* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Information Security Incident Management
Multilevel security wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Unix security wikipedia , lookup
Airport security wikipedia , lookup
IT risk management wikipedia , lookup
Wireless security wikipedia , lookup
Distributed firewall wikipedia , lookup
Mobile security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Information security wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
Computer security wikipedia , lookup
Security-focused operating system wikipedia , lookup
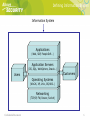
Speaker • Robert Potvin, CISSP & CBCP • 15 years of IT Security Experience • Senior Consultant of Above Security • Operations in Montreal, Ottawa, Toronto and Bahamas working with 160 customers in 11 countries Confidential Document 1 ISO-17799 Overview • BS7799 was created in 1999 as a two part document (standard + certification scheme) by the British Standards Institution (BSI) • The standard portion was adopted and converted into an ISO standard in 2000 • The certification scheme portions is still a BSI only standard and it’s latest revision is dated 2002 • Many worldwide governments policies, standards, guidelines and best practices are based, inspired or in compliance with ISO17799:2000 & BS7799-2:2002 and some of them don’t even know it • There is a general misconception that it is not a complete standard because it lacks implementation guidelines • Since it was built by a standard organization (BSI), the implementation guidelines where intentionally left out of the document and regroup into other specific standards and “security techniques” (i.e.: ISO13335, PAS56…) Confidential Document 2 ISO-17799:2000 Overview • 127 controls distributed within 10 categories - Information security policy Organizational security Asset classification and control Personnel security Physical & environmental security Communication & operations management Access control System development & maintenance Business continuity management Compliance • Uses a Plan/Do/Check/Act implementation and operation model that starts with a risk assessment to established the required security controls needed to adequately manage information security risks within the business processes • Used in conjunction with BS7799, it also establish documentation, revision, communication, training, auditing and continuous improvement requirements Confidential Document 3 ISO-17799 Overview • Complementary standards and guidelines where inspired by ISO17799, design to or supports the implementation of ISO17799: - AS/NSZ-4360:2004, Risk Management Guidelines HB-231:2004, Information Security Risk Management Guidelines ISO-19011:1996, Guidelines for Management System Auditing PAS56:2003, Guide to Business Continuity Management ISO/TR-18044:2004, Information Security Incident Management ISO-GMITS:1996/2001 (Guidelines for the Management of IT Security): • • • • • ISO/TR-13335/1:1996, ISO/TR-13335/2:1997, ISO/TR-13335/3:1998, ISO/TR-13335/4:2000, ISO/TR-13335/5:2001, Concepts and Model for IT Security Planning IT Security Management of IT Security Selection of safeguards Management guidance on network security • CoBIT control objectives are fully mapped to support ISO17799 • ITIL is especially efficient for ‘Communication & Operations Management’ Confidential Document 4 What’s new in ISO-17799:2005 ? • Risk management where addressed only in part 2 document, the part 1 now includes a new chapter on ‘Risk Assessment and Treatment’ requirements • ‘Asset classification and control’ evolve into a more holistic ‘Asset management’ approach • ‘Personnel Security’ evolve into ‘Human resources security’ which now emphasis on what’s needed before, during and on termination of employment • ‘Communication and operations management’ now includes service delivery management of 3rd parties (i.e.: outsourcer performance and security obligation monitoring) • Introduction of ‘Technical Vulnerability Management’ • Incident management controls that where spread all around the previous version of the standard are now consolidated within a new chapter titled ‘Information Security Incident Management’ • In short: 2 new control families, a new total of 135 controls, over 80 changes within the existing controls (deletion/addition/modification) Confidential Document 5 Defining Information System Information System Applications (Web, SAP, PeopleSoft…) Application Servers (IIS, SQL, WebSphere, Oracle…) Users Customers Operating Systems (Win2K, XP, Unix, OS/400…) Networking (TCP/IP, FW, Router, Switch) Confidential Document 6 Copyright 2004 - Above Security Defining Information Security • Assets oriented Information Security: - Protecting Confidentiality Insuring Integrity Preserving Availability Addressing Compliancy Augmenting Reliability • Business oriented information security: - Managing risk Insuring business continuity Protecting corporate image Protecting shareholders’ value Confidential Document 7 Copyright 2004 - Above Security Defining Information Security • From Technology Protection to People and Process: • False sense of protection….. - Firewalls - VPNs - IDS - Applications - Wireless Confidential Document 8 Copyright 2004 - Above Security Problems with Firewalls •Definition - A Firewall filters available services from your company incoming from and outgoing to the Internet. •Problems - Will not prevent hackers from interacting with your company. - Often badly configured incoming and outgoing. - Logging is often poorly configured. - Who checks the Logs ? Confidential Document 9 Problems with VPN •Definition - Virtual Private Network. - Remote access system. - Replacing traditional dial-up modem pools on the net. •Problems - Inexpensive