Chapter 1
... Sometimes the shared information is badintentioned and wants to share other information which should not be shared. ...
... Sometimes the shared information is badintentioned and wants to share other information which should not be shared. ...
Additive Relationship
... When a number is placed into the machine, the machine will use a rule to decide what the output should be. Watch as values are placed into the input-‐output machine. The results are recorded in ...
... When a number is placed into the machine, the machine will use a rule to decide what the output should be. Watch as values are placed into the input-‐output machine. The results are recorded in ...
Virtual Private Network(VPN)
... exchanges, to guarantee the identities of the two parties and avoid man-in-the-middle attacks data encryption standard (DES) and other bulk encryption algorithms for encrypting data keyed hash algorithms (HMAC, MD5, SHA) for ...
... exchanges, to guarantee the identities of the two parties and avoid man-in-the-middle attacks data encryption standard (DES) and other bulk encryption algorithms for encrypting data keyed hash algorithms (HMAC, MD5, SHA) for ...
Remote Access - York Technical College
... Process of encoding data using a mathematical algorithm that makes it difficult for unauthorized users to read the data if they intercept it. Encryption requires a key (math. Algorithm) to read the data. Two types of encryption ...
... Process of encoding data using a mathematical algorithm that makes it difficult for unauthorized users to read the data if they intercept it. Encryption requires a key (math. Algorithm) to read the data. Two types of encryption ...
coms3995 - Computer Science, Columbia University
... • Why do I see an hour glass or spinning beach ball? • How can I share the CPU so that I can still play a game while compiling a new Linux kernel? • What's a file system and how does it work? • How does the Internet work? • How does data get from sender to destination, and why doesn't it sometimes? ...
... • Why do I see an hour glass or spinning beach ball? • How can I share the CPU so that I can still play a game while compiling a new Linux kernel? • What's a file system and how does it work? • How does the Internet work? • How does data get from sender to destination, and why doesn't it sometimes? ...
Grade 8 Module 5
... x, there is a unique output of y. For Graph 2, the input of x=1 has two different outputs, y=0 and y=2, which means it cannot be a function. For Graph 3, it appears that each value of x has two outputs, one on the lower half of the circle and one on the upper half, ...
... x, there is a unique output of y. For Graph 2, the input of x=1 has two different outputs, y=0 and y=2, which means it cannot be a function. For Graph 3, it appears that each value of x has two outputs, one on the lower half of the circle and one on the upper half, ...
Review Questions
... 1. In information security a(n) _____ is the likelihood that a threat agent will exploit a vulnerability. A. attack B. threat C. risk D. exploitation 2. _____ is a systematic and structured approach to managing the potential for loss that is related to a threat. A. Asset management B. Risk assessmen ...
... 1. In information security a(n) _____ is the likelihood that a threat agent will exploit a vulnerability. A. attack B. threat C. risk D. exploitation 2. _____ is a systematic and structured approach to managing the potential for loss that is related to a threat. A. Asset management B. Risk assessmen ...
Nausea and Vomiting Protocol - Sunnybrook Center for Prehospital
... Medical Directives for ACPs ...
... Medical Directives for ACPs ...
The Cut-and-Choose Game and its Application to Cryptographic
... turn may depend on the function being computed as well as characteristics of specific deployment settings, such as software, hardware configuration and network condition, etc. This provides the ability to “tune” protocols to specific applications in a much more fine-grained way than before. We demon ...
... turn may depend on the function being computed as well as characteristics of specific deployment settings, such as software, hardware configuration and network condition, etc. This provides the ability to “tune” protocols to specific applications in a much more fine-grained way than before. We demon ...
L2-WM-3T5 Micro Prismatic Lens
... One of Corelite's latest additions to its line of architectural direct-indirect extruded fixtures, the Loft, features crisp modern lines with a new, ultra-high efficiency, clear micro-linear prismatic lens material to meet the tightest watts-per-square foot requirements. The Loft, with up to 95% fix ...
... One of Corelite's latest additions to its line of architectural direct-indirect extruded fixtures, the Loft, features crisp modern lines with a new, ultra-high efficiency, clear micro-linear prismatic lens material to meet the tightest watts-per-square foot requirements. The Loft, with up to 95% fix ...
pps
... Disadvantages clear, but: • Advantage: proof remains `property’ of prover and not automatically shared with verifier • Very important in cryptographic applications – Zero-knowledge • Many variants • Can be used to transform any protocol designed to work with benign players into one working with mali ...
... Disadvantages clear, but: • Advantage: proof remains `property’ of prover and not automatically shared with verifier • Very important in cryptographic applications – Zero-knowledge • Many variants • Can be used to transform any protocol designed to work with benign players into one working with mali ...
E2-WM-3T5 Micro Prismatic Lens
... One of Corelite's latest additions to its line of architectural direct-indirect extruded fixtures, the Element, features crisp modern lines with a new, ultra-high efficiency, clear micro-linear prismatic lens material to meet the tightest watts-per-square foot requirements. The Element, with up to 9 ...
... One of Corelite's latest additions to its line of architectural direct-indirect extruded fixtures, the Element, features crisp modern lines with a new, ultra-high efficiency, clear micro-linear prismatic lens material to meet the tightest watts-per-square foot requirements. The Element, with up to 9 ...
