* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Networking Security
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cross-site scripting wikipedia , lookup
Operation AntiSec wikipedia , lookup
Cyberattack wikipedia , lookup
Wireless security wikipedia , lookup
Access control wikipedia , lookup
Rainbow table wikipedia , lookup
Denial-of-service attack wikipedia , lookup
Computer security wikipedia , lookup
Password strength wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Unix security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Mobile security wikipedia , lookup
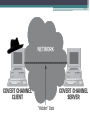
Network Security Kevin Diep Outline • The five phrases of network penetration • How to prevent exploitations and network vulnerability • Ethical issues behind such attacks Phase 1: Reconnaissance • To collect and gain information • Low-Technology Reconnaissance: Social Engineering Physical Break-In Dumpster Diving Social Engineering Social engineering involves an attacker calling employees at the target organization on the phone and duping them into revealing sensitive information • Finding pretext to obtain privileged information or services • Social engineering is deception, pure and simple. Social Engineering • Several of social engineering's "greatest hits" are A new employee calls the help desk trying to figure out how to perform a particular task on the computer. An angry manager calls a lower level employee because a password has suddenly stopped working. Social Engineering A system administrator calls an employee to fix an account on the system, which requires using a password. An employee in the field has lost some important information and calls another employee to get the remote access phone number Physical Break-In • An external attacker might try to walk through a building entrance, sneaking in with a group of employees on their way into work • An attacker might simply try grabbing a USB Thumb drive, CD, DVD, backup tape, hard drive, or even a whole computer containing sensitive data and walking out with it tucked under a coat. Dumpster Diving • Retrieving sensitive information from trash such ask discarded paper, CDs, DVDs, floppy disks, tapes, and hard drives containing sensitive data. • Dumpster diving is especially effective when used for corporate espionage Phase 1: Reconnaissance • Higher-Technology Reconnaissance: Searching the Web Using the Whois Database Reconnaissance via Searching the Web • Searching an organization’s own web site Employees’ contact information and phone numbers Clues about the corporate culture and language Business partners Recent mergers and acquisitions Server and application platforms in use Reconnaissance via Whois Database • These databases contain a variety of data elements regarding the assignment of domain names, individual contacts, and even Internet Protocol (IP) addresses Phase 2: Scanning • After the reconnaissance phase, the attacker is armed with some vital information about the target infrastructure a handful of telephone numbers, domain names, IP addresses, and technical contact information • Most attackers then use this knowledge to scan target systems looking for openings Phase 2: Scanning • War Dialing • Network Mapping • Port Scanning War-dialing attack • Searching for a modem in a target's telephone exchange to get access to a computer on their network • You can manually do it yourself or use tools that automates the task for you, dialing large pools of telephone numbers in an effort to find unprotected modems. • These tools can scan in excess of 1,000 telephone numbers in a single night using a single computer with a single phone line Phase 2: Network Mapping • Finding live hosts ICMP pings Traceroute • We can use this feature to determine the paths that packets take across a network Phase 2: Port Scanning • Used software to find open ports • Nmap, Strobe, Ultrascan Phase 2: Scanning What the Attacker Knows Tools Used to Get the Information List of addresses for live hosts on the network Ping and Cheops-ng General network topology Traceroute and Cheops-ng List of open ports on live hosts Nmap port scan List of services and versions running on the target ports Nmap version scan Operating system types of live hosts Nmap and Xprobe2 active operating system fingerprinting List of ports open through packet filters on the target network Firewalk Phase 3: Gaining Access • Gaining access to retrieve sensitive information from the victim • Use the victim as a launching platform to attack other victim • Destroy the victim file • Two methods of gaining access Gaining Access using Application and OS attacks Gaining Access using Network attacks Phase 3: Gaining Access Using Application and OS Attacks • Password attacks • Web application attacks Password Attacks • Password Guessing Attacks Users often choose passwords that are easy to remember, but are also easily guessed default passwords used by vendors left unchanged • Password Guessing Through Login Attacks run a tool that repeatedly tries to log in to the target system across the network, guessing password after password Phase 3: Password Cracking • More sophisticated and faster than password guessing through login script • Requires access to a file containing user names and encrypted passwords Phase 3: Password Cracking • A password-cracking tool can form its password guesses in a variety of ways. Words in the dictionary • Many password-cracking tools also support bruteforce cracking guesses every possible combination of characters to determine the password (a–z and 0–9) and special characters (!