CompTIA Security (SY0-401)
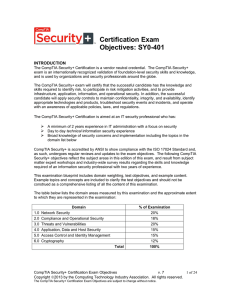
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
Extensions to the FTP Protocol
... SSH (Secure Shell) is a protocol which provides a secure means of logging into and executing commands on another network computer running Unix (or VMS), and transferring files between computers. It negotiates and establishes an encrypted connection between an SSH client and an SSH server, authentica ...
... SSH (Secure Shell) is a protocol which provides a secure means of logging into and executing commands on another network computer running Unix (or VMS), and transferring files between computers. It negotiates and establishes an encrypted connection between an SSH client and an SSH server, authentica ...
HCL/ALU
... Use voltage thresholds to extract discrete values from continuous signal – Simplest version: 1-bit signal ...
... Use voltage thresholds to extract discrete values from continuous signal – Simplest version: 1-bit signal ...
Document
... – iteration required in designs with branching and non-negligible wire C or RC – same convergence difficulties as in synthesis / placement problem ...
... – iteration required in designs with branching and non-negligible wire C or RC – same convergence difficulties as in synthesis / placement problem ...
Problems - UCF Local Programming Contest
... Given the original five numbers at the corners of a pentagon, output the Positive Pentagon that can be created by following this process. You may assume this process will always make a pentagon “pentastic” in at most 1000 steps. The Input: The first input line will contain only a single positive int ...
... Given the original five numbers at the corners of a pentagon, output the Positive Pentagon that can be created by following this process. You may assume this process will always make a pentagon “pentastic” in at most 1000 steps. The Input: The first input line will contain only a single positive int ...
IPSec
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
XML: Part - Houston Community College System
... Pretty Good Privacy (PGP) (continued) • Uses a passphrase to encrypt the private key on the local computer • Passphrase: – A longer and more secure version of a password – Typically composed of multiple words – More secure against dictionary attacks ...
... Pretty Good Privacy (PGP) (continued) • Uses a passphrase to encrypt the private key on the local computer • Passphrase: – A longer and more secure version of a password – Typically composed of multiple words – More secure against dictionary attacks ...
Chap 6: Web Security - IUP Personal Websites
... Pretty Good Privacy (PGP) (continued) • Uses a passphrase to encrypt the private key on the local computer • Passphrase: – A longer and more secure version of a password – Typically composed of multiple words – More secure against dictionary attacks ...
... Pretty Good Privacy (PGP) (continued) • Uses a passphrase to encrypt the private key on the local computer • Passphrase: – A longer and more secure version of a password – Typically composed of multiple words – More secure against dictionary attacks ...
Power-Delay Optimizations in Gate Sizing 1
... one combinational subcircuit at a time, and therefore, although the entire circuit may have a million or more gates, the number of variables in the sizing problem will be comfortably small. Previous approaches that have taken power considerations into account during transistor sizing include [4{8]. ...
... one combinational subcircuit at a time, and therefore, although the entire circuit may have a million or more gates, the number of variables in the sizing problem will be comfortably small. Previous approaches that have taken power considerations into account during transistor sizing include [4{8]. ...
Devireddy
... Wired Equivalent Privacy (WEP), a security protocol for wireless local area networks (WLANs) defined in the 802.11b standard. LANs are more secure than WLANs. WLANs, which are over radio waves are more vulnerable to tampering. WEP provides security by encrypting data ...
... Wired Equivalent Privacy (WEP), a security protocol for wireless local area networks (WLANs) defined in the 802.11b standard. LANs are more secure than WLANs. WLANs, which are over radio waves are more vulnerable to tampering. WEP provides security by encrypting data ...
Accurate and computer efficient modelling of - LaPSI
... Transient faults may be injected at different levels of abstraction by either altering the logic values or momentarily changing the voltage levels and charging states of the struck nodes. Lower level models may be obtained via device-level simulation of the effect of an ionising particle penetrating ...
... Transient faults may be injected at different levels of abstraction by either altering the logic values or momentarily changing the voltage levels and charging states of the struck nodes. Lower level models may be obtained via device-level simulation of the effect of an ionising particle penetrating ...
Consider the following problem
... These were the original models introduced by Charnes, Cooper and Rhodes in their paper in 1978. Immediately after the publication of this paper, the authors made a minor modification. In a conventional LP, the decision variables are non-negative – they can be either zero or positive. However, the au ...
... These were the original models introduced by Charnes, Cooper and Rhodes in their paper in 1978. Immediately after the publication of this paper, the authors made a minor modification. In a conventional LP, the decision variables are non-negative – they can be either zero or positive. However, the au ...
Spinglass
... The scalability of distributed protocols and systems is a major determinant of success in demanding systems. For example, consider the recent field-test of the Navy’s Cooperative Engagement Capability (CEC). During the period Sept. 13-27, 2000, this system (which offers an over-the-horizon cooperati ...
... The scalability of distributed protocols and systems is a major determinant of success in demanding systems. For example, consider the recent field-test of the Navy’s Cooperative Engagement Capability (CEC). During the period Sept. 13-27, 2000, this system (which offers an over-the-horizon cooperati ...
Pediatric Poisoning/Overdose GENERAL MANAGEMENT OF TOXIC
... 4. Identification of the substance (patient has been exposed to). EMT/SPECIALIST/PARAMEDIC 5. Alert receiving hospital if patient may present HAZMAT risk. 6. Sample of drug or substance and any medication or poison containers should be brought in with patient if it does NOT pose a risk to rescuers. ...
