* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Security & Cryptography
Quantum key distribution wikipedia , lookup
Unix security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Proxy server wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Web of trust wikipedia , lookup
Computer security wikipedia , lookup
Cryptography wikipedia , lookup
Security-focused operating system wikipedia , lookup
History of cryptography wikipedia , lookup
Distributed firewall wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Authentication wikipedia , lookup
Mobile security wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Transport Layer Security wikipedia , lookup
Wireless security wikipedia , lookup
Electronic authentication wikipedia , lookup
Diffie–Hellman key exchange wikipedia , lookup
Deep packet inspection wikipedia , lookup
Secure multi-party computation wikipedia , lookup
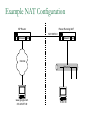
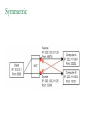
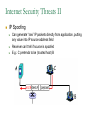
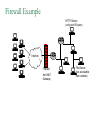
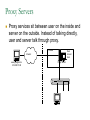
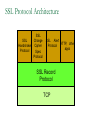
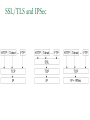
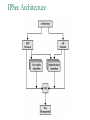
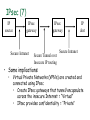
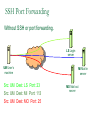
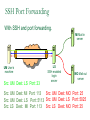
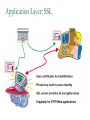
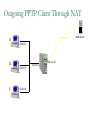
Network Security Today’s Universities Campus Perimeter Security Anti-virus system 100 % Firewalls Remote access VPN, using IPSEC 96.2 % 78.8 % 78.8 % Access control 55.8 % Content filtering 57.7 % Intrusion Detection System Remote access VPN using SSL Other * Anti-virus system Firewalls Remote access VPN, using IPSEC Access control Content filtering Intrusion Detection System Remote access VPN using SSL Other 25 % 11.5 % * Other includes packet shapers, proxy servers and smart-card authentication. Security challenges for remote offices 53.8 % Lack of personnel/expertise Complexity Management costs are too high Solution costs are too high Lack of one-stop shopping from vendors 51.9 % 42.3 % 36.5 % 21.2 % Agenda NAT – the most common and quite effective zeromainetnance firewall PacketFilters and RealFirewalls SSL/TLS: transport layer security Easy to use CA infrastructure SSH IPSec: network layer security (VPN) Difficult to deploy Transport or Tunnel mode Use of Private Addresses Routers in the public Internet will not route packets whose destination are private addresses 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16 However, it is possible for routers in a private network to route packets with private addresses The same private addresses can be reused in different private networks NAT Basics Network Address Translator (NAT) Defined in RFC 3022 Standard application map private IP address range 10.0.0.0 – 10.255.255.255 172.16.0.0 – 172.31.255.255 192.168.0.0192.168.255.255 to public IP address range Network Address Port Translation (NAPT or Masquerading) NAPT Basics Network Address Port Translator Can map multiple private IP addresses and ports to one public IP address and ports NAT Internals NAT modifies headers in IP and TCP/UDP IP header Source (outgoing) or destination (incoming) IP address IP header checksum TCP/UDP header Source (outgoing) or destination (incoming) TCP/UDP port TCP/UDP checksum NAT Fields modified in IP and TCP header: IP header TCP Header vsn len tos total length source port destination port identification flgs fragment offset sequence number TTL protocol header checksum acknowledgement number source IP address hlen rsv flags window size destination IP address TCP checksum urgent pointer options (optional) data options (optional) data (optional) NAT Some protocols include IP address in data portion of IP datagram Example is FTP: FTP uses 2 connections Control connection for login, commands Data connection for data transfer FTP client tells FTP server how to open the data connection -- supplies IP address and port These are in data section of IP datagram; not protocol headers, so NAT translation becomes application-specific NAT - ALG’s Application Layer Gateways (or ALG’s) sit on NAT gateway to translate IP and port information in data Must have separate