Password Security
... From the Desk of Thomas F. Duffy, Chair, MS-ISAC Every day malicious cyber-actors compromise websites and post lists of usernames, email addresses, and passwords online. While this can be embarrassing, such as when thousands of government employees email addresses and passwords were exposed during t ...
... From the Desk of Thomas F. Duffy, Chair, MS-ISAC Every day malicious cyber-actors compromise websites and post lists of usernames, email addresses, and passwords online. While this can be embarrassing, such as when thousands of government employees email addresses and passwords were exposed during t ...
White Hat Hacking Tyler Schumacher Department of Computer
... demonstrates exactly how a grey hat hacker can work is self-described in the article "How we defaced www.apache.org" written by two hackers who go by “{}” and “Hardbeat”. The introduction to the article follows: This paper does _not_ uncover any new vulnerabilities. It points out common (and slight ...
... demonstrates exactly how a grey hat hacker can work is self-described in the article "How we defaced www.apache.org" written by two hackers who go by “{}” and “Hardbeat”. The introduction to the article follows: This paper does _not_ uncover any new vulnerabilities. It points out common (and slight ...
1 | I.C.T.C. “International Computer Training Center” www.ictc.gr info
... Lesson 1: Introduction to Ethical Hacking Problem Definition -Why Security? Essential Terminologies Elements of Security The Security, Functionality and Ease of se Triangle Case Study What does a Malicious Hacker do? Types of Hacker Attacks ...
... Lesson 1: Introduction to Ethical Hacking Problem Definition -Why Security? Essential Terminologies Elements of Security The Security, Functionality and Ease of se Triangle Case Study What does a Malicious Hacker do? Types of Hacker Attacks ...
1.2: Research and Participation
... menu and select File-New -Message: You can also create a new message by selecting the “Write a new message” option from the main window. To write a message, you must first decide who will receive this email. The email address of the receiver must be filled in the ‘To’ field. If you want to send the ...
... menu and select File-New -Message: You can also create a new message by selecting the “Write a new message” option from the main window. To write a message, you must first decide who will receive this email. The email address of the receiver must be filled in the ‘To’ field. If you want to send the ...
From Russia with Love: Behind the Trend Micro
... The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most current situation. Nothing contai ...
... The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most current situation. Nothing contai ...
Privacy Policy - Dickey`s Barbecue Pit
... submit to us is secure and kept confidential. Our website is certified as a licensee of the DigiCert ClickID™ Site Seal program. DigiCert® is a provider of digital trust services that enable everyone, everywhere to engage in commerce and communications securely. When you place an order online, your ...
... submit to us is secure and kept confidential. Our website is certified as a licensee of the DigiCert ClickID™ Site Seal program. DigiCert® is a provider of digital trust services that enable everyone, everywhere to engage in commerce and communications securely. When you place an order online, your ...
Hackers and Attackers
... – Extortion, blackmail, theft, are all alive and well in the cyber world – Even physical security can be compromised if we include cyber stalking – Maybe other motivation such as malice against a company or government agency ...
... – Extortion, blackmail, theft, are all alive and well in the cyber world – Even physical security can be compromised if we include cyber stalking – Maybe other motivation such as malice against a company or government agency ...
Networking Security
... • Attacker may can extend an application’s SQL statement to extract or update information that the attacker is not authorized to access • Attacker will explore how the Web application interacts with the back-end database by finding a user-supplied input string that will be part of a database query ...
... • Attacker may can extend an application’s SQL statement to extract or update information that the attacker is not authorized to access • Attacker will explore how the Web application interacts with the back-end database by finding a user-supplied input string that will be part of a database query ...
InterScan Messaging Security Solutions
... – Goal = to acquire a valid email list for the company – Can use the list later for a targeted attack, such as a phishing, virus, spyware, or spam attack • Bounced Mail Attacks – Spoofs a legitimate company by inserting its domain as the email sender – When the receiving servers bounce the email, th ...
... – Goal = to acquire a valid email list for the company – Can use the list later for a targeted attack, such as a phishing, virus, spyware, or spam attack • Bounced Mail Attacks – Spoofs a legitimate company by inserting its domain as the email sender – When the receiving servers bounce the email, th ...
Information Security Policy
... The Management’s intentions for publishing an Acceptable Use Policy are not to impose restrictions that are contrary to the company’s established culture of openness, trust and integrity. Management is committed to protecting the employees, partners and the company from illegal or damaging actions b ...
... The Management’s intentions for publishing an Acceptable Use Policy are not to impose restrictions that are contrary to the company’s established culture of openness, trust and integrity. Management is committed to protecting the employees, partners and the company from illegal or damaging actions b ...
Threats and Attacks
... § Incident: definitions vary § Any attack, all attacks using vulnerability X, etc. § Anything resulting in service degradation other than problem mgmt., service request fulfillment ...
... § Incident: definitions vary § Any attack, all attacks using vulnerability X, etc. § Anything resulting in service degradation other than problem mgmt., service request fulfillment ...
Ch – 1 Introduction
... or other information traffic so that opponents, even if they captured the message, could not extract the information from the message. • The common technique for masking contents is encryption. If we had encryption protection in place, an opponent still might be able to observe the pattern of these ...
... or other information traffic so that opponents, even if they captured the message, could not extract the information from the message. • The common technique for masking contents is encryption. If we had encryption protection in place, an opponent still might be able to observe the pattern of these ...
Survey of online attacks on E-Commerce sites
... 3.5 Man in the Middle attack : This technique uses a packet sniffer to tap the communication between client and the server. Packet sniffer comes in two categories: Active and Passive sniffers. Passive sniffers monitors and sniffs packet from a network having same collision domain i.e. network with a ...
