* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download InterScan Messaging Security Solutions
Cyberwarfare wikipedia , lookup
Airport security wikipedia , lookup
Information security wikipedia , lookup
Wireless security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Unix security wikipedia , lookup
Microsoft Security Essentials wikipedia , lookup
Information privacy law wikipedia , lookup
Cyberattack wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Security-focused operating system wikipedia , lookup
Distributed firewall wikipedia , lookup
Operation AntiSec wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Computer security wikipedia , lookup
Mobile security wikipedia , lookup
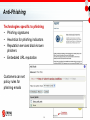
International cybercrime wikipedia , lookup
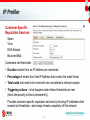
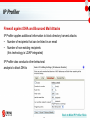
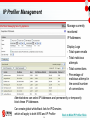
InterScan Messaging Security Solutions Filip Demianiuk Technical Channel Manager Poland & Baltic Countries [email protected] Agenda – Gateway Messaging Security • Email Threats • InterScan Messaging Security Solutions • Beyond Gateway Messaging Security • Summary and Keys to Remember 2 Email Threats Spam Problem 75-90% of Email is Spam 1 ● Spam has increased fivefold in the last couple of years.2 ● Zombies and botnets make it easier for spammers and are now responsible for most spam ● Spam is evolving with new techniques like image spam ● Even if blocked from the inbox, letting spam into the network uses bandwidth, storage, and other network resources Source: Gartner “Benchmarking Anti-Spam Effectiveness.” April 25, 2006 (Gartner customers report that 75-90% of the emails they receive are spam) 1 2 Source: Ferris The Global Economic Impact of Spam, 2005. February 2005 (Other statistics) 4 Virus Problem Viruses are only in about 2-6% of emails.1 HOWEVER, the impact can be substantial. And the number of viruses can add up. 2 3 Instead of the mass virus attacks of the past, hackers are using viruses for monetary gain (often using more targeted attacks) Examples Source: Gartner “Benchmarking Anti-Spam Effectiveness.” April 25, 2006 (viruses 2-6% of email) • Bot code that allows hackers to use the victim’s machine to send spam or fraudulent emails 1 2 Source: Computer Economics. 2005 Malware Report: The Impact of Malicious Code Attacks. January 2006. (Figure 1) 3 Source: The Radicati Group, Inc. Email Security Market, 2006-2010. June 2006 (Bar Graph) • Key-logging Trojans that collect confidential information 5 Phishing Problem • Email fraud made up 4% of email in 20061 • Phishing emails spoof legitimate companies and attempt to steal information 1 • Phishing affects both individuals and corporations with thousands of unique phishing threats sent out every month • Companies need to protect themselves from loss of confidential information and potential liability Blended threats – Malware and phishing attacks Key-Logging Trojans also “phish” for information Pharming Crimeware redirects users to fraudulent Web sites to steal information 1 6 Source: The Radicati Group, Inc. Email Security Market, 2006-2010. June 2006 (fraud 4% of email) 2 Source: Anti-Phishing Working Group. Retrieved from Web site: http://www.antiphishing.org/ (fraudulent email and Web site) Targeted Attacks Unique attacks tailored for the targeted organization • Viruses (such as ransom attacks) • Spyware in Email • Corporate Spear Phishing • Directory Harvest Attack (DHA) – Tries numerous variations of possible email addresses using a company’s domain – Goal = to acquire a valid email list for the company – Can use the list later for a targeted attack, such as a phishing, virus, spyware, or spam attack • Bounced Mail Attacks – Spoofs a legitimate company by inserting its domain as the email sender – When the receiving servers bounce the email, the bounced emails are sent to the spoofed company, flooding the server and tainting the reputation of the innocent company 7 Data Privacy & Protection • Regulatory Compliance Regulations impose mandates on data protection or privacy Can affect email and other digital communication • Corporate Governance Internal standards or policies that a company uses to govern itself In this case policies for appropriate use of messaging • Loss of Confidential Information Protection against data leakage, whether intentional, or inadvertent 8 Email Security Concerns • • • • • • • • • • Spam Viruses Network Security Regulatory Compliance Corporate Governance Loss of Confidential Information Spyware Denial of Service Attacks Phishing Directory Harvest Attacks 1 1 Source: The Radicati Group, Inc. Email Security Market, 2006-2010. June 2006 (Bar Graph) 9 InterScan Messaging Security Solutions Gateway Email Security Products Same superior protection in all form factors • SOFTWARE: InterScan Messaging Security Suite (IMSS) - Flexible configuration options on customer’s own hardware and on multiple machines - Solution on leading operating systems: Windows, Linux and Solaris • APPLIANCE: InterScan Messaging Security Appliance (IMSA) - Easy deployment with pre-configured software - Redundant, high-throughput appliance optimized for security and performance • HOSTED SERVICE: InterScan Messaging Hosted Security (IMHS) - Immediate deployment by simply redirecting the MX record - Added security and bandwidth by