ALG for each application to be translated Common applications which need ALG: FTP, DNS, SNMP, H.323 (Voice over IP) USNET-NAT has an FTP ALG Further complications possible besides IP/Port translation NAT ALG for FTP FTP ALG must: Translate IP address in data portion Set up NAT router to accept incoming connection Modify TCP (or UDP) checksum Check for data length changes - if even one segment length changes, modify TCP sequence and ACK numbers for remainder of session RFC 3022 Example NAT Configuration Router Running NAT ISP Router 198.198.50.0 Internet Ethernet www.google.com 216.239.57.99 10.0.0.50 Types of NAT I Static NAT maintains a fixed mapping from private addresses to global addresses, which must be configured manually. Dynamic NAT Global IP address is issued for each “session” TCP/IP: NAT router checks for SYN/FIN flags Types of NAT II 1. 2. 3. 4. Full Cone Restricted Cone Port Restricted Cone Symmetric Network Address Translation NAT is a major problem for media communications NAT: Full Cone Any computer can send back data to an open port. Restricted Cone Any computer can send back data to an open port AFTER we send data to their IP. Port Restricted Cone Same as restricted cone but we need to first send data to their IP AND the port that will be allowed to send back. Symmetric Internet Security Threats I Packet Sniffing Broadcast media e.g. Ethernet, wireless comms Promiscuous NIC reads all packets passing by Can read all unencrypted data (e.g. passwords) E.g. C sniffs B’s packets Internet Security Threats II IP Spoofing Can generate “raw” IP packets directly from application, putting any value into IP source address field Receiver can’t tell if source is spoofed E.g.: C pretends to be (trusted host) B Internet Security Threats III Denial of service (DOS) Flood of maliciously generated packets “swamp” to receiver Distributed DOS (DDOS): multiple coordinated sources swamp one receiver E.g.: C and remote host SYN-attack A No real defense against this attack!! Types of firewalls Packet filters Standard packet filter Stateful packet filter Proxy gateways Network Address Translation (NAT) Intrusion Detection Logging Components of firewall Firewall Example HTTP-Server (only port 80 open) Internet Firewall And NAT Gateway File-Server (not accessible from outside) Packet Filtering Block or allow packets based on rules. Filtering based on packet headers and interface it arrives on. Filtering Strategies Example – Inbound telnet open not allowed. That which is not explicitly permitted is prohibited. That which is not explicitly prohibited is permitted. Session and protocol tracking Fragmented IP packets Packets violating the L4-L7 protocol Proxy Servers Proxy services sit between user on the inside and server on the outside. Instead of talking directly, user and server talk through proxy. Firewall Dual homed Host Internet www.google.com 216.239.57.99 Proxy Server Ethernet Network Address Translation Network Address Translation (NAT) allows a network to use one set of addresses internally and a different set when dealing with external networks. It helps conceal internal network and force connections to go through choke point. Router does the extra work required for address translation. Threat Alice Bob Eve •Alice and Bob want to communicate •Eve is eavesdropping (intercept, delete, add messages) What is Network Security? Secrecy: Only sender and intended receiver should be able to “understand” message Authentication: Sender and receiver want to confirm identity of each other Message Integrity: Sender and receiver want to ensure that message has not been altered without detection Taxonomy of Network Security Secure Communication Symmetric Cryptography (e.g., DES) Asymmetric Cryptography (e.g., RSA) Message Digests (e.g., MD5) Cryptographic Security Technologies En-/Decryption/Signing of E-Mail En-/Decryption of Shell Communication e.g. PrettyGoodPrivacy (PGP) e.g. SecureShell (SSH) En-/Decryption on Protocol Level e.g. SSL (TCP), IPSec (IP) Basic crypto applications Algorithms: DES, AES, 3DES Used for actual reversible encryption “non-entropic”, reversible operations Requires a unique “secret key” for the encryptor and decryptor Hashes: SHA-1, MD5 Used to generate a unique mathematical “summary value” for a given dataset “Entropic”, non-reversible operation Used to authenticate a data set Can be combined with a “secret key” value to create a custom Hash- ensures that your hash was created by someone you trust. Symmetric Key Distribution • Key distribution • Public key via trusted Certificate Authorities • Symmetric key? • • Diffie-Helman Key Exchange Public key, then symmetric key (e.g. SSL) Secure Socket Layer (SSL) SSL works at transport layer. Provides security to any TCPbased app using SSL services. SSL: used between WWW browsers, servers for E-commerce (shttp, scp). SSL security services: server authentication data encryption client authentication (optional) Server authentication: SSL enabled browser includes public keys of trusted CAs. Browser requests servercertificate, issued by trusted CA. Browser uses CA’s public key to extract server’s public key from certificate. Visit your browser’s security menu to see its trusted CAs. SSL and TLS SSL designed by Netscape TLS IETF standard SSL and TLS provide applications: compromise between SSL and a Microsoft protocol Encryption Server authentication (Optional) client authentication SSL programming libraries are pretty easy to use SSL Protocol Architecture SSL Handshake Protocol SSL Change Cipher Spec Protocol SSL Alert HTTP, other Protocol apps SSL Record Protocol TCP SSL Handshake Pretty complicated Server (and client) authentication Negotiation of: why HTTPS websites seem sooooooo slow. Encryption algorithm MAC algorithm Encryption key Must be done before any data transmission SSL/TLS and IPSec How does SSL differ? SSL is based on PKI, which uses public/private key pairs- using entirely different math Designed to enable secure transfer of data (like a temporary crypto key) to someone you don’t necessarily trust IKE/IPSec does not use PKI, as it is inherently less safe- and designed for e-commerce use Actually, PKI-like key exchange is used in some limited ways in IKE, but the core of IPSec is not based on public/private key exchange IPSec Overview What is IKE and IPSEC? Generally speaking, IKE is a method for securely exchanging encryption ciphers that will be used in a later encrypted session IPSec is an overall term used to describe encrypted data communication over IP, using the keys exchanged with IKE Remember, the problem is not just encrypting the messagesit’s keeping your keys safe in the long term This is accomplished by renegotiating keys often in IPSec- this compartmentalizes the encryption and data exchange This means that secret keys must be exchanged often IPSec Architecture IPSec There are three parts to IPSec: AH- authentication header- provides session security at a “sophisticated” level by checking data integrity and protecting against “replay” attacks (protocol 51) ESP- encapsulating security payload- provides the bulk data encryption method (protocol 50) IKE- handles the exchange of secret keys used in the prior two categories (udp port 500) NOTE: IKE generally cannot be NATted, as the IP addresses used by each participating gateway are tracked, and NAT looks like a replay attack The guts of key exchange Sending Gateway determines a packet needs to be encrypted Sending Gateway opens an IKE session with the Receiving gateway- this step defines the IKE SA Diffie-Hellman key exchange uses hashing of a certificate or shared secret to authenticate each gateway, and sets up a public/private data exchange channel Sending and Receiving Gateways exchange protocol settings, algorithm settings, and secret keys using PKI A new IPSec SA is defined for the ESP tunnel, and data begins to be transferred New term: Selector- a logical construct similar to a route, that allows the gateway to determine if an inbound packet is to be encrypted and passed over a particular SA Quick Mode IKE Hash type, SA type (ESP), IP information (encryption domains/selectors) Hash type, SA type (ESP), IP information (encryption domains/selectors) ACK HASH return HASH More details: You don’t really have to use IKE: Enter many large ugly numbers Keep track of them and keep them secret Pass them from site to site Change them secretly Have fun! IPSec in Tunnel Mode IP Header New IP Header ESP Head Old IP Head IP DATA IP DATA ESP