Chapter 5 Protection of Information Assets
... – Banning all use of transportable drives in the security policy – Where no authorized use of USB ports exists, disabling use with a logon script which removes them from the system directory – If they are considered necessary for business use, encrypting all data transported or saved by these device ...
... – Banning all use of transportable drives in the security policy – Where no authorized use of USB ports exists, disabling use with a logon script which removes them from the system directory – If they are considered necessary for business use, encrypting all data transported or saved by these device ...
Understanding the Methods of Network Attacks
... Also notice the use of a Network-based Intrusion Detection System (NIDS), a Network Intrusion Prevention System (NIPS), and a Host-based Intrusion Prevention System (HIPS). All three of these mitigation strategies look for malicious traffic and can alert or drop such traffic. However, these strategi ...
... Also notice the use of a Network-based Intrusion Detection System (NIDS), a Network Intrusion Prevention System (NIPS), and a Host-based Intrusion Prevention System (HIPS). All three of these mitigation strategies look for malicious traffic and can alert or drop such traffic. However, these strategi ...
Security+ Guide to Network Security Fundamentals, Third
... Information security is by its very nature complex Complex security systems can be hard to understand, troubleshoot, and feel secure about As much as possible, a ________________ ____________________________________ __________________ for a potential attacker ...
... Information security is by its very nature complex Complex security systems can be hard to understand, troubleshoot, and feel secure about As much as possible, a ________________ ____________________________________ __________________ for a potential attacker ...
Lecture1
... this protocol. Its designers aimed primarily at a client–server model, and it provides mutual authentication — both the user and the server verify each other's identity. Kerberos protocol messages are protected against eavesdropping and replay attacks. 0 Kerberos builds on symmetric key cryptography ...
... this protocol. Its designers aimed primarily at a client–server model, and it provides mutual authentication — both the user and the server verify each other's identity. Kerberos protocol messages are protected against eavesdropping and replay attacks. 0 Kerberos builds on symmetric key cryptography ...
Information Security Incident Management
... • Senior Consultant of Above Security • Operations in Montreal, Ottawa, Toronto and Bahamas working with 160 customers in 11 countries ...
... • Senior Consultant of Above Security • Operations in Montreal, Ottawa, Toronto and Bahamas working with 160 customers in 11 countries ...
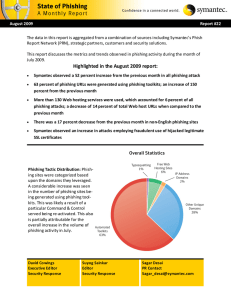
Highlighted in the August 2009 report
... from phishing toolkits that randomize their URL string are observed to point to the same Web page and do not contain a unique Web page in each URL. Unique Phishing websites are the ones where each attack is categorized on distinct Web Pages. Web-Hosting: Type of Internet hosting service which allows ...
... from phishing toolkits that randomize their URL string are observed to point to the same Web page and do not contain a unique Web page in each URL. Unique Phishing websites are the ones where each attack is categorized on distinct Web Pages. Web-Hosting: Type of Internet hosting service which allows ...
Computer Security, Ethics, and Privacy
... What is a denial of service attack and back door? A denial of service attack is an assault which disrupts computer access to an Internet service such as the Web or e-mail ...
... What is a denial of service attack and back door? A denial of service attack is an assault which disrupts computer access to an Internet service such as the Web or e-mail ...
Security Assessment Questionnaire
... performed with or without detailed prior knowledge of the environment. When it is performed without prior knowledge additional steps will be taken to enumerate hosts and applications and to assess the ease with which any outsider could exploit publicly available information or social engineering to ...
... performed with or without detailed prior knowledge of the environment. When it is performed without prior knowledge additional steps will be taken to enumerate hosts and applications and to assess the ease with which any outsider could exploit publicly available information or social engineering to ...
Cutting Edge VoIP Security Issues Color
... Attacks against media gateways can affect all external traffic and/or generate large amounts of toll fraud ...
... Attacks against media gateways can affect all external traffic and/or generate large amounts of toll fraud ...
Discovering Computers 2006
... A back door is a program or set of instructions in a program that allow users to bypass security controls when accessing a computer resource ...
... A back door is a program or set of instructions in a program that allow users to bypass security controls when accessing a computer resource ...
What is Security?
... a high volume of vulnerabilities in the network infrastructure embarrassingly poor protocols. Hackers are exploiting these software bugs, which are sometimes easy to fix, eavesdropping and intercepting communication data with increasing ease. ...
... a high volume of vulnerabilities in the network infrastructure embarrassingly poor protocols. Hackers are exploiting these software bugs, which are sometimes easy to fix, eavesdropping and intercepting communication data with increasing ease. ...
information Security Blueprint
... – Does not apply to internal attacks from employee threats or on-site physical threats ...
... – Does not apply to internal attacks from employee threats or on-site physical threats ...
Principals of Information Security, Fourth Edition
... Attacks (cont’d.) • Types of attacks (cont’d.) – Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network – Phishing: an attempt to gain personal/financial information from individual, usually by posi ...
