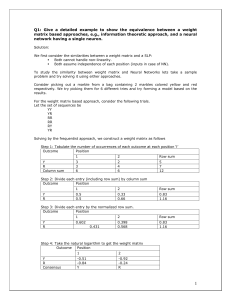
Lecture8_Dare
... If the target host is down, a variant on the TCP sequence number attack may be used Defense – A more secure means of validation, such as the Needham-Schroeder algorithm. TCP by itself is inadequate. – Essentially – don’t trust ident for anything important ...
... If the target host is down, a variant on the TCP sequence number attack may be used Defense – A more secure means of validation, such as the Needham-Schroeder algorithm. TCP by itself is inadequate. – Essentially – don’t trust ident for anything important ...
The Power of Epidemics: Robust Communication for Large-Scale Distributed Systems
... requests can arrive any more. Given that many protocols have no knowledge about the receivers, this certainty can never be achieved and they resort to a method called application level framing to require the application to reconstruct message for retransmission. This was applicable to some multi-use ...
... requests can arrive any more. Given that many protocols have no knowledge about the receivers, this certainty can never be achieved and they resort to a method called application level framing to require the application to reconstruct message for retransmission. This was applicable to some multi-use ...
Chapter 6
... • Hash algorithms are one-way functions. • A hash algorithm has these characteristics: – It uses no secret key – The message digest it produces cannot be inverted to produce the original information – The algorithm and information about how it works are publicly available – Hash collision are nearly ...
... • Hash algorithms are one-way functions. • A hash algorithm has these characteristics: – It uses no secret key – The message digest it produces cannot be inverted to produce the original information – The algorithm and information about how it works are publicly available – Hash collision are nearly ...
Assignment 2
... Weight Sharing: Overfitting is a drawback of a NN, where the NN memorizes the mapping between target and data. Overfitting occurs when the number of parameters is large, and subsets of parameters exclusively map to each training example. Hence an “optimal NN is the one that has minimal parameters”. ...
... Weight Sharing: Overfitting is a drawback of a NN, where the NN memorizes the mapping between target and data. Overfitting occurs when the number of parameters is large, and subsets of parameters exclusively map to each training example. Hence an “optimal NN is the one that has minimal parameters”. ...
Computer Network Security Protocols and Standards
... safeguard his or her privacy and security by maintaining the integrity of the circuits. This security is based on trust. ...
... safeguard his or her privacy and security by maintaining the integrity of the circuits. This security is based on trust. ...
Security
... developed public-key cryptography Asymmetric: – Private key – kept secret by owner – Public key – distributed freely to all who wish to send – Generated by computer algorithm, so a mathematical relation exists between them ... however ... – It is computationally difficult to determine the private ke ...
... developed public-key cryptography Asymmetric: – Private key – kept secret by owner – Public key – distributed freely to all who wish to send – Generated by computer algorithm, so a mathematical relation exists between them ... however ... – It is computationally difficult to determine the private ke ...
Chapter. 01
... link, or the disabling of the file management system. DOS - Denial of Service Attacks have ...
... link, or the disabling of the file management system. DOS - Denial of Service Attacks have ...
Data security based on multipath routing.
... Drawbacks of the protocol Diversity coding provides single line failure with only one extra line instantaneously without communicating with the transmitter. But this feature is not made use of in the protocol. A particular sequence has to be followed to get each message parts. If a message par ...
... Drawbacks of the protocol Diversity coding provides single line failure with only one extra line instantaneously without communicating with the transmitter. But this feature is not made use of in the protocol. A particular sequence has to be followed to get each message parts. If a message par ...
MODEL PENAL CODE
... indifference when the accidental killing occurs during the commission, or as an accomplice to, attempt to, or in flight from: robbery, rape, kidnapping, escape. c. First degree murder. In many jurisdictions, whether through statute or case law, an intentional killing done with premeditation and deli ...
... indifference when the accidental killing occurs during the commission, or as an accomplice to, attempt to, or in flight from: robbery, rape, kidnapping, escape. c. First degree murder. In many jurisdictions, whether through statute or case law, an intentional killing done with premeditation and deli ...
draft-gu-ppsp-tracker-protocol-02
... • Proposals: Add both in the message, IP is mandatory and PeerID is used if NO enough peers with public IP ...
... • Proposals: Add both in the message, IP is mandatory and PeerID is used if NO enough peers with public IP ...
Source Transformation, Thevenin and Norton Equivalents, OP AMP
... Thévenin’s theorem, as stated for sinusoidal AC circuits, is changed only to include the term impedance instead of resistance. Any two-terminal linear ac network can be replaced with an equivalent circuit consisting of a voltage source and an impedance in series. VTh is the Open circuit voltag ...
... Thévenin’s theorem, as stated for sinusoidal AC circuits, is changed only to include the term impedance instead of resistance. Any two-terminal linear ac network can be replaced with an equivalent circuit consisting of a voltage source and an impedance in series. VTh is the Open circuit voltag ...
Net+ Chapter 1
... encryption processes that are designed to provide authentication for users and services that need to communicate and be validated on a network. • Kerberos provides a way to prove identity in order to gain access to other network resources. • Kerberos works through the use of encrypted tickets and se ...
... encryption processes that are designed to provide authentication for users and services that need to communicate and be validated on a network. • Kerberos provides a way to prove identity in order to gain access to other network resources. • Kerberos works through the use of encrypted tickets and se ...
Insert Title Here
... Escrow mechanisms are a security hazard If required, perform at key generation, in the physical presence of humans Physically export Key Encryption Key and protect Export other keys encrypted with Key Encryption Key ...
... Escrow mechanisms are a security hazard If required, perform at key generation, in the physical presence of humans Physically export Key Encryption Key and protect Export other keys encrypted with Key Encryption Key ...
ECSP – EC-Council Certified Secure Programmer
... The bugs, defects and flaws that exist in software applications and programs present common vulnerabilities for malicious hackers to exploit. This EC-Council course teaches professional programmers who utilize Java and .NET frameworks to design and develop applications while adhering to secure codin ...
... The bugs, defects and flaws that exist in software applications and programs present common vulnerabilities for malicious hackers to exploit. This EC-Council course teaches professional programmers who utilize Java and .NET frameworks to design and develop applications while adhering to secure codin ...
2010-004.Basic gates.Wakerly.chpt2
... Product expression for small number of variables We will use these rules in the class for all kinds of reversible, quantum, optical, etc. logic. Try to remember them or put them to your “creepsheet”. ...
... Product expression for small number of variables We will use these rules in the class for all kinds of reversible, quantum, optical, etc. logic. Try to remember them or put them to your “creepsheet”. ...
Convertibility Verification and Converter Synthesis: Two Faces of the
... Student: Jie-Hong Jiang Mentor: Prof. Robert Brayton EE249 Class Project ...
... Student: Jie-Hong Jiang Mentor: Prof. Robert Brayton EE249 Class Project ...
IPSec (IP Security)
... Determine SA details (over SPI) Consult the SA Database to validate/decipher the packet Once validated/deciphered the appropriate action for the packet is determined and it is forwarded according to the rules in the SPD ...
... Determine SA details (over SPI) Consult the SA Database to validate/decipher the packet Once validated/deciphered the appropriate action for the packet is determined and it is forwarded according to the rules in the SPD ...