Chapter 02: The Need for Security
... or destroy equipment. _________________________ ANS: F, spike PTS: 1 6. The shoulder looking technique is used in public or semipublic settings when individuals gather information they are not authorized to have by looking over another individual’s shoulder or viewing the information from a distance ...
... or destroy equipment. _________________________ ANS: F, spike PTS: 1 6. The shoulder looking technique is used in public or semipublic settings when individuals gather information they are not authorized to have by looking over another individual’s shoulder or viewing the information from a distance ...
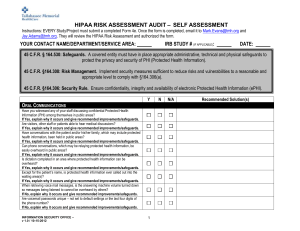
Form 4e HIPAA Risk Assessment Survey
... If No, explain why it occurs and give recommended improvements/safeguards. Are workstations turned off after business hours? If No, explain why it occurs and give recommended improvements/safeguards. Do staff protect their IDs and passwords and never share them? If No, explain why it occurs and give ...
... If No, explain why it occurs and give recommended improvements/safeguards. Are workstations turned off after business hours? If No, explain why it occurs and give recommended improvements/safeguards. Do staff protect their IDs and passwords and never share them? If No, explain why it occurs and give ...
3 Responding to Incidents
... Incidents that occur with SSAW IS, the Director must notify the AFMS Privacy Office Director via telephone. Immediately afterwards, the IS Director will follow up with an e-mail to the AFMS Privacy Office, and complete the AFMS Information Assurance Computer Incident Reporting Form found in Section ...
... Incidents that occur with SSAW IS, the Director must notify the AFMS Privacy Office Director via telephone. Immediately afterwards, the IS Director will follow up with an e-mail to the AFMS Privacy Office, and complete the AFMS Information Assurance Computer Incident Reporting Form found in Section ...
The Real Cost of Free Programs such as Instant
... protocols. Fasttrack, used by KaZaA and others; Gnutella, which is both a protocol and a client; and WinMX. In addition to the threats below, these programs often come loaded with spyware. Since these products are not developed or published by major companies like Netscape, Microsoft and Yahoo, like ...
... protocols. Fasttrack, used by KaZaA and others; Gnutella, which is both a protocol and a client; and WinMX. In addition to the threats below, these programs often come loaded with spyware. Since these products are not developed or published by major companies like Netscape, Microsoft and Yahoo, like ...
Lecture Notes - Computer Science & Engineering
... Damage of the target may not reflect the real amount of damage Services may rely on the attacked service, causing a cascading and escalating damage Need: support for decision makers to – Evaluate risk and consequences of cyber attacks – Support methods to prevent, deter, and mitigate ...
... Damage of the target may not reflect the real amount of damage Services may rely on the attacked service, causing a cascading and escalating damage Need: support for decision makers to – Evaluate risk and consequences of cyber attacks – Support methods to prevent, deter, and mitigate ...
Remote Access—Attack Vectors
... Another recent vulnerability in this area is related to clientless VPN products. These devices retrieve content from different sites and then serve the data so it appears to be from the SSL VPN. This circumvents same-origin restrictions. A same-origin policy is designed to enforce trust domains and ...
... Another recent vulnerability in this area is related to clientless VPN products. These devices retrieve content from different sites and then serve the data so it appears to be from the SSL VPN. This circumvents same-origin restrictions. A same-origin policy is designed to enforce trust domains and ...
Chapter 10
... Threats to the Physical Security of Internet Communications Channels • Internet’s packet-based network design – Precludes it from being shut down • By attack on single communications link ...
... Threats to the Physical Security of Internet Communications Channels • Internet’s packet-based network design – Precludes it from being shut down • By attack on single communications link ...
Risk Analysis - University at Albany
... – determination of state of risk associated with a system based upon thorough analysis – includes recommendations to support subsequent security controls/decisions. – takes into account business, as well as legal constraints. ...
... – determination of state of risk associated with a system based upon thorough analysis – includes recommendations to support subsequent security controls/decisions. – takes into account business, as well as legal constraints. ...
CH9
... threat exploits a vulnerability fraud Any business activity that uses deceitful practices or devices to deprive another of property or other rights malware (malicious software) A generic term for malicious software phishing A crimeware technique to steal the identity of a target company to get ...
... threat exploits a vulnerability fraud Any business activity that uses deceitful practices or devices to deprive another of property or other rights malware (malicious software) A generic term for malicious software phishing A crimeware technique to steal the identity of a target company to get ...
Malicious Threats - The University of Texas at Dallas
... for changes which might signify an attack by an unknown virus. Cryptographic Checksummers use an encryption algorithm to lessen the risk of being fooled by a virus which targets that particular checksummer. Monitor/Behavior Blocker - a TSR that monitors programs while they are running for behavior w ...
... for changes which might signify an attack by an unknown virus. Cryptographic Checksummers use an encryption algorithm to lessen the risk of being fooled by a virus which targets that particular checksummer. Monitor/Behavior Blocker - a TSR that monitors programs while they are running for behavior w ...