... Attacks (cont’d.) • Types of attacks (cont’d.) – Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network – Phishing: an attempt to gain personal/financial information from individual, usually by posi ...
6 - Department of Accounting and Information Systems ACIS | Pamplin
... Installing Internetwork connections requires leased lines or other data channels; these connections are usually secured under requirements of formal service agreement When individuals seek to connect to organization’s network, more flexible option must be provided Options such as virtual priva ...
... Installing Internetwork connections requires leased lines or other data channels; these connections are usually secured under requirements of formal service agreement When individuals seek to connect to organization’s network, more flexible option must be provided Options such as virtual priva ...
Key To Personal Information Security
... (LAN) or Internet run many services that listen at well-known and not so well known ports • By port scanning, the attacker finds which ports are available (i.e., what service might be listing to a port) • A port scan consists of sending a message to each port, one at a time • The kind of response re ...
... (LAN) or Internet run many services that listen at well-known and not so well known ports • By port scanning, the attacker finds which ports are available (i.e., what service might be listing to a port) • A port scan consists of sending a message to each port, one at a time • The kind of response re ...
Colinwatson-a-new-ontology-of-unwanted-automation
... • No coverage of implementation bugs • All the threats must require the web to exist for the threat to be materialised; thus attacks that can be achieved without the web are out of scope. Malicious Automation ...
... • No coverage of implementation bugs • All the threats must require the web to exist for the threat to be materialised; thus attacks that can be achieved without the web are out of scope. Malicious Automation ...
AISE PoIS4E_PP_ch02_48
... traveling over network; can be used both for legitimate purposes and for stealing information from a network – Phishing تصيد احتيالي: an attempt to gain personal/financial information from individual, usually by posing as legitimate entity – Pharming : redirection of legitimate Web traffic (e.g., ...
... traveling over network; can be used both for legitimate purposes and for stealing information from a network – Phishing تصيد احتيالي: an attempt to gain personal/financial information from individual, usually by posing as legitimate entity – Pharming : redirection of legitimate Web traffic (e.g., ...
Essentials of Business Information Systems Chapter 7 Securing
... System Vulnerability and Abuse Hackers and Computer Crime • Computer crime • Defined as “any violations of criminal law that involve a knowledge of computer technology for their perpetration, investigation, or prosecution” • Computer may be target of crime, e.g.,: • Breaching confidentiality of prot ...
... System Vulnerability and Abuse Hackers and Computer Crime • Computer crime • Defined as “any violations of criminal law that involve a knowledge of computer technology for their perpetration, investigation, or prosecution” • Computer may be target of crime, e.g.,: • Breaching confidentiality of prot ...
Principals of Information Security, Fourth Edition
... Attacks (cont’d.) • Types of attacks (cont’d.) – Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network – Phishing: an attempt to gain personal/financial information from individual, usually by posi ...
... Attacks (cont’d.) • Types of attacks (cont’d.) – Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network – Phishing: an attempt to gain personal/financial information from individual, usually by posi ...
MASTER - HubSpot
... Security Standards, to the extent applicable. The Security Standards may require that you engage an approved third party vendor to conduct quarterly perimeter scans and/or security reviews can be accessed through Visa and Mastercard websites at www.Visa.com and www.MasterCard.com ...
... Security Standards, to the extent applicable. The Security Standards may require that you engage an approved third party vendor to conduct quarterly perimeter scans and/or security reviews can be accessed through Visa and Mastercard websites at www.Visa.com and www.MasterCard.com ...
Lecture12
... the Clark-Wilson model is a Constrained Data Item (CDI). An Integrity Verification Procedure (IVP) ensures that all CDIs in the system are valid at a certain state. Transactions that enforce the integrity policy are represented by Transformation Procedures (TPs). A TP takes as input a CDI or Unconst ...
... the Clark-Wilson model is a Constrained Data Item (CDI). An Integrity Verification Procedure (IVP) ensures that all CDIs in the system are valid at a certain state. Transactions that enforce the integrity policy are represented by Transformation Procedures (TPs). A TP takes as input a CDI or Unconst ...
Chapter 2
... Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skills to convince people to reveal access credentials or other valuable information to attacker ...
... Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skills to convince people to reveal access credentials or other valuable information to attacker ...
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 16. Illustrate fundamental legal issues involved with security management. 17. Design an audit policy and incident response procedures. 18. Manage and distribute critical software updates that resolve known security vulnerabilities and other stability issues. 19. Explain the importance of educating ...
... 16. Illustrate fundamental legal issues involved with security management. 17. Design an audit policy and incident response procedures. 18. Manage and distribute critical software updates that resolve known security vulnerabilities and other stability issues. 19. Explain the importance of educating ...
Chapter 2
... Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skills to convince people to reveal access credentials or other valuable information to attacker ...
... Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skills to convince people to reveal access credentials or other valuable information to attacker ...
Social engineering (security)

Social engineering, in the context of information security, refers to psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional ""con"" in that it is often one of many steps in a more complex fraud scheme.The term ""social engineering"" as an act of psychological manipulation is also associated with the social sciences, but its usage has caught on among computer and information security professionals.