03-WAS Common Threats - Professional Data Management
... usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. ...
... usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. ...
InterScan Messaging Security Solutions
... Key-Logging Trojans also “phish” for information Pharming Crimeware redirects users to fraudulent Web sites to steal information ...
... Key-Logging Trojans also “phish” for information Pharming Crimeware redirects users to fraudulent Web sites to steal information ...
Spear Phishing Attacks—Why They are Successful and How to Stop
... security defenses simply do not stop these types of attacks. This paper provides a detailed look at how spear phishing is used within advanced targeted attacks. It will provide an overview of spear phishing, its characteristics, and a notable attack case study. Finally, the paper looks at the key ca ...
... security defenses simply do not stop these types of attacks. This paper provides a detailed look at how spear phishing is used within advanced targeted attacks. It will provide an overview of spear phishing, its characteristics, and a notable attack case study. Finally, the paper looks at the key ca ...
spear-phishing attacks
... Some of the most notorious cyber crimes in recent history — such as the attacks on major banks, media companies and even security firms — started with just one person clicking on a spear-phishing email. Spear phishing is on the rise because it works. Traditional security defenses simply do not detec ...
... Some of the most notorious cyber crimes in recent history — such as the attacks on major banks, media companies and even security firms — started with just one person clicking on a spear-phishing email. Spear phishing is on the rise because it works. Traditional security defenses simply do not detec ...
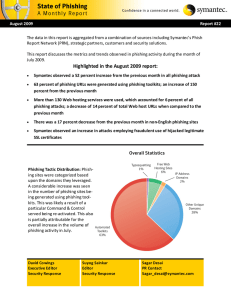
Highlighted in the August 2009 report
... padlock icon, while offering a false sense of security to the victims. In this particular attack, the certificates were legitimate because they matched the compromised legitimate domain. The fake pages that were spoofing the target brands in actuality had no connection with the displayed domain or t ...
... padlock icon, while offering a false sense of security to the victims. In this particular attack, the certificates were legitimate because they matched the compromised legitimate domain. The fake pages that were spoofing the target brands in actuality had no connection with the displayed domain or t ...
Introduction - GMU Computer Science
... • 5% of users are lured into these attacks! [2005] • Delivery via web site, e-mail or instant message, the attack asks users to click on a link to “re-validate” or “re-activate” their account. The link displays a believable facsimile of your site and brand to con users into submitting private detail ...
... • 5% of users are lured into these attacks! [2005] • Delivery via web site, e-mail or instant message, the attack asks users to click on a link to “re-validate” or “re-activate” their account. The link displays a believable facsimile of your site and brand to con users into submitting private detail ...
DO NOT - Middlebury College
... Recognize a Secure Web Site (HTTPS) How to Spot a Spoofed Web Site Recognize a Phishing Attempt What is Social Engineering ...
... Recognize a Secure Web Site (HTTPS) How to Spot a Spoofed Web Site Recognize a Phishing Attempt What is Social Engineering ...
Prevent Online Fraud and Identity Theft
... information from Identity Theft is crucial. There are many ways the unscrupulous can gain access to information such as your name, Social Security Number, credit card or bank account numbers, or other identifying information to commit fraud or other crimes. E-Mail Phishing - Involves you receiving a ...
... information from Identity Theft is crucial. There are many ways the unscrupulous can gain access to information such as your name, Social Security Number, credit card or bank account numbers, or other identifying information to commit fraud or other crimes. E-Mail Phishing - Involves you receiving a ...
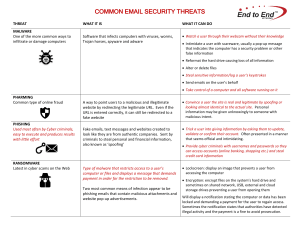
COMMON EMAIL SECURITY THREATS
... website by redirecting the legitimate URL. Even if the URL is entered correctly, it can still be redirected to a fake website ...
... website by redirecting the legitimate URL. Even if the URL is entered correctly, it can still be redirected to a fake website ...
Fraudulent Emails, Websites and Phishing Variations Fraudulent
... How fraudsters obtain email addresses Fraudsters obtain email addresses from many places on the Internet. They also purchase email lists and sometimes guess email addresses. Fraudsters generally have no idea if people to whom they send banking-related phish emails are actual bank customers. Their ho ...
... How fraudsters obtain email addresses Fraudsters obtain email addresses from many places on the Internet. They also purchase email lists and sometimes guess email addresses. Fraudsters generally have no idea if people to whom they send banking-related phish emails are actual bank customers. Their ho ...
Phishing/Email Scams - Minot State University
... Phishing/Email Scams Phishing is the use of email and fraudulent web sites to trick people into disclosing personal financial or identity information, such as credit card or Social Security numbers, user names, passwords and addresses. Although most "phishes" come as email, phishing scams can also c ...
... Phishing/Email Scams Phishing is the use of email and fraudulent web sites to trick people into disclosing personal financial or identity information, such as credit card or Social Security numbers, user names, passwords and addresses. Although most "phishes" come as email, phishing scams can also c ...
Phishing Scams - Corner Stone Credit Union
... account or personal information, such as passwords, Social Security numbers, PINs, credit or check card numbers, or other confidential information. To protect sensitive information, never respond to such requests. It’s important to remember that this type of scam can also come in the form of text me ...
... account or personal information, such as passwords, Social Security numbers, PINs, credit or check card numbers, or other confidential information. To protect sensitive information, never respond to such requests. It’s important to remember that this type of scam can also come in the form of text me ...
Abstract - Compassion Software Solutions
... Malicious URLs have been widely used to mount various cyber attacks including spamming, phishing and malware. Phishing is a security attack that involves obtaining sensitive or otherwise private data by presenting oneself as a trustworthy entity. Phishes often exploit users’ trust on the appearance ...
... Malicious URLs have been widely used to mount various cyber attacks including spamming, phishing and malware. Phishing is a security attack that involves obtaining sensitive or otherwise private data by presenting oneself as a trustworthy entity. Phishes often exploit users’ trust on the appearance ...
Phishing

Phishing is the attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money), often for malicious reasons, by masquerading as a trustworthy entity in an electronic communication. The word is a neologism created as a homophone of fishing due to the similarity of using fake bait in an attempt to catch a victim. Communications purporting to be from popular social web sites, auction sites, banks, online payment processors or IT administrators are commonly used to lure unsuspecting victims. Phishing emails may contain links to websites that are infected with malware. Phishing is typically carried out by email spoofing or instant messaging, and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one. Phishing is an example of social engineering techniques used to deceive users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.Many websites have now created secondary tools for applications, like maps for games, but they should be clearly marked as to who wrote them, and users should not use the same passwords anywhere on the internet.Phishing is a continual threat that keeps growing to this day. The risk grows even larger in social media such as Facebook, Twitter, and Google+. Hackers commonly take advantage of these sites to attack people using them at their workplace, homes, or in public in order to take personal and security information that can affect the user or company (if in a workplace environment). Phishing takes advantage of the trust that the user may have since the user may not be able to tell that the site being visited, or program being used, is not real; therefore, when this occurs, the hacker has the chance to gain the personal information of the targeted user, such as passwords, usernames, security codes, and credit card numbers, among other things.