keeping threats completely off the network - Reduced hardware and software purchases and maintenance 11 Comprehensive Messaging Protection Viruses, Worms, Trojans Spyware Spam Phishing Inappropriate Content Award-Winning Anti-Virus – includes zero-day protection Anti-Spyware –protection against spyware in email Multi-Tier Anti-Spam – Network Reputation Services, IP Profiler, and our anti-spam composite engine for high effectiveness with low false positives Anti-Phishing – reputation services, signatures, and heuristics aimed at phishing Inappropriate Content – content filtering enforces compliance and prevents data leakage 12 Multi-Tier Anti-Spam Highly Effective Solution Network Reputation Services – First Defense • Global and dynamic reputation services • Blocks up to 80% before entering the network IP Profiler – Patent-Pending Technology • Customer-specific reputation services based on company email traffic, keeps threats off network • Firewall against DHA and bounced mail attacks Anti-Spam Composite Engine – Guards Inbox • Stops any remaining spam before it enters inbox • Integrates statistical analysis, heuristics, signatures, whitelists, blacklists and more • Patent-pending image spam detection technology 13 Network Reputation Services Network Reputation Services • Global: Verifies IP addresses against the world’s largest, most trusted reputation database • Dynamic: Identifies new spam and phishing sources, stopping even zombies and botnets when they first emerge Fights off spam at the source • Before it enters the gateway • Uses email samples and sender histories to accurately determine the reputation • Leaves only a small percentage of mail to be filtered by the traditional scanning • Saves bandwidth, storage, and other network resources 14 IP Profiler Customer-Specific Reputation Services Spam Virus DHA Attacks Bounced Mail Customers set thresholds • Duration emails from an IP Address are monitored • Percentage of emails from that IP Address that contain the email threat • Total mails that need to be received to be considered a relevant sample • Triggering actions – what happens when these thresholds are met (block temporarily or block permanently) Provides customer-specific reputation services by blocking IP addresses that exceed set thresholds—also keeps threats completely off the network Additional Information 15 Trend Micro Anti-Spam Composite Engine What is Trend Micro Anti-Spam Composite Engine? Trend Micro anti-spam composite engine uses a “cocktail” approach to block both spam and phishing emails. – – – – – – Statistical Analysis Advanced Heuristics Signature Filtering Whitelists/Blacklists Multilingual Spam Detection Patent-Pending Image Spam Detection Technology Industry Proven Technology Install base of over 25 million seats over the past four years 16 Image Spam Detection Patent-Pending Image Spam Detection Boils down to the core of the email—for example, strips out background and text colors, dimensions, and other randomized elements Enables just a few main signatures to stop all of the numerous variations 17 Award-Winning Antivirus and Anti-Spyware Antivirus – Email and Attachments • Pattern files • Zero-day protection – Zero-day protection applies heuristics to detect unknown viruses – For example, IntelliTrap stops viruses based on the tools used to hide the virus and not the virus code itself--no signature is required • Anti-spyware and other malware protection for email • ActiveAction provides automated responses to viruses, spyware, and other malware 18 Anti-Phishing Technologies specific to phishing • Phishing signatures • Heuristics for phishing indicators • Reputation services block known phishers • Embedded URL reputation Customers can set policy rules for phishing emails 19 Protection from Targeted Attacks • Technologies that prevent known attacks will not work (for example, signatures and reputation services) • Instead we apply predictive techniques--zero-day protection, heuristics, and behavior analysis - Antivirus = prevents virus attacks aimed at specific organizations (for example, ransom attacks) - Anti-spyware = stops the more targeted spyware attacks sent through email. - DHA and bounced mail protection (IP Profiler) = protects against bounced mail attacks and directory harvest attacks, which can result in additional targeted attacks - Anti-phishing = blocks corporate spear phishing 20 Data Privacy and Protection Enforce Content Compliance • Minimize legal liability • Comply with regulations (SOX, HIPAA, …) • Support internal messaging standards • Prevent data leakage • Antivirus stops any malware sent by email that could potentially damage or corrupt data. • Anti-phishing helps to prevent the theft of confidential information. • Anti-spyware stops the potentially more targeted attacks sent by email which attempt to steal corporate data. • Flexible content filtering enables the efficient inspection of messages to ensure that data does not improperly leave the organization. 