trailer ESP Auth Authenticated and Encrypted What does the header look like? Here’s a picture: NEW IP HEADER Security Parameter Index Sequence Number Initialization Vector Encrypted IP Header UDP header (or whatever) DATA Data Padding Trailer: padding, pad ln ESP Authentication Encap. Header ESP Header ESP Header ESP Header ESP Trailer Why padding? Some Algorithms (DES) require specific block sizes for “Cipher Block Chaining”, which speeds encryption. IPsec Transport mode • ESP protocol provides network-layer secrecy, source host authentication and data integrity • TCP/UDP segment is surrounded by header and trailer fields • • DES-CBC encryption of TCP/UDP segment + trailer Trailer lists the Protocol of the segment (TCP, or UDP, or …). Hidden from observers. • Normal IP routing using IP header. Destination sees protocol=50 and decrypts ESP packet IPsec – no encryption • AH protocol provides source authentication and data integrity, but not secrecy • Insert an AH header between IP header (indicated by Protocol = 51) • • Next Header field indicates whether segment is TCP, UDP, etc. Authentication Data field contains a digital signature, or signed message digest calculated over the original IP datagram • • • Provides source authentication Provides datagram integrity tamper check Digital signature could be DES, MD5, or SHA - negotiated Tunnel and Transport Mode Authentication Header (AH) Authenticates the sender Encapsulating Security Payload (ESP) Data encryption Can be done in two ways: Transport mode: only the transport layer segment is encrypted Tunnel mode encrypt the entire IP datagram put it inside another IP datagram IPsec (7) IP source IPsec gateway Secure Intranet Secure Tunnel over Insecure IP routing • Some implications: • IPsec gateway IP dest Secure Intranet Virtual Private Networks (VPN’s) are created and connected using IPsec • Create IPsec gateways that tunnel/encapsulate across the insecure Internet = “Virtual” • IPsec provides confidentiality = “Private” SSH Overview SSH = Secure Shell. Initially designed to replace insecure rsh, telnet utilities. Secure remote administration (mostly of Unix systems). Extended to support secure file transfer and e-mail. Latterly, provide a general secure channel for network applications. SSH-1 flawed, SSH-2 better security (and different architecture). SSH provides security at Application layer. Only covers traffic explicitly protected. Applications need modification, but port-forwarding eases some of this (see later). Built on top of TCP, reliable transport layer protocol. SSH Overview SSH Communications Security (SCS). Open source version from OpenSSH. IETF Secure Shell (SECSH) working group. www.ssh.com. Founded by Tatu Ylonen, writer of SSH-1. SSH is a trademark of SCS. Standard for SSH in preparation. www.ietf.org/html.charters/secsh-charter.html. Long-running confusion and dispute over naming. SSH-2 Architecture SSH-2 adopts a three layer architecture: SSH Transport Layer Protocol. SSH Authentication Protocol Initial connection. Server authentication (almost always). Sets up secure channel between client and server. Client authentication over secure transport layer channel. SSH Connection Protocol Supports multiple connections over a single transport layer protocol secure channel. Efficiency (session re-use). SSH-2 Architecture Applications SSH Connection Protocol SSH Authentication Protocol SSH Transport Layer Protocol TCP SSH-2 Security Goals Server (nearly) always authenticated in transport layer protocol. Client (nearly) always authenticated in authentication protocol. Establishment of a fresh, shared secret. By public key (DSS, RSA, SPKI, OpenPGP). Or simple password for particular application over secure channel. Shared secret used to derive further keys, similar to SSL/IPSec. For confidentiality and authentication in SSH transport layer protocol. Secure ciphersuite negotiation. Encryption, MAC, and compression algorithms. Server authentication and key exchange methods. SSH-2 Algorithms Key establishment through Diffie-Hellman key exchange. Variety of groups supported. Server authentication via RSA or DSS signatures on nonces (and other fields). HMAC-SHA1 or HMAC-MD5 for MAC algorithm. 