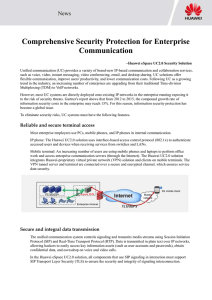
Comprehensive Security Protection for
... VPN tunnel server and terminal are connected over a secure and encrypted channel, which ensures service data security. ...
... VPN tunnel server and terminal are connected over a secure and encrypted channel, which ensures service data security. ...
Versatile Message Transport Protocol FLIP - royal hackeres 2010-14
... Connectionless protocol used in AMEOBA Distributed Systems Features are Transparency, Security, easy Network Management, Group Communication & C-S Communication Identifies entities as Network Service Access Points(NSAP’s) with location independent 64-bit identifier Sites on internetwork have mor ...
... Connectionless protocol used in AMEOBA Distributed Systems Features are Transparency, Security, easy Network Management, Group Communication & C-S Communication Identifies entities as Network Service Access Points(NSAP’s) with location independent 64-bit identifier Sites on internetwork have mor ...
Slide 1
... The origins of the Internet: ARPAnet The Internet was originally conceived by the Advanced Research Project Agency (ARPA) of the U.S. government in 1969 and was known as ARPAnet. It was designed to enable U.S. military leaders to stay in contact in case of a nuclear war. The protocol used in ARPAne ...
... The origins of the Internet: ARPAnet The Internet was originally conceived by the Advanced Research Project Agency (ARPA) of the U.S. government in 1969 and was known as ARPAnet. It was designed to enable U.S. military leaders to stay in contact in case of a nuclear war. The protocol used in ARPAne ...
Hardware Building Blocks and Encoding
... Internet for the telephone system as the underlying structure for communications. The trusted VPN components of the new VPN still do not offer security but they give customers a way to easily create network segments for wide area networks (WANs). On the other hand, the secure VPN components can be c ...
... Internet for the telephone system as the underlying structure for communications. The trusted VPN components of the new VPN still do not offer security but they give customers a way to easily create network segments for wide area networks (WANs). On the other hand, the secure VPN components can be c ...
PPT Version
... – IAPP now an 802.11f Recommended Practice. – But depends heavily on IETF protocols (RADIUS, UDP) so not strictly L2 protocol. ...
... – IAPP now an 802.11f Recommended Practice. – But depends heavily on IETF protocols (RADIUS, UDP) so not strictly L2 protocol. ...
Enhancing the Security and Capacity of Collaborative Software for
... group members. Reliable Multicast Protocol [2] is a reliable multicast transport protocol offering a variety of services of different quality. It is used in the reduction of multicast retransmission and congestion avoidance. Figure 1 shows a layered architecture of RMTP. The RMP makes use of the IP ...
... group members. Reliable Multicast Protocol [2] is a reliable multicast transport protocol offering a variety of services of different quality. It is used in the reduction of multicast retransmission and congestion avoidance. Figure 1 shows a layered architecture of RMTP. The RMP makes use of the IP ...
10 March 2009 - Computer Science
... The use of cryptographic protocols as a means to provide security to web servers and applications at the transport layer is becoming increasingly popular. However it is difficult to analyze this sort of traffic as it is encrypted •ISP's are often served with court orders to provide logs of clients a ...
... The use of cryptographic protocols as a means to provide security to web servers and applications at the transport layer is becoming increasingly popular. However it is difficult to analyze this sort of traffic as it is encrypted •ISP's are often served with court orders to provide logs of clients a ...
example design
... something we encourage you to do, and other thing completely different is to write VHDL code that has to be easily analysed and assessed by your team mates and the instructor in very short time. This is why all the class has to follow a very tight coding conventions or styles. Therefore, to translat ...
... something we encourage you to do, and other thing completely different is to write VHDL code that has to be easily analysed and assessed by your team mates and the instructor in very short time. This is why all the class has to follow a very tight coding conventions or styles. Therefore, to translat ...
Security and Privacy in Sensor Networks: Research Challenges
... POOR state of understanding Needed by services and applications ...
... POOR state of understanding Needed by services and applications ...
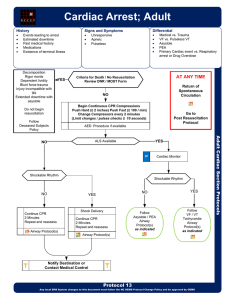
Cardiac Arrest
... Adult Cardiac Section Protocols Pearls · Efforts should be directed at high quality and continuous compressions with limited interruptions and early defibrillation when indicated. Consider early IO placement if available and / or difficult IV access anticipated. · DO NOT HYPERVENTILATE: If no advanc ...
... Adult Cardiac Section Protocols Pearls · Efforts should be directed at high quality and continuous compressions with limited interruptions and early defibrillation when indicated. Consider early IO placement if available and / or difficult IV access anticipated. · DO NOT HYPERVENTILATE: If no advanc ...
Investigating shape representation in human visual cortex
... can learn appropriate behaviors when embedded in a closed-loop system (input: sensory, output: action)? • Example: – learn to play Pong based on raw video input – or maybe more vision-type stuff ...
... can learn appropriate behaviors when embedded in a closed-loop system (input: sensory, output: action)? • Example: – learn to play Pong based on raw video input – or maybe more vision-type stuff ...