21 Content Filtering Inbound and outbound content filters scan emails and attachments Specify Protected Content − Attachment characteristics (true file type, name, size, etc.) − Keywords, lexicons, and preset dictionaries − Customize with Boolean and regular expressions Select Authorized Senders or Recipients − Company-wide, department, group, or individual Designate Appropriate Enforcement − Delete, quarantine, notify, postpone, pass, encrypt with TLS, or archive − Add company specific legal disclaimers to email text 22 Easy Management • High performance • Highly scalable solution • Single Web-based management console • Centralized policy, quarantine, archive, logging, and reporting • Delegated administration • Message tracking with flexible search criteria • End-User Quarantine 23 Policy & Reporting Enhancements Policies • Intuitive policy creation 1. Inbound or outbound or both 2. Select what to filter 3. Select the action 4. Review and assign order Reports • One-time and scheduled reports • Reports on mail traffic, viruses, spam, content, policy, Network Reputation Services, and IP Profiler 24 Return on Investment • Keeps threats out of the inbox—increasing productivity and preventing staff from falling victim to malware and phishing • End-User Quarantine and quarantine notification emails allow users to efficiently manage their own spam • Messaging tracking and reports provide detailed system views • Single Web console, LDAP integration, and delegated administration make management easy, freeing IT staff • End-user spam management reduces the burden on IT • Stopping threats at the perimeter, often before they even enter the gateway (using reputation and/or hosted services) • Solutions provide security and preserve bandwidth, storage, and other network resources • Data protection helps reduce legal fees and settlements, retain customers, and preserve the company reputation 25 Beyond Gateway Email Security Layered Messaging Security 27 Trend Micro Enterprise Protection Strategy – A Complete Network Security Framework Enforce security policy on every network device Monitor network and Internet for potential threats Recover via automated cleanup of viruses, worms, Trojans and spyware Customized and comprehensive centralized management 28 Prevent damage by stopping threats Summary and Key Points to Remember Summary and Key Points InterScan Messaging Security solutions offer integrated, comprehensive security at the enterprise perimeter All email pain points are addressed: – – – – – Multi-tier anti-spam with cutting-edge, patent-pending technologies Award-winning antivirus with zero-day protection and anti-spyware Anti-phishing with phishing-specific technologies Targeted attack prevention using predictive techniques Data protection to enforce compliance and prevent data leakage Minimizes risks and costs, providing high return on investment - - The solutions are optimized to keep threats off the network, increasing security and network resources Easy management reduces the burden in IT staff, freeing them for other projects Data security helps stop data leakage, reduce legal fees and settlements, retain customers, and preserve the company reputation, mitigating these business risks 30 Gateway Security Leader Trend Micro pioneered gateway antivirus security and is the market share leader – IDC1 “Having been founded in 1988, Trend Micro has nearly two decades of experience in the enterprise, service provider, mid-sized, SOHO and consumer security market. With many years of success behind it, the company has grown to be a current global leader in network security” – Radicati 2 Trend Micro started in antivirus and has expanded into a comprehensive network security company, providing a strong, unified defense for its customers. 1 IDC, Worldwide Antivirus 2006–2010 Forecast Update and 2005 Vendor Analysis, Doc ##204715, Dec 2006 2 31 Source: The Radicati Group, Inc. Email Security Market, 2006-2010. June 2006 Appendix Product Levels Threat protection is packaged in different levels * IMHS Standard = complete inbound protection with streamlined management IMHS Advanced = granular access and control for inbound and outbound traffic with flexible content filtering, similar to IMSS and IMSA 33 IP Profiler Firewall against DHA and Bounced Mail Attacks IP Profiler applies additional information to block directory harvest attacks • Number of recipients that can be listed in an email • Number of non-existing recipients (this technology is LDAP integrated) IP Profiler also conducts other behavioral analysis to block DHAs 34 Back to Main IP Profiler Slide IP Profiler – How It Works 1. Records all inbound and outbound SMTP traffic 2. Reports records on email traffic from each IP Address to a database 3. The emails are scanned by the anti-spam composite engine 4. The results of the scanning engine are reported to the database 5. The traffic from the IP Address is profiled by cross referencing the recorded traffic with the scanning results For example, total messaging from the IP Address vs. spam messages from the IP Address 6. This outcome is compared against the user thresholds 7. If the outcome exceeds the thresholds, the trigger action is applied Block Permanently (SMTP 5xx) or Block Temporarily (SMTP 4xx) 35 Back to Main IP Profiler Slide IP Profiler Management Manage currently monitored IP Addresses Display Logs - Total spam emails - Total malicious attempts - Total connections - Percentage of malicious attempt in the overall number of connections Administrators can select IP Addresses and permanently or temporarily block these IP Addresses Can create global white/black lists for IP/Domains which will apply to both NRS and IP Profiler Back to Main IP Profiler Slide 36