give appropriate privileges to authorized users only. Change Firewall ACL configuration: If port 110 is not required to be open on the Internet, modify the ACL to block all incoming traffic. Upgrade phpBB: Upgrade phpBB to prevent critical attacks exploiting ...
CGI Programming: Part 2 Robert M. Dondero, Ph.D. Princeton University 1
... Tools → Page Info → Security → View Cookies ...
... Tools → Page Info → Security → View Cookies ...
Grid Programming (1)
... No way to know how and where published certificates are used Certificate authority Certificate request ...
... No way to know how and where published certificates are used Certificate authority Certificate request ...
CTF - CIAST
... UCSB sp0nsorz – won last years Defcon Test Skills of understanding security What it’s not! ...
... UCSB sp0nsorz – won last years Defcon Test Skills of understanding security What it’s not! ...
Slides - owasp
... Malware will inject additional functionality to your application, in order to conduct the attacks, persist ...
... Malware will inject additional functionality to your application, in order to conduct the attacks, persist ...
Very non-resistant
... Difference Betw’n Mean & Median A more flexible web example: http://www.ruf.rice.edu/~lane/stat_sim/descriptive/index.html ...
... Difference Betw’n Mean & Median A more flexible web example: http://www.ruf.rice.edu/~lane/stat_sim/descriptive/index.html ...
Computer Network Security Protocols and Standards
... there are some differences in design goals, implementation, and acceptance. – First S-HTTP was designed to work with only web protocols. Because SSL is at a lower level in the network stack than S-HTTP, it can work in many other network protocols. – Secondly, in terms of implementation, since SSL is ...
... there are some differences in design goals, implementation, and acceptance. – First S-HTTP was designed to work with only web protocols. Because SSL is at a lower level in the network stack than S-HTTP, it can work in many other network protocols. – Secondly, in terms of implementation, since SSL is ...
Cybersecurity Chapter 3 Test Review
... following is MOST likely causing the issue? The web server is configured on the firewall’s DMZ interface. The VLAN is improperly configured. The firewall’s MAC address has not been entered into the filtering list. The firewall executes an implicit deny. ...
... following is MOST likely causing the issue? The web server is configured on the firewall’s DMZ interface. The VLAN is improperly configured. The firewall’s MAC address has not been entered into the filtering list. The firewall executes an implicit deny. ...
all the web without the risk
... This restriction ensures that, were malware to access the VM, it would not be able to see, map or attack any other infrastructure within the network. Using a second VPN from the server, users have the option to direct their traffic through a Global IP hub of their choice, allowing them to easily con ...
... This restriction ensures that, were malware to access the VM, it would not be able to see, map or attack any other infrastructure within the network. Using a second VPN from the server, users have the option to direct their traffic through a Global IP hub of their choice, allowing them to easily con ...
The key questions that we`d like to ask at the beginning
... your entire conversation. Because if a hacker does manage to gain access to the private key, he still won’t be able to recover the shared, short-term secret key and will not be able to decrypt any communications. What’s more, PFS continuously changes the key material during a session, generating a n ...
... your entire conversation. Because if a hacker does manage to gain access to the private key, he still won’t be able to recover the shared, short-term secret key and will not be able to decrypt any communications. What’s more, PFS continuously changes the key material during a session, generating a n ...
HTTPS

HTTPS (also called HTTP over TLS, HTTP over SSL, and HTTP Secure) is a protocol for secure communication over a computer network which is widely used on the Internet. HTTPS consists of communication over Hypertext Transfer Protocol (HTTP) within a connection encrypted by Transport Layer Security or its predecessor, Secure Sockets Layer. The main motivation for HTTPS is authentication of the visited website and to protect the privacy and integrity of the exchanged data.In its popular deployment on the internet, HTTPS provides authentication of the website and associated web server with which one is communicating, which protects against man-in-the-middle attacks. Additionally, it provides bidirectional encryption of communications between a client and server, which protects against eavesdropping and tampering with and/or forging the contents of the communication. In practice, this provides a reasonable guarantee that one is communicating with precisely the website that one intended to communicate with (as opposed to an impostor), as well as ensuring that the contents of communications between the user and site cannot be read or forged by any third party.Historically, HTTPS connections were primarily used for payment transactions on the World Wide Web, e-mail and for sensitive transactions in corporate information systems. In the late 2000s and early 2010s, HTTPS began to see widespread use for protecting page authenticity on all types of websites, securing accounts and keeping user communications, identity and web browsing private.