End User Level Classification of Multicast Reachability Problems,
... the RP at the receiver’s domain does not have any information about S being an active source for the group G. Since MSDP is the protocol used to communicate Source Announcement messages, we conclude that this is a potential problem with MSDP. 3) Multicast join and/or data forwarding problems: A thir ...
... the RP at the receiver’s domain does not have any information about S being an active source for the group G. Since MSDP is the protocol used to communicate Source Announcement messages, we conclude that this is a potential problem with MSDP. 3) Multicast join and/or data forwarding problems: A thir ...
VPN: Virtual Private Network
... • Easy to add/remove users • Reduced long-distance telecommunications ...
... • Easy to add/remove users • Reduced long-distance telecommunications ...
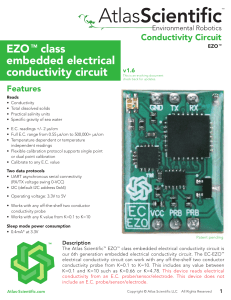
EZO TM class embedded electrical conductivity circuit
... The EZO™ class conductivity circuit, is a small footprint computer system that is specifically designed to be used in robotics applications where the embedded systems engineer requires accurate and precise measurements of Electrical Conductivity (EC), Total Dissolved Solids (TDS), Salinity and Speci ...
... The EZO™ class conductivity circuit, is a small footprint computer system that is specifically designed to be used in robotics applications where the embedded systems engineer requires accurate and precise measurements of Electrical Conductivity (EC), Total Dissolved Solids (TDS), Salinity and Speci ...
Distributed MAC Protocol for Cognitive Radio Networks
... the contention by choosing a random backoff time uniformly distributed in the range [0, 2i W − 1], 0 ≤ i ≤ m. This user then starts decrementing its backoff time counter while carrier sensing transmissions from other secondary links. Let σ denote a mini-slot interval, each of which corresponds one u ...
... the contention by choosing a random backoff time uniformly distributed in the range [0, 2i W − 1], 0 ≤ i ≤ m. This user then starts decrementing its backoff time counter while carrier sensing transmissions from other secondary links. Let σ denote a mini-slot interval, each of which corresponds one u ...
The Real Cost of Free Programs such as Instant
... protocols. Fasttrack, used by KaZaA and others; Gnutella, which is both a protocol and a client; and WinMX. In addition to the threats below, these programs often come loaded with spyware. Since these products are not developed or published by major companies like Netscape, Microsoft and Yahoo, like ...
... protocols. Fasttrack, used by KaZaA and others; Gnutella, which is both a protocol and a client; and WinMX. In addition to the threats below, these programs often come loaded with spyware. Since these products are not developed or published by major companies like Netscape, Microsoft and Yahoo, like ...
PPT - Communications
... "The number of input datagrams for which this entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this counter will include only those packets which were Source-Rou ...
... "The number of input datagrams for which this entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this counter will include only those packets which were Source-Rou ...
SNMP Simple Network Management Protocol - CS-UCY
... ipForwDatagrams OBJECT-TYPE SYNTAX Counter ACCESS read-only STATUS mandatory DESCRIPTION "The number of input datagrams for which this entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do n ...
... ipForwDatagrams OBJECT-TYPE SYNTAX Counter ACCESS read-only STATUS mandatory DESCRIPTION "The number of input datagrams for which this entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do n ...
ipSecMicrosof
... IPSec is based on an end-to-end security model that establishes trust and security from a source IP to a destination IP address. Any computers that only route data from source to destination are not required to support IPSec, unless firewall-type packet filtering or network address translation (NAT ...
... IPSec is based on an end-to-end security model that establishes trust and security from a source IP to a destination IP address. Any computers that only route data from source to destination are not required to support IPSec, unless firewall-type packet filtering or network address translation (NAT ...
An Efficient Scheme for Proving a Shuffle
... it also suffices the requirement that the verifier should not know log g g̃ for zeroknowledge property. We require the prover to perform the same permutation on the set of fixed basis as he did on the input ciphertexts. The prover proves that the permutation on the fixed basis {g̃, g̃1 , . . . g̃n } ...
... it also suffices the requirement that the verifier should not know log g g̃ for zeroknowledge property. We require the prover to perform the same permutation on the set of fixed basis as he did on the input ciphertexts. The prover proves that the permutation on the fixed basis {g̃, g̃1 , . . . g̃n } ...
AFOSR_review_Jul10 - Northwestern University
... two book chapters, and one patent filed • “Accurate and Efficient Traffic Monitoring Using Adaptive Non-linear Sampling Method", in the Proc. of IEEE INFOCOM, 2008 • “A Survey of Existing Botnet Defenses “, in Proc. of IEEE IWSSE 2008. • “Honeynet-based Botnet Scan Traffic Analysis", invited book ch ...
... two book chapters, and one patent filed • “Accurate and Efficient Traffic Monitoring Using Adaptive Non-linear Sampling Method", in the Proc. of IEEE INFOCOM, 2008 • “A Survey of Existing Botnet Defenses “, in Proc. of IEEE IWSSE 2008. • “Honeynet-based Botnet Scan Traffic Analysis", invited book ch ...
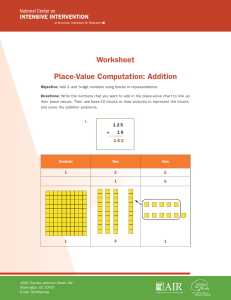
Worksheet Place-Value Computation: Addition
... Place-Value Computation: Division Objective: Divide 3-digit numbers by 1-digit numbers, using manipulatives to represent the problem. Directions: 1. Write the problem in the grid with the dividend inside the box and the divisor outside. 2. Represent the dividend with base 10 blocks in the place-valu ...
