* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download D`Amo - softfarm
Next-Generation Secure Computing Base wikipedia , lookup
Access control wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Wireless security wikipedia , lookup
Information security wikipedia , lookup
Information privacy law wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Cryptography wikipedia , lookup
History of cryptography wikipedia , lookup
Mobile security wikipedia , lookup
Social engineering (security) wikipedia , lookup
Security-focused operating system wikipedia , lookup
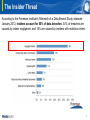
D’Amo, Comprehensive DB Encryption Solution Table of Contents The Need for Effective Database Security - Database: The Ultimate Target - Lack of Database Protection (Statistics) An Introduction to D’Amo - Database Security: Encryption - Key Benefits of Encryption - Introduction to D’Amo - D’Amo: Comprehensive DB Security - Regulatory Compliance 1 The Need for Effective Database Security Databases: The Ultimate Target When people think of hacking, they often picture hackers damaging websites. While this is indeed a common occurrence, the ultimate goal of many hackers i s to gain access to the wealth of information contained within electronic databases. Information contained within databases can include: • Client Personal Information (Name, SSN, credit card numbers) • Bank Account Information • Sales Revenue for Individual Products • Payroll Information • A Company Strategic Plans • Defense System Information • Intellectual Property • Test and Performance Results • And much, much more… 3 The Insider Threat According to the Ponemon Institute’s Aftermath of a Data Breach Study, released January 2012, insiders account for 50% of data breaches. 34% of breaches are caused by insider negligence, and 16% are caused by insiders with malicious intent. 4 Lack of Database Protection Only 30% of companies encrypt personal data in their databases 75% of companies lack proper database access controls Only 50% of companies consider database security a high priority ~ 2010 Independent Oracle Users Group Data Security Report “Some data managers feel that their data is secure mainly because databases are not connected to the Internet—a false comfort that may lead to a rude awakening.” ~2010 Independent Oracle Users Group Data Security Report 5 An Introduction to D’Amo: Comprehensive Database Encryption Solution Introduction to D’Amo Comprehensive Database Security Solution D’Amo, Comprehensive DB Security Solution, provides not only encryption but also access control, and auditing. D’Amo has been No.1 in the Korean DB encryption market, having 80% of the market share since March 2004. Encryption Access Control Separation of Duty Comprehensive Database Security Solution Auditing Reporting Comprehensive DB Security Solution, D'Amo 7 D’Amo: Encryption by Column Encryption • D’Amo minimizes overhead by encrypting critical data columns only. • Encryption and decryption processes are performed using a PKI-based symmetric key cryptosystem. • Supports international encryption algorithm standards (DES, Triple DES, AES, etc…) • Operation modes can be either Cipher Block Chaining (CBC) or Cipher Feedback (CFB), depending on algorithm and the Security Manager’s preference. 8 D’Amo: Column Access Control Column Access Control • D’Amo enables column access control, selective application of encryption/decryption privileges, and application of access policies to internal and external users. 9 D’Amo: Separation of Authority Separation of Authority • D’Amo enables strict separation of authority between the Security Manager and the Database Administrator. 10 Regulatory Compliance Payment Card Industry Data Security Standard (PCI DSS, 2004) is an international information security standard for companies dealing with electronic payment transactions (credit cards, debit cards, etc.). • Requires secure management of cardholder data. • Fines for violations can range from $5000-$100,000 USD per month. Federal Information Processing Standard (FIPS) is a set of standards required by the United States Federal Government for use in computer systems used by government agencies and contractors. • Well-known FIPS standards include the Data Encryption Standard (DES) and the Advanced Encryption Standard (AES). • The international equivalent of FIPS is the International Organization for Standardization (ISO). 11 Thank You! Japan Penta Security Systems Corporation Ascend Akasaka Bldg. 3F Minato-ku, Tokyo 107-0052 , Japan TEL: 81-3-5573-8191 : FAX: 81-3-5573-193 3 URL: www.pentasecurity.co.jp Email: [email protected] Republic of Korea Penta Secuirty Sytems Corporation Hanjin Shipping Building 20F 25-11 Yoido-dong, Youngdeungpo-ku, Seoul, Republic of Korea TEL: 82-2-780-7728 : FAX: 82-2-786-5281 URL: www.pentasecurity.com