to attack. - Often available for Whoever, Whenever, Wherever. - Few companies use strong authentication. - Once inside, there is no limited field of action to users. Confidential Document 10 Problems with IDS •Definition - Intrusion Detection System •Problems - False positives, false negatives. - Limited load capacity - Correlation of event is painful. - Companies often only use the network IDS. - 24x7 monitoring is required. - Incident handling and response procedure often lacking. - IDS are only alarm systems – useless without monitoring and a central police force. Confidential Document 11 Problems with Applications Problems: - Privileges: • Web server volume and client-server applications with plenty of privileges. - Developers Inexperience: • Often no security training. • Insufficient controls and logs to protect systems. - Validation: • Insufficient validation in data entry and data consultation. – Important information leakages. Confidential Document 12 Problems with Wireless •Problem - Only 25% of companies use the WEP. - Give an unwatched access to the internal network. •Bad Architecture (Direct access to internal network) •Examples: - Jamaica – New Kingston. • More than 80 access points were discovered. • 80% did not use the WEP. - Montreal (in 2 hours) • More than 200 access points discovered. • 85% did not use the WEP. Confidential Document 13 How to diagnose? Penetration Testing •Formal and structured attack simulation against your infrastructure •An attack that will try to use any privileges and information available to both legitimate and non legitimate users to gain access to confidential information •An approach that will try to exploit every weaknesses of your systems both internal, external, application and physical •A formalized operation that will outline what are your exposure to attacks and how complex conducting those attack might be Confidential Document 14 Copyright 2004 - Above Security Penetration testing steps Five step to successful penetration 1. Gaining knowledge about the victim, it’s network, services and applications 2. Scanning the overall infrastructure for potential vulnerabilities that might be present at the various layers 3. Exploit the security breaches to gain access to your systems that might enable us to go further in your network 4. Implement backdoor to preserve the access 5. Erase the traces Confidential Document 15 Copyright 2004 - Above Security Example of successful hack • Being able to gain access to confidential customer database • Being able to access medical information of patient on an hospital network • Being able to create a bank account and conduct fraudulent financial transaction • Being able to hack the wireless network and gain full access to the internal network • Being able to hack the backup server and access confidential information that where not under access control like on the rest of the network Confidential Document 16 Copyright 2004 - Above Security Example of successful hack • Being able to take control of the corporation central database server • Being able to control the SCADA infrastructure for lighting, gaz and water treatment facilities • Being able to steal intellectual property and application source code • Being able to control the security camera systems • And the list can goes on forever… Confidential Document 17 Copyright 2004 - Above Security What are we left with ? •Information Security Challenges: - Providing universal access to data and systems - Establishing the right value to assets - Identifying system weaknesses - Efficiently monitoring the assets - Building a corporate culture - Reaching the right balance between risk, exposure, usability, protection and investments But how ? Confidential Document 18 Copyright 2004 - Above Security Security Governance •Governance is: doing things the way they should be done to protect the business, the employee and shareholders value •Risks and threats are real and could have significant impact on your business •Information security is the responsibility of the board; members should sign off the policy •Information assets possess value; proper protection should therefore be in place •Information security is not free; like any investment, it should be properly managed Confidential Document 19 Copyright 2004 - Above Security Security Governance •Information security governance should deliver: - Strategic alignment: orientations are driven by business requirements, not technology, and should impact productivity as little as possible - Direction: a standard set of practices coupled with proper effort distribution, keeping focus on areas with the greatest impact and business benefits - Risk management: a list of risks we agree to live with, a proper understanding of risk exposure and a sufficient awareness of management priorities - Measurement: a defines set of metrics to independently obtain assurance on measurable processes and investment performance Confidential Document 20 Copyright 2004 - Above Security Information security recipe 1. Implement information security policies 2. Risk Assessment 3. Develop a business continuity strategy 4. Configure proper network and system auditing 5. Deploy log centralization and analysis 6. Insure intrusion detection at all layers 7. Segment your network and reinforce access control 8. Manage your vulnerabilities 9. Conduct system security monitoring, 10. Get independent compliance audit and penetration testing 11. Security Awareness and Training Confidential Document 21 Copyright 2004 - Above Security Ingredient #1 •Information Security Policies: - It is a management statement that information security is important - It provide direction by establishing a set of clearlyarticulated business rules to help people make