* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 24 - William Stallings, Data and Computer
Quantum key distribution wikipedia , lookup
Web of trust wikipedia , lookup
Cryptography wikipedia , lookup
Information security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Authentication wikipedia , lookup
Electronic authentication wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Access control wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Computer security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Mobile security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Wireless security wikipedia , lookup
Unix security wikipedia , lookup
Secure multi-party computation wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
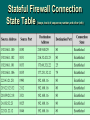
Data and Computer Communications Chapter 24 – Computer and Network Security Techniques Ninth Edition by William Stallings Data and Computer Communications, Ninth Edition by William Stallings, (c) Pearson Education - Prentice Hall, 2011 Computer and Network Security Techniques To guard against the baneful influence exerted by strangers is therefore an elementary dictate of savage prudence. Hence before strangers are allowed to enter a district, or at least before they are permitted to mingle freely with the inhabitants, certain ceremonies are often performed by the natives of the country for the purpose of disarming the strangers of their magical powers, or of disinfecting, so to speak, the tainted atmosphere by which they are supposed to be surrounded. —The Golden Bough Sir James George Frazer —The Art of War Sun Tzu Virtual Private Networks and IPSEC IPSEC provides three main facilities: an authentication-only function called the Authentication Header (AH) combined authentication/encryption function called Encapsulating Security Payload (ESP) key exchange functionality Transport & Tunnel Modes ESP supports two modes of use: Transport • which provides protection for upper-layer protocols • typically used for end-to-end communication between two hosts Tunnel • which provides protection to the entire IP packet • used when at least one of the two ends is a security gateway ESP Encryption and Authentication Example of Tunnel Mode Host A IPSEC Processing Needed? Outer IP Header is Stripped Host B Key Management IPSEC key management involves the determination and distribution of secret keys. IPSEC supports 2 types of key management • Manual – requires a system administrator to manually configure the systems and corresponding keys • Automated – no human intervention needed and enables on-demand creation of keys IPSEC and VPNs there is a driving need for users and organizations to be able to: secure their networks receive traffic over the internet while still meeting the need to secure the network Ipsec and VPNs IPsec provides the • can be implemented in routers or firewalls owned network and operated by the manager organization with • a service provider can simplify the job of planning, complete implementing, and control over maintaining Internet-based the security VPNs for secure access and aspects of secure communication VPN Application layer security SSL – Secure Socket Layer general purpose service designed to provide a reliable end-to-end secure service set of protocols that relies on TCP • could be provided as part of the underlying protocol suite and transparent to applications • can be embedded in specific packages TLS – Transport Layer Security RFC 2246 basically an updated service from SSL that provides reliable endto-end secure data transfer SSL Architecture (Two Important SSL Concepts) SSL Connection • transport that provides a suitable type of service • peer-to-peer and transient SSL Session • association between client and server • created by handshake protocol SSL Record Protocol MAC= message authentification code Change Cipher Spec Protocol (see Fig. 24.2 shown previously) the simplest of the three SSL-specific protocols makes use of the SSL Record Protocol consists of a single message, which consists of a single byte with the value 1 sole purpose is to cause the pending state to be copied into the current state Alert and Handshake Protocols (see Fig. 24.2 shown previously) Alert Protocol (ex. Incorrect MAC) conveys SSL related alerts to the peer entity compressed and encrypted Handshake Protocol most complex part of SSL allows server and client to authenticate negotiates encryption and MAC algorithm as well as the keys used before the transmission of any application data Wi-Fi Protected Access Wi-Fi Protected Access is also known as WPA is the Wi-Fi standard a set of security mechanisms created to accelerate the introduction of strong security into WLANs WPA Based on the IEEE 802.11i standard addresses 3 main security areas Authentication Key management Data transfer privacy requires the use of an Authentication Server (AS) PSK (pre-shared key) does not require an AS defines a more robust authentication protocol Supports AES with 128-bit keys and 104bit RC4 encryption 802.11i Operational Phases 3 Main Ingredients for WPA Access Control 802.11i Access Control Privacy with Message Integrity IEEE 80211i defines two schemes both add a message integrity code (MIC) to the 802.11 MAC Frame Temporal Key Integrity Protocol (TKIP) • WPA-1 • only requires software changes to devices implemented with WEP Counter Mode – CBC MAC Protocol (CCMP) • WPA-2 • makes use of AES protocol Intrusion Detection