Malicious Threats - The University of Texas at Dallas
... for changes which might signify an attack by an unknown virus. Cryptographic Checksummers use an encryption algorithm to lessen the risk of being fooled by a virus which targets that particular checksummer. Monitor/Behavior Blocker - a TSR that monitors programs while they are running for behavior w ...
... for changes which might signify an attack by an unknown virus. Cryptographic Checksummers use an encryption algorithm to lessen the risk of being fooled by a virus which targets that particular checksummer. Monitor/Behavior Blocker - a TSR that monitors programs while they are running for behavior w ...
6. Basic concept of the Cybersecurity Information Exchange
... the actual sources of attacks, i.e. bot-herders and the like, viewing only one type of information, no matter what the one type is, has proven ineffective in countering the threat. Information that is available is often of such disparate nature that trying to coordinate and correlate available infor ...
... the actual sources of attacks, i.e. bot-herders and the like, viewing only one type of information, no matter what the one type is, has proven ineffective in countering the threat. Information that is available is often of such disparate nature that trying to coordinate and correlate available infor ...
Vulnerability Management: Tools, Challenges and Best Practices
... The challenges of information management are typically related to the breadth and depth of the information being gathered and shared, and the methods by which they are shared. It becomes difficult for organizations to manage the flow of new security related information in and out of the company. Thi ...
... The challenges of information management are typically related to the breadth and depth of the information being gathered and shared, and the methods by which they are shared. It becomes difficult for organizations to manage the flow of new security related information in and out of the company. Thi ...
Governance Guidance
... In today’s globally networked business environment, the significance of information and corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise in ...
... In today’s globally networked business environment, the significance of information and corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise in ...
Governance Guidance - Top Actions
... In today’s globally networked business environment, the significance of information and corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise in ...
... In today’s globally networked business environment, the significance of information and corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise in ...
Governance Guidance - Top Actions
... In today’s globally networked business environment, the significance of information and corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise in ...
... In today’s globally networked business environment, the significance of information and corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise in ...
8. Enabling cybersecurity information exchange
... CIRTs and the operators or vendors of equipment, software or network based systems. The cybersecurity information exchanged is valuable for achieving enhanced cybersecurity and infrastructure protection, as well as accomplishing the principal functions performed by CIRTs. The exchange of cybersecuri ...
... CIRTs and the operators or vendors of equipment, software or network based systems. The cybersecurity information exchanged is valuable for achieving enhanced cybersecurity and infrastructure protection, as well as accomplishing the principal functions performed by CIRTs. The exchange of cybersecuri ...
Cengage Learning 2013
... • Application error • Occurs when more data is sent to a buffer than it can handle • Attacker can take advantage of the consequence of the failure ...
... • Application error • Occurs when more data is sent to a buffer than it can handle • Attacker can take advantage of the consequence of the failure ...
Threats To Windows Users and Countermeasures
... months before the attack. Another DDOS tool known as "Knight" was found on approximately 1500 hosts as reported by CERT Advisory CA-2001-20. This tool also uses IRC as the control channel. ...
... months before the attack. Another DDOS tool known as "Knight" was found on approximately 1500 hosts as reported by CERT Advisory CA-2001-20. This tool also uses IRC as the control channel. ...
Intrusion Detection System(IDS) Overview
... firewalls, virus scanners, authentication systems, VPN etc.. Given their role, these are prime targets and being managed by humans, they are error prone. Failure of one of these tools will jeopardize the security!. ...
... firewalls, virus scanners, authentication systems, VPN etc.. Given their role, these are prime targets and being managed by humans, they are error prone. Failure of one of these tools will jeopardize the security!. ...
Information Technology (IT) Security Policy
... The provision of facilities for information backups on network file servers and other centralized information stores but excluding backups of the hard disks on individual computers; ...
... The provision of facilities for information backups on network file servers and other centralized information stores but excluding backups of the hard disks on individual computers; ...
Application Security
... • All these settings should be defined, implemented, and maintained as many are not shipped with secure defaults. This includes keeping all software up to date, including all code libraries used by the application. ...
... • All these settings should be defined, implemented, and maintained as many are not shipped with secure defaults. This includes keeping all software up to date, including all code libraries used by the application. ...
Application of CYBEX (Cybersecurity Information Exchange)
... CYBEX – techniques for the new paradigm Weakness, vulnerability and state Event, incident, and heuristics Information exchange policy Identification, discovery, and query Identity assurance Exchange protocols ...
... CYBEX – techniques for the new paradigm Weakness, vulnerability and state Event, incident, and heuristics Information exchange policy Identification, discovery, and query Identity assurance Exchange protocols ...
Social engineering (security)

Social engineering, in the context of information security, refers to psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional ""con"" in that it is often one of many steps in a more complex fraud scheme.The term ""social engineering"" as an act of psychological manipulation is also associated with the social sciences, but its usage has caught on among computer and information security professionals.