decision when using or managing information assets - It is uniquely tailored to your organization requirements and business processes - It is a standard of due care that needs to be implemented no matter what industry your organization belongs Confidential Document 22 Copyright 2004 - Above Security Information Security Policies It should minimally contain the following: 1. Organizational security 2. Asset classification and control 3. Users, operators and management roles and responsibilities 4. System usage guidelines 5. Physical and environmental security 6. Communication and operations management 7. Access control 8. Systems development and maintenance 9. Business continuity 10. Compliance and measurement Confidential Document 23 Copyright 2004 - Above Security Ingredient #2 •Risk Management: - Information security is not about technology, it’s about managing risk - A vulnerability is a breach within a system (reliance on electricity, security hole, lack of control, physical exposure…) - A threat is the actual event that can exploit a vulnerability (virus, electrical storm, hurricane…) - A risk is the result of the combination of vulnerability and threat (outage = power failure cause by storm) Confidential Document 24 Copyright 2004 - Above Security Risk Management Asset Value Asset Value Risk = Volume of cube Risk Threat Threat Vulnerability Actual Risk Confidential Document Vulnerability Residual Risk 25 Copyright 2004 - Above Security Ingredient #3 •Business Continuity: - BC is the ability to maintain a constant availability of processes and information availability - DR is the immediate and temporary restoration of computing and network operation within a defined timeframe after a disaster occurs - Advanced planning and preparations are necessary to identify impact and potential losses and to establish a step by step approach to business resumption - A plan is not a static document, it is a living strategy and an evolving process Confidential Document 26 Copyright 2004 - Above Security Cost of Downtimes Productivity • Number of employees affected x hours out x burdened hourly rate Damaged Reputation • Customers • Suppliers • Financial markets • Banks • Business partners • ... Confidential Document Know your downtime costs per hour, day, two days ... Other Expenses • Temporary employees • Equipment rental • Overtime costs • Extra shipping costs • Travel expenses • Legal obligations ... Revenue • Direct loss • Compensatory payments • Future revenue losses • Billing losses • Investment losses Financial Performance • • • • • • • Revenue recognition Cash flow Lost discounts (A/P) Payment guarantees Credit rating Stock price … Source: Gartner Group 2003 27 Copyright 2004 - Above Security Ingredient #4 •Network Security Monitoring: - Technical equivalent to security governance - Corporation tends to neglect an holistic approach when protecting corporate assets - Corporation normally focus solely on perimeter - Defense in depth the best risk mitigation approach - In brief, it is the combination of hardware, software, people and processes to monitor and respond to security incident Confidential Document 28 Copyright 2004 - Above Security Components to monitor Vulnerability Management Server logs Firewall & VPN Logs Router & Switches Log Network IDS Components to be monitored Host based IDS Application Based IDS Application logs Policy Compliance Anti-Virus Confidential Document 29 Copyright 2004 - Above Security Steps for proper monitoring Information Collection Centralization and standardization of the information Alert Normalization Process Event Correlation Process Event Prioritization Process Information Presentation Process Incident Handling Intervention Confidential Document 30 Copyright 2004 - Above Security The MMI Infrastructure Confidential Document 31 Copyright 2004 - Above Security Platforms to support • Operating Systems: NT, 2000, 2003/XP, AIX, Solaris, HP, Linux, BSD, OS/400 • Networking: Cisco, Nortel, 3COM • Firewall/VPN: MS ISA, Checkpoint, Cisco, Netscreen, Watchguard, Symantec • IDS: Snort, Cisco, ISS, Enterasys, Tripwire, NFR, NAI, Symantec • PKI/Strong authentication: RSA, Entrust, Microsoft • Application servers: MS SQL, IIS, MS Exchange, Lotus Notes, Websphere, Oracle • Application: Greatplains, Peoplesoft, SAP, Custom Web Based Confidential Document 32 Copyright 2004 - Above Security Solutions • Attack monitoring at all layers (network, server, application) • Vulnerability management/change management for complex infrastructure • Early warning system for potentially disastrous virus, vulnerability, worms… • Pure event correlation (cause to effect analysis) • Centralization, data reduction and analysis of your server logs • 24x7 monitoring by highly trained personnel • Remote real time intervention • Flexible real time escalation for sensible events • Forensic Confidential Document 33 Copyright 2004 - Above Security Ingredient #5 •Compliance Audit and Testing: -Last Step (confirm posture) - First Step (Business Case) - Solid Methodology (not a sales pitch document !) - What to look for : • External infrastructure • External application interfaces • Internal Intrusion • Internal vulnerabilities • Wireless • Social engineering • War Dialing Confidential Document 34 Copyright 2004 - Above Security Ingredient #6 •Security Awareness and training: -Executives linked to business drivers Regulations, obligations and risks - IT Very technical Incident analysis Build a training plan - End-Users Real world examples Link to their daily activities Confidential Document 35 Copyright 2004 - Above Security Thanks for attending ! Questions? Please visit us at our booth ! Web: www.abovesecurity.com E-mail: [email protected] HQ Phone: (450) 430-8166 Confidential Document 36