* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download View Presentation - InfoSec Nashville
Unix security wikipedia , lookup
Information security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Mobile security wikipedia , lookup
Disaster recovery plan wikipedia , lookup
Operation AntiSec wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Information privacy law wikipedia , lookup
Medical privacy wikipedia , lookup
Computer security wikipedia , lookup
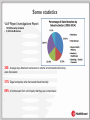
Detect and Respond… Steps to preparing and responding to a breach Jeff Lockwood, CISSP Purpose & Agenda • Educate on what we have today – Tools for Fools- All the monitoring capabilities we would want – Skilled Security Resources – Board level awareness on Data Breaches • We are still in a struggle • Goal: Identify some steps and tools to assist in implementing Incident Response Some statistics VzW Report Investigations Report - 79,790 Security Incidents - 2,122 Data Breaches 205- Average days Attackers had access to victims’ environments before they were discovered. 31% Target companies who discovered threat internally 69% of victims learn from a third party that they are compromised . What about this year 80 million records 1.1 million records 1 Million emails 850,000 records Proprietary data exposed 25 million records What are they after Hacker Pricing for Stolen Credentials (Dell SecureWorks’ Counter Threat Unit ) • “Kitz” –verified health insurance, SSN, bank account info /logins (account & routing numbers, account type), driver’s license, full name, address, phone, etc. and counterfeit physical documents and hardware related to the identity data in the package (e.g. credit cards, driver’s license, insurance cards, etc.)—ranging between $1200 – $1300 per Kitz. Add $100 – $500 for rush orders and other miscellaneous fees like wire transfer, escrow, etc. • “Fullz” – If these records also include health insurance credentials for a US victim, then they were negotiated for about $500 each, based on what was included: full names, addresses, phone numbers, e-mail addresses (with passwords), dates of birth, SSN or EIN, one or more of: bank account information (account & routing numbers, account type), online banking credentials (varying degrees of completeness), or credit card information (including full track2 data and any associated PINs) • Health Insurance Credentials – Health insurance credentials are $20 each. They include names (more than one for spouse & family coverage), date(s) of birth, contract number, group number, type of plan (Individual/Group, HMO/PPO, deductible and copay information), and insurer contact information for customer service and filing claims). Note: when there is a dental, vision, or chiropractic plan associated with the health plan, each of those was an additional $20. What are they after Fees for Additional Stolen Credentials • US credit card with CVV Code– $1 – $2 • Non-US credit card with CVV– $2 – $10 • Credit card with full track 2 and PIN– $5 – $50 • Prestige credit cards (include Platinum, Diamond, Black) with verified available balance– $20 – $400* • Online bank account, < $10K— $250 – $1000* • Compromised computer– $1 – $100 • PayPal, verified balance– $20 – $200* • Game accounts (Steam, Minecraft, WoW, PSN, XBOX Live/Microsoft)– $5 – $1000** Skype account (premium)– $1 – $10 * Some hackers’ prices are based on 4% – 12% of verified current balance ** Rare items are often “parted out’ or fenced separately What do we do – Detailed, step-by-step Incident Response Plan – Analysis of insurance policies to determine coverage – Legal counsel and key service providers “on speed dial” – Government affairs/communications with regulators – Readiness exercises that simulate an actual attack – Business continuity planning – Security audits of key vendors – Litigation and regulatory preparedness Mounting an Effective Response – – – – – – – Policy and Procedures Communication Plan and Logistics Visibility Threat Intelligence Incident Response Metrics Automations Incident Response Process Sources: NIST SP800-61 Preparation • What do we do based upon various types of incidents? (BIA helps. Start with a Policy) • When is the incident management team called? • How can governmental agencies or law enforcement help? • When do we involve law enforcement? • What resources do we need to handle an incident? • What shall we do to prevent or discourage incidents from occurring? • Where on-site & off-site shall we keep the IRP? Detection & Analysis Organization must have sufficient detection & monitoring capabilities to detect incidents in a timely manner Proactive Detection includes: • Network Intrusion Detection/Prevention System (NIDS/NIPS) • Host Intrusion Detection/Prevention System (HIDS/HIPS) • Antivirus, Endpoint Security Suite • Security Information and Event Management (Logs) • Vulnerability/audit testing • System Baselines, Sniffer • Centralized Incident Management System • Input: Server, system logs • Coordinates & co-relates logs from many systems • Tracks status of incidents to closure. Get to Root Cause Reactive Detection: Reports of unusual or suspicious activity Logs to Collect & Monitor Security Config Changes to sec. config. Authent. Failures Unauthor-ized acceses Changes to network device config. Network Irregularity Unusual packets Deleted logs Blocked packets New Users Overflowing log files Transfer of sensitive data Change in privileges Change to files: system code/data Log Issues Lockouts & expired passwd accts Outgoing IP Address Clear/ change log config Containment, Eradication & Recovery • Activate Incident Response Team to contain threat • IT/security, public relations, mgmt, business • Isolate the problem • Disable server or network zone comm. • Disable user access • Change firewall configurations to halt connection • Obtain & preserve evidence- Chain of Custody Containment - Response Technical • Collect data • Analyze log files • Obtain further technical assistance • Deploy patches & workarounds Managerial • Business impacts result in mgmt intervention, notification, escalation, approval Legal • Issues related to: investigation, prosecution, liability, privacy, laws & regulation, nondisclosure Eradication • • • • • • • • Determine how the attack occurred: who, when, how, and why? What is impact & threat? What damage occurred? Remove root cause: initial vulnerability(s) Rebuild System Talk to ISP to get more information Perform vulnerability analysis Improve defenses with enhanced protection techniques Discuss recovery with management, who must make decisions on handling affecting other areas of business Analysis • • • • • • • What happened? Who was involved? What was the reason for the attack? Where did attack originate from? When did the initial attack occur? How did it happen? What vulnerability enabled the attack? Remove root cause • • • • • If Admin or Root compromised, rebuild system Implement recent patches & recent antivirus Fortify defenses with enhanced security controls Change all passwords Retest with vulnerability analysis tools Recovery • Restore operations to normal • Ensure that restore is fully tested and operational Common Mistakes • • • • • • • • • Incident Response Plan a checklist item. ( Needs to be tailored) Plans are not tested No authority for the incident response team- Need Senior Leadership ownership and buy-in Insufficient logging & Too much logging- Know what is real and what is not Improperly trained Incident Response Team- Skills Gap Analysis Lack of documentation – Before/During/After Getting containment confused with remediation – MTTI vs MTTR No one is really in charge NO AUTOMATION!!!!!!! Questions