... 4. Identification of the substance (patient has been exposed to). EMT/SPECIALIST/PARAMEDIC 5. Alert receiving hospital if patient may present HAZMAT risk. 6. Sample of drug or substance and any medication or poison containers should be brought in with patient if it does NOT pose a risk to rescuers. ...
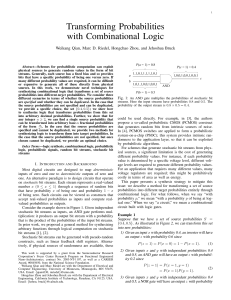
Transforming Probabilities with Combinational Logic
... synthesizing sequential state machines for this task. Motivated by problems in neural computation, Jeavons et al. considered the problem of transforming stochastic binary sequences through what they call “local algorithms:” fixed functions applied to concurrent bits in different sequences [11]. This ...
... synthesizing sequential state machines for this task. Motivated by problems in neural computation, Jeavons et al. considered the problem of transforming stochastic binary sequences through what they call “local algorithms:” fixed functions applied to concurrent bits in different sequences [11]. This ...
SNMP
... simple version of IP and UDP on their devices. Thus the software requirements are kept simple enough, and, can, in most cases, be stored in ROM. UDP is well suited to the brief request / response message used in network ...
... simple version of IP and UDP on their devices. Thus the software requirements are kept simple enough, and, can, in most cases, be stored in ROM. UDP is well suited to the brief request / response message used in network ...
Web Security Security+ Guide to Network Security Fundamentals
... Pretty Good Privacy (PGP) (continued) • Uses a passphrase to encrypt the private key on the local computer • Passphrase: – A longer and more secure version of a password – Typically composed of multiple words – More secure against dictionary attacks ...
... Pretty Good Privacy (PGP) (continued) • Uses a passphrase to encrypt the private key on the local computer • Passphrase: – A longer and more secure version of a password – Typically composed of multiple words – More secure against dictionary attacks ...
document
... potential pitfalls or "weak spots" in the VPN model can be easy to forget. These four concerns with VPN solutions are often raised. ...
... potential pitfalls or "weak spots" in the VPN model can be easy to forget. These four concerns with VPN solutions are often raised. ...
PK b
... set of size d , and let F {S1 ,..., Sk } be a family of subsets of G. We say that subset Si S j if S j cover Si . We say that family F is t -cover free over G if each subset in F is not covered by the union of t subsets in F . Moreover, we say that a family of subsets is q-uniform if all subsets ...
... set of size d , and let F {S1 ,..., Sk } be a family of subsets of G. We say that subset Si S j if S j cover Si . We say that family F is t -cover free over G if each subset in F is not covered by the union of t subsets in F . Moreover, we say that a family of subsets is q-uniform if all subsets ...
CHAPTER 1 Networking Concepts
... A form of cryptosystem in which encryption and decryption are performed using the same key This encryption scheme has five ingredients Plaintext: Readable message or data Encryption Algorithm: Performs various substitutions and transformations on the plaintext Secret Key: The secret key is also ...
... A form of cryptosystem in which encryption and decryption are performed using the same key This encryption scheme has five ingredients Plaintext: Readable message or data Encryption Algorithm: Performs various substitutions and transformations on the plaintext Secret Key: The secret key is also ...
Design Methods for Polymorphic Digital Circuits 1
... In order to illustrate the ad hoc approach we decided to design a polymorphic 5bit parity vs. Boolean symmetry circuit. The Boolean symmetry circuit returns log. 1 if the input vector is symmetric. Figure 2a shows the conventional implementations of these circuits as well as their composition in a s ...
... In order to illustrate the ad hoc approach we decided to design a polymorphic 5bit parity vs. Boolean symmetry circuit. The Boolean symmetry circuit returns log. 1 if the input vector is symmetric. Figure 2a shows the conventional implementations of these circuits as well as their composition in a s ...
ENGINE—7.3L DIESEL—GLOW PLUG CONTROL Article No
... or removal of the GPCM components, it is very important to re-run the KOER Glow Plug Monitor self test to verify no system faults are present before releasing the vehicle. For diagnostic procedures, refer to the new pinpoint test for the GPCM system (Figures 1-6). ...
... or removal of the GPCM components, it is very important to re-run the KOER Glow Plug Monitor self test to verify no system faults are present before releasing the vehicle. For diagnostic procedures, refer to the new pinpoint test for the GPCM system (Figures 1-6). ...
A Survey of BGP Security: Issues and Solutions
... ▫ Secure Path Vector: One-Time Signatures generated from Root Value ▫ Signature Amortization: One Signature for ...
... ▫ Secure Path Vector: One-Time Signatures generated from Root Value ▫ Signature Amortization: One Signature for ...
pdf
... 3. Identity-based signatures. In class we showed how to obtain an identity-based signature scheme: the master public key is a modulus N and an exponent e; the master secret key is d such that ed = 1 mod ϕ(N ). A user with identity ID is given secret key SKID = H(ID)d mod N (where H is modeled as a ...
... 3. Identity-based signatures. In class we showed how to obtain an identity-based signature scheme: the master public key is a modulus N and an exponent e; the master secret key is d such that ed = 1 mod ϕ(N ). A user with identity ID is given secret key SKID = H(ID)d mod N (where H is modeled as a ...