... 3.5 Man in the Middle attack : This technique uses a packet sniffer to tap the communication between client and the server. Packet sniffer comes in two categories: Active and Passive sniffers. Passive sniffers monitors and sniffs packet from a network having same collision domain i.e. network with a ...
Protecting against spear-phishing
... that the average cost of a cyber-attack in the UK was £1.9m in 2010, and that’s without taking into account the increasingly heavy fines being issued for lax security.4 This was evident in July 2009 when HSBC, the largest bank in the UK, was fined £3.2m for losing confidential customer information. ...
... that the average cost of a cyber-attack in the UK was £1.9m in 2010, and that’s without taking into account the increasingly heavy fines being issued for lax security.4 This was evident in July 2009 when HSBC, the largest bank in the UK, was fined £3.2m for losing confidential customer information. ...
spear-phishing attacks
... as a byproduct of larger data-theft operations. For example, a cyber criminal might steal all data on a file server that happened to include PII, that was of no particular interest to the attacker. This changed last year as Mandiant investigated several massive PII breaches that it believed were orc ...
... as a byproduct of larger data-theft operations. For example, a cyber criminal might steal all data on a file server that happened to include PII, that was of no particular interest to the attacker. This changed last year as Mandiant investigated several massive PII breaches that it believed were orc ...
Cybersecurity and Information Assurance PPT
... • Snort’s open source network-based intrusion detection system has the ability to perform realtime traffic analysis and packet logging on Internet Protocol (IP) networks. • Snort performs protocol analysis, content searching, and content matching. • The program can also be used to detect probes or a ...
... • Snort’s open source network-based intrusion detection system has the ability to perform realtime traffic analysis and packet logging on Internet Protocol (IP) networks. • Snort performs protocol analysis, content searching, and content matching. • The program can also be used to detect probes or a ...
Security on the Internet - Australian Federal Police
... from an unknown person through websites such as dating sites, online forums or social networking sites. Scams are usually designed to either steal your money or trick you into revealing personal information. They use techniques to manipulate you and appeal to your good nature, and are constantly ...
... from an unknown person through websites such as dating sites, online forums or social networking sites. Scams are usually designed to either steal your money or trick you into revealing personal information. They use techniques to manipulate you and appeal to your good nature, and are constantly ...
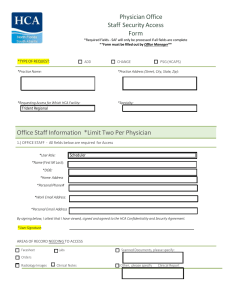
Physician Office Staff Security Access Form Office Staff Information
... I understand that the HCA affiliated facility or business entity (the “Company”) at which I have privileges or for which I work, volunteer or provide services manages health information as part of its mission to treat patients. Further, I understand that the Company has a legal and ethical responsib ...
... I understand that the HCA affiliated facility or business entity (the “Company”) at which I have privileges or for which I work, volunteer or provide services manages health information as part of its mission to treat patients. Further, I understand that the Company has a legal and ethical responsib ...
Slide 1 - IITK - Indian Institute of Technology Kanpur
... • Hide the Service Set ID or SSID :Sometimes changing the SSID is also not full proof as hackers have advanced methods to intrude into a wireless network if the SSID is known. To prevent such cases the SSID needs to be hidden. Router configuration softwares allow the SSID to be hidden and the steps ...
... • Hide the Service Set ID or SSID :Sometimes changing the SSID is also not full proof as hackers have advanced methods to intrude into a wireless network if the SSID is known. To prevent such cases the SSID needs to be hidden. Router configuration softwares allow the SSID to be hidden and the steps ...
Support: Ticket, Process, and Expectations
... Ensure email password is secure (forgot my password feature generally relies on your email account being secure) Avoid opening unknown email attachments ...
... Ensure email password is secure (forgot my password feature generally relies on your email account being secure) Avoid opening unknown email attachments ...
systemsprinciples2
... – access control (e.g. checking file permissions on file open) – memory safety (process does not read/write outside its own memory space) – type safety (data accessed in accordance with type) ...
... – access control (e.g. checking file permissions on file open) – memory safety (process does not read/write outside its own memory space) – type safety (data accessed in accordance with type) ...
Phishing/Email Scams - Minot State University
... come in the form of text messages and phone calls. An email message may look harmless. Posing as your credit card company, your bank, or even Minot State University, it alerts you to a problem with your account and urges you to respond immediately by clicking a web link and "verifying" or "updating" ...
... come in the form of text messages and phone calls. An email message may look harmless. Posing as your credit card company, your bank, or even Minot State University, it alerts you to a problem with your account and urges you to respond immediately by clicking a web link and "verifying" or "updating" ...
Security Risks - Bannerman High School
... bank details, phone number, address etc.. • Phishers use e-mails pretending to be from e.g. your bank, from Ebay from Pay-Pal to get you to give them your details. • They can even pretend to be someone who wants to give you money, but first you have to give them your bank details.. Then they steal f ...
... bank details, phone number, address etc.. • Phishers use e-mails pretending to be from e.g. your bank, from Ebay from Pay-Pal to get you to give them your details. • They can even pretend to be someone who wants to give you money, but first you have to give them your bank details.. Then they steal f ...
Security Requirements
... “In 1999, some students at the University of the South Pacific managed to get access to the system and retrieve a list of all students email passwords. This allowed them to send abusive messages to others using other students email account” ...
... “In 1999, some students at the University of the South Pacific managed to get access to the system and retrieve a list of all students email passwords. This allowed them to send abusive messages to others using other students email account” ...