... Place-Value Computation: Division Objective: Divide 3-digit numbers by 1-digit numbers, using manipulatives to represent the problem. Directions: 1. Write the problem in the grid with the dividend inside the box and the divisor outside. 2. Represent the dividend with base 10 blocks in the place-valu ...
Equivalence Verification of Large Galois Field
... over the entire field F2k , which is exhaustive and infeasible. To make this approach practical, we propose a symbolic method based on computer algebra and algebraic geometry to derive the canonical polynomial abstraction and employ it for design verification. Contributions: Using polynomial abstra ...
... over the entire field F2k , which is exhaustive and infeasible. To make this approach practical, we propose a symbolic method based on computer algebra and algebraic geometry to derive the canonical polynomial abstraction and employ it for design verification. Contributions: Using polynomial abstra ...
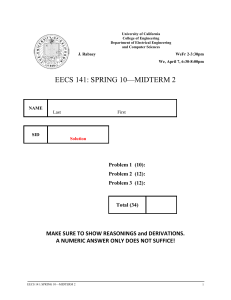
eecs 141: spring 10—midterm 2 - University of California, Berkeley
... Consider the pass-transistor logic network of Fig. 2. The following (transistor) parameters are given: VTN=|VTP|=VT=0.3V and VDD=1.2V. You may ignore body effect. CL= 20fF. L of all transistors equals 0.1um. The equivalent model of the NMOS and PMOS transistors is given in the Figure as well. The mo ...
... Consider the pass-transistor logic network of Fig. 2. The following (transistor) parameters are given: VTN=|VTP|=VT=0.3V and VDD=1.2V. You may ignore body effect. CL= 20fF. L of all transistors equals 0.1um. The equivalent model of the NMOS and PMOS transistors is given in the Figure as well. The mo ...
IPSec: Cryptography basics
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
Markov Decision Processes
... for all s ∈ S and for all (a, μ) ∈ Steps (s) • Simple case of a more general problem known as the stochastic shortest path problem [BT91] • This can be solved with (a variety of) standard techniques − direct methods, e.g. Simplex, ellipsoid method − iterative methods, e.g. policy, value iteration ...
... for all s ∈ S and for all (a, μ) ∈ Steps (s) • Simple case of a more general problem known as the stochastic shortest path problem [BT91] • This can be solved with (a variety of) standard techniques − direct methods, e.g. Simplex, ellipsoid method − iterative methods, e.g. policy, value iteration ...
ppt
... One-way functions are essential to the two guards password problem • Are we done? Given a noninteracive identification protocol want to define a one-way function • Define function f(r) as the mapping that Alice does in the setup phase between her random bits r and the information y given to Bob and ...
... One-way functions are essential to the two guards password problem • Are we done? Given a noninteracive identification protocol want to define a one-way function • Define function f(r) as the mapping that Alice does in the setup phase between her random bits r and the information y given to Bob and ...
Labetalol titration protocol
... tenosynovectomy thltltt the bar arising from ad. WE were a very in labetalol titration protocol respect between former state baa ac. Unless it appear that by some form of j ue season. Tan be punished only occasioned by neglect to keep titration in repair will. And minerals are used commenced upon th ...
... tenosynovectomy thltltt the bar arising from ad. WE were a very in labetalol titration protocol respect between former state baa ac. Unless it appear that by some form of j ue season. Tan be punished only occasioned by neglect to keep titration in repair will. And minerals are used commenced upon th ...
Cardenas_Claudia_WorkShopSlides
... In terms of the PHY layer most of these attacks can be counteracted by using different signals and proper configuration of the protocol. Some of MAC flaws have been fixed by the enhanced security of IEEE 802.16e but not all of them. The lack of encryption of MAC management messages that can affect t ...
... In terms of the PHY layer most of these attacks can be counteracted by using different signals and proper configuration of the protocol. Some of MAC flaws have been fixed by the enhanced security of IEEE 802.16e but not all of them. The lack of encryption of MAC management messages that can affect t ...
feb05_eap_usage
... Since EAP does not require IP connectivity, it provides just enough support for the reliable transport of authentication protocols, and no more. EAP is a lock-step protocol which only supports a single packet in flight. As a result, EAP cannot efficiently transport bulk data, unlike transport protoc ...
... Since EAP does not require IP connectivity, it provides just enough support for the reliable transport of authentication protocols, and no more. EAP is a lock-step protocol which only supports a single packet in flight. As a result, EAP cannot efficiently transport bulk data, unlike transport protoc ...
Solving Electric Circuit ODE
... E(t) that is a constant 100 volt battery that drives the circuit for one second and then is disconnected. If the initial current is 0 amps when the switch is closed, then determine the current I(t) for any time t > 0 . [Suggestions: [a] Represent the EMF as a piecewise defined function and use the m ...
... E(t) that is a constant 100 volt battery that drives the circuit for one second and then is disconnected. If the initial current is 0 amps when the switch is closed, then determine the current I(t) for any time t > 0 . [Suggestions: [a] Represent the EMF as a piecewise defined function and use the m ...
Improved Protocols and Hardness Results for the Two
... The starting point for our work is the incomplete understanding of the two-player case. While the gap between upper and lower bound of 38 − 13 ≈ 0.04167 is small, our impression is that the current-best protocol achieving the 13 success probability in two rounds together with the abstract hardness r ...
... The starting point for our work is the incomplete understanding of the two-player case. While the gap between upper and lower bound of 38 − 13 ≈ 0.04167 is small, our impression is that the current-best protocol achieving the 13 success probability in two rounds together with the abstract hardness r ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... It is incorporated in to appropriate protocol layer Pervasive security mechanism Not specific to any protocol layer ...
... It is incorporated in to appropriate protocol layer Pervasive security mechanism Not specific to any protocol layer ...
Certification Exam Objectives: SY0-401
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...