Data Security - Devi Ahilya Vishwavidyalaya
... Information Security is a complicated area and can be addressed by well-trained and experienced Professionals. “When there is an attack on the system with the help of different threats, it means that our system is working very slowly, damaged and our information are unsecured” is called Informatio ...
... Information Security is a complicated area and can be addressed by well-trained and experienced Professionals. “When there is an attack on the system with the help of different threats, it means that our system is working very slowly, damaged and our information are unsecured” is called Informatio ...
New Law Requires Businesses in California to Report Electronic Break-Ins
... In the wake of a security breach at one of its own data centers, the State of California has enacted legislation that requires businesses to disclose computer security breaches. The stimulus for the legislation occurred in April 2002, when California’s Steven P. Teale data center in Rancho Cordova s ...
... In the wake of a security breach at one of its own data centers, the State of California has enacted legislation that requires businesses to disclose computer security breaches. The stimulus for the legislation occurred in April 2002, when California’s Steven P. Teale data center in Rancho Cordova s ...
Computer Hacking
... • Anyone can be a computer hacker however, computer hacking is most common in teenagers and young adults. • Computer hackers are often people who enjoy learning more about how computers work and consider computer hacking a form of art. ...
... • Anyone can be a computer hacker however, computer hacking is most common in teenagers and young adults. • Computer hackers are often people who enjoy learning more about how computers work and consider computer hacking a form of art. ...
View Presentation - InfoSec Nashville
... Health Insurance Credentials – Health insurance credentials are $20 each. They include names (more than one for spouse & family coverage), date(s) of birth, contract number, group number, type of plan (Individual/Group, HMO/PPO, deductible and copay information), and insurer contact information for ...
... Health Insurance Credentials – Health insurance credentials are $20 each. They include names (more than one for spouse & family coverage), date(s) of birth, contract number, group number, type of plan (Individual/Group, HMO/PPO, deductible and copay information), and insurer contact information for ...
Challenges of protecting safety internet enviroment for children in
... Promote the good online games, websites, forums and chat room for children, Provide guidelines to improving the awareness for parents. ...
... Promote the good online games, websites, forums and chat room for children, Provide guidelines to improving the awareness for parents. ...
20121101
... A structured (advanced), targeted attack (persistent), intent on gaining information (threat) ...
... A structured (advanced), targeted attack (persistent), intent on gaining information (threat) ...
Slide 1
... DEFINITION OF CYBER TERORRISM “ Electronic attack through computer network towards critical infrastructure that has big potential to disturb social and economic activity of a nation.” Misused of cyberspace by Terrorist Group for specific goal. ...
... DEFINITION OF CYBER TERORRISM “ Electronic attack through computer network towards critical infrastructure that has big potential to disturb social and economic activity of a nation.” Misused of cyberspace by Terrorist Group for specific goal. ...
Preventing Social Engineering
... More of a nuisance than a threat Spread using social engineering techniques Productivity and resource cost ...
... More of a nuisance than a threat Spread using social engineering techniques Productivity and resource cost ...
Assignment #2 S.Popovic
... Gaining full admin privileges to a IBM minicomputer at the computer learning center in LA in order to win a bet. Hacked Motorola, NEC, Nokia, and Sun Microsystems. At the time of his arrest, Kevin was the most-wanted computer criminal in the USA. Was arrested by the FBI on February 15, 1995. ...
... Gaining full admin privileges to a IBM minicomputer at the computer learning center in LA in order to win a bet. Hacked Motorola, NEC, Nokia, and Sun Microsystems. At the time of his arrest, Kevin was the most-wanted computer criminal in the USA. Was arrested by the FBI on February 15, 1995. ...
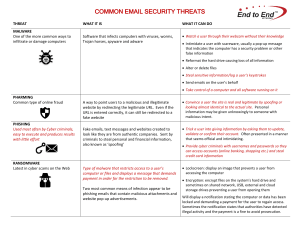
COMMON EMAIL SECURITY THREATS
... locked and demanding a payment for the user to regain access. Sometimes the notification states that authorities have detected illegal activity and the payment is a fine to avoid prosecution. ...
... locked and demanding a payment for the user to regain access. Sometimes the notification states that authorities have detected illegal activity and the payment is a fine to avoid prosecution. ...
chapter 5 – basic security
... Spam is a serious network threat that can overload ISPs, email servers and individual enduser systems. A person or organization responsible for sending spam is called a spammer. Spammers often make use of unsecured email servers to forward email. Spammers can use hacking techniques, such as vir ...
... Spam is a serious network threat that can overload ISPs, email servers and individual enduser systems. A person or organization responsible for sending spam is called a spammer. Spammers often make use of unsecured email servers to forward email. Spammers can use hacking techniques, such as vir ...
Phishing Scams - Corner Stone Credit Union
... providing personal or account information that is then used by the perpetrators to commit fraud. The term “phishing” is used to describe these scams as the fraud perpetrators are fishing to obtain personal and account information from individuals who may fall prey. These emails can take on an air of ...
... providing personal or account information that is then used by the perpetrators to commit fraud. The term “phishing” is used to describe these scams as the fraud perpetrators are fishing to obtain personal and account information from individuals who may fall prey. These emails can take on an air of ...
TMDE Web Site
... Pacific since late March ’03 • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
... Pacific since late March ’03 • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
business computer and network check list
... When staff leave my business I can prevent them from accessing all systems I have a strong password policy enforced My laptop hard disk is encrypted so if it is lost or stolen, the data remains safe Data access on my server is restricted to staff and what is needed by their role ...
... When staff leave my business I can prevent them from accessing all systems I have a strong password policy enforced My laptop hard disk is encrypted so if it is lost or stolen, the data remains safe Data access on my server is restricted to staff and what is needed by their role ...
Hacker Ethics presentation
... The hackers should share information with others within the group. They cannot brag, expose their knowledge to the outside world, spy on users, or trash systems. ...
... The hackers should share information with others within the group. They cannot brag, expose their knowledge to the outside world, spy on users, or trash systems. ...
attacks
... services based on the size and scope of the enterprise. ◦ Smaller businesses may require less protection. Email and personal encryption. ...
... services based on the size and scope of the enterprise. ◦ Smaller businesses may require less protection. Email and personal encryption. ...
Cybersecurity - Queen`s Wiki
... That could never happen to me! Think again. • Microsoft reports the ransomware attack rate in Canada is 4x higher than any other country • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in ...
... That could never happen to me! Think again. • Microsoft reports the ransomware attack rate in Canada is 4x higher than any other country • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in ...
Open ended challenge rationale
... Someone who violates computer security for malicious reasons, status or personal gain ...
... Someone who violates computer security for malicious reasons, status or personal gain ...