3DES, RC4, or AES finalists (Rijndael/Serpent). Pseudo-random function for key derivation. Small number of ‘official’ algorithms with simple DNS-based naming of ‘private’ methods. SSH-1 versus SSH-2 Many vulnerabilities have been found in SSH-1 . SSH-1 Insertion attack exploiting weak integrity mechanism (CRC-32) and unprotected packet length field. SSHv1.5 session key retrieval attack (theoretical). Man-in-the-middle attacks (using e.g. dsniff). DoS attacks. Overload server with connection requests. Buffer overflows. But SSH-1 widely deployed. And SSH-1 supports: Wider range of client authentication methods (.rhosts and Kerberos). Wider range of platforms. SSH Port Forwarding Without SSH or port forwarding. LS Login server UM User’s machine Src: UM Dest: LS Port: 23 Src: UM Dest: MI Port: 113 Src: UM Dest: MO Port: 25 MI Mail in server MO Mail out server SSH Port Forwarding Recall: TCP port number ‘identifies’ application. SSH on local machine: Intercepts traffic bound for server. Translates standard TCP port numbers. E.g. port 113 port 5113. Sends packets to SSH-enabled server through SSH secure channel. SSH-enabled server: Receives traffic. Re-translates port numbers. E.g. port 5113 port 113. Forwards traffic to appropriate server using internal network. SSH Port Forwarding With SSH and port forwarding. MI Mail in server UM User’s machine Src: UM Dest: LS Port: 23 LS SSH-enabled login server MO Mail out server Src: UM Dest: MO Port: 25 Src: UM Dest: MI Port: 113 Src: UM Dest: LS Port: 5113 Src: UM Dest: LS Port: 5025 Src: LS Dest: MI Port: 113 Src: LS Dest: MO Port: 25 SSH Applications Anonymous ftp for software updates, patches... Secure ftp. E.g.upload of webpages to webserver using sftp. Server now needs to authenticate clients. Username and password may be sufficient, transmitted over secure SSH transport layer protocol. Secure remote administration. No client authentication needed, but clients want to be sure of origin and integrity of software. SysAdmin (client) sets up terminal on remote machine. SysAdmin password protected by SSH transport layer protocol. SysAdmin commands protected by SSH connection protocol. Guerilla Virtual Private Network. 6.3 Comparing IPSec, SSL/TLS, SSH All three have initial (authenticated) key establishment then key derivation. IKE in IPSec Handshake Protocol in SSL/TLS (can be unauthenticated!) Authentication Protocol in SSH All protect ciphersuite negotiation. All three use keys established to build a ‘secure channel’. Comparing IPSec, SSL/TLS, SSH Operate at different network layers. This brings pros and cons for each protocol suite. Recall `Where shall we put security?’ discussion. Naturally support different application types, can all be used to build VPNs. All practical, but not simple. Complexity leads to vulnerabilities. Complexity makes configuration and management harder. Complexity can create computational bottlenecks. Complexity necessary to give both flexibility and security. Comparing IPSec, SSL/TLS, SSH Security of all three undermined by: Implementation weaknesses. Weak server platform security. Weak user platform security. Keystroke loggers, malware,… Limited deployment of certificates and infrastructure to support them. Worms, malicious code, rootkits,… Especially client certificates. Lack of user awareness and education. Users click-through on certificate warnings. Users fail to check URLs. Users send sensitive account details to bogus websites What is a VPN Public networks are used to move information between trusted network segments using shared facilities like frame relay or atm A VIRTUAL Private Network replaces all of the above utilizing the public Internet Performance and availability depend on your ISP and the Internet VPN Implementations VPN as your Intranet VPN Components Technologies Application Layer: SSL Tunnel vs Transport Transport Implemented by the end point systems Real address to real address Cannot ‘go through’ other networks Tunnel Encapsulation of the original IP packet in another packet Can ‘go through’ other networks End systems need not support this Often PC to a box on the ‘inside’ PPTP: Free from Microsoft PPTP: Security Outgoing PPTP Client Through NAT a Internet 10.0.0.2 NAT b c 10.0.0.3 10.0.0.4 10.0.0.1 204.x.1.10 web server VPN Comparisons