Intrusion Detection RFC 2828 Security Intrusion • a security event, or combination of multiple security events, that constitutes a security incident in which an intruder gains, or attempts to gain access to a system without having authorization to do so Intrusion Detection • a security service that monitors and analyzes system events for the purpose of finding, and providing real-time or near-real-time warning of, attempts to access system resources in an unauthorized manner Intrusion Detection (IDS) IDS Host Based monitors characteristics of events on a single host network based monitors characteristics of events on the network IDS Components Sensors • collect data Analyzers User Interface • analyze the collected data to see if an intrusion has occurred • enables a user to view the sensor output and the completed analysis output Basic Principles of Countering Intrusions Intruder Behavior Profiling Host-Based IDS Techniques can detect both external and internal intrusions. Anomaly Detection • collecting a baseline and then comparing behavior against that baseline Signature Detection • defines a set of rules or attack patterns Firewalls integral part of an organization’s defense-in-depth strategy as well as an important complement to an organization’s IDS. typically thought of as perimeter protection “defense in depth” an Firewall Characteristics all traffic passes through the firewall only authorized traffic is allowed to pass the firewall itself is immune to penetration assumes a hardened system with a secured operating system Firewall Control Access Techniques Service Control • determines types of internet services that can be accessed both inbound and outbound Direction Control • determines the direction in which particular service requests may be initiated User Control • access to service is controlled based on user’s identity Behavior Control • controls how a particular service can be used Firewall Limitations cannot protect against attacks that bypass the firewall (i.e. a modem pool) may not fully protect against internal threats cannot guard against wireless communications between local systems on different sides of the internal firewall cannot protect against mobile devices that plug directly into the internal network Types of Firewalls Packet Filtering Firewall • applies a set of rules to each incoming and outgoing IP packet Stateful Inspection Firewall • tightens up the rules for TCP traffic by creating a directory of outbound TCP connections. Application Level Gateway • application proxy, acts as a relay of application level traffic Circuit Level Gateway • sets up two TCP connections and relays TCP segments from one connection to the other Types of Firewalls PacketFiltering Examples Packet Filtering Firewalls Advantages: its simplicity transparent to users very fast Disadvantages: cannot prevent attacks to application specific vulnerabilities do not support advanced user authentication schemes vulnerable to attacks that take advantage of problems within TCP/IP susceptible to security breaches caused by improper configurations Stateful Firewall Connection State Table (keeps track of sequence number and other info) Application-Level Gateway also called an application proxy, acts as a relay of application-level traffic tend to be more secure than packet filters easy to log and audit all incoming traffic Disadvantage: additional processing overhead on each connection Circuit-Level Gateway circuit-level proxy stand alone system or function performed by an application-level gateway sets up two TCP connections security function consists of determining which connections will be allowed used where the system administrator trusts the internal users Malware Defense Prevention is the primary goal for malware defense. However when prevention is not possible we want to: Detect Identify Remove Anti-virus the above software is designed to do all of Anti-Virus Generic Decryption (GD) GD is technology that enables anti-virus programs to detect even the most complex polymorphic viruses. A GD scanner contains: • CPU Emulator • Virus Signature Scanner • Emulation Control Module Digital Immune System Behavior-Blocking Software Types of behavior being monitored are: integrates with the operating system of a host computer and monitors program behavior in real time. • attempts to open, view, delete or modify files • attempts to format or otherwise erase disks • modifications to the logic of macro or executable files • modifications of critical system settings • unauthorized scripting Behavior Blocking Generality Timeliness • should be able to handle a wide variety of worm attacks • approach should respond quickly to limit infected systems Resiliency Minimal denial-ofservice costs • should be resistant to techniques by to evade worm Transparency • should not require modification to existing OS and hardware • minimal reduction in capacity or service due to countermeasure Global and local coverage • should be able to deal with attack sources from inside and outside (6 Classes of Worm Defense) Signature-based scanning & filtering Filter-based containment Payload-classification based worm containment Threshold Random Walk (TRW) scan detection Rate Limiting Rate Halting Summary VPNs transport and tunnel modes SSL and TLS architecture and protocol Wi-Fi and IPsec protected access access control and privacy Intrusion detection Firewalls characteristics and types Malware Defense worm countermeasures