@#$, and so on). this brute-force guessing process can take an enormous amount of time, ranging from hours to centuries Phase 3: Gaining Access • Web Application Attacks Account Harvesting SQL Piggy Account Harvesting User ID is incorrect Password is incorrect Account Harvesting • Attackers can write a script to brute-force guessing all possible user IDs using a false password. • If an error message is returned indicating that the user ID is valid, they will store that to a file, and reverse the process and guessing the password for the successful ID they just obtained. SQL Piggybacking • Attacker may can extend an application’s SQL statement to extract or update information that the attacker is not authorized to access • Attacker will explore how the Web application interacts with the back-end database by finding a user-supplied input string that will be part of a database query Phase 3: Gaining Access Using Network Attacks • Sniffing • IP Spoofing Phase 3: Sniffing • Sniffer Allows attacker to see everything sent across the network, including userIDs and passwords • Island Hopping Attack Attacker initially takes over a machine via some exploit Attacker installs a sniffer to capture userIDs and passwords to take over other machines Phase 3: IP Spoofing • Just change your IP address to the other system's address • If the attacker just wants to send packets that look like they come from somewhere else Phase 4: Maintaining Access • Trojan Horses Software program containing a concealed malicious capability but appears to be benign, useful, or attractive to users • Backdoor Software that allows an attacker to access a machine using an alternative entry method Installed by attackers after a machine has been compromised May Permit attacker to access a computer without needing to provide account names and passwords Phase 4: Maintaining Access • Trojan Horse Backdoors Programs that combine features of backdoors and Trojan horses Not all backdoors are Trojan horses Not all Trojan horses are backdoors Programs that seem useful but allows an attacker to access a system and bypass security controls Phase 4: Maintaining Access • Categories of Trojan Horse Backdoors Application-level Trojan Horse Backdoor A separate application runs on the system that provides backdoor access to attacker Traditional RootKits Critical operating system executables are replaced by attacker to create backdoors and facilitate hiding Kernel-level RootKits Operating system kernel itself is modified to allow backdoor access and to help attacker to hide Application-level Trojan Horse Backdoor • User must be tricked into installing this application which gives attacker backdoor access and complete control over victim’s machine Back Orifice 2000 • Tricking Users to install Trojan Backdoors embed backdoor application in another innocent looking program via “wrappers” Wrapper creates one Trojan EXE application from two separate EXE programs Traditional RootKits • A suite of tools that allow an attacker to maintain root-level access via a backdoor and hiding evidence of a system compromise • More powerful than application-level Trojan horse backdoors(eg. BO2K, Netcat) since the latter run as separate programs which are easily detectable • a more insidious form of Trojan horse backdoor than application-level counterparts since existing critical system components are replaced to let attacker have backdoor access and hide • A RootKit replaces /bin/login with a modified version that includes a backdoor password for root access Kernel-Level RootKits • More sinister, devious, and nasty than traditional RootKits • Operating system kernel replaced by a Trojan horse kernel that appears to be wellbehaved but in actuality is rotten to the core • Trojanized kernel can intercept system calls and run another application chosen by atttacker • File Hiding Attacker can hide specific subdirectories and files • Process Hiding Attacker can be running Netcat listener but the kernel will not report its existence to ps • Network Hiding Attacker can tell kernel to lie to netstat about network port being used by a backdoor program Phase 5: Covering Tracks and Hiding • Hiding Evidence by Altering Event Logs Attackers like to remove evidence from logs associated with attacker’s gaining access, elevating privileges,and installing RootKits and backdoors Create hidden file from the user • Covert Channels Communication channels that disguises data while it moves across the network to avoid detection Can be used to remotely control a machine and to secretly transfer files or applications Preventing Exploitations • Rule of thumb ▫ Don’t give out sensitive information to anyone ▫ Don’t let attacker get root or administrator access on hosts ▫ Harden OS ▫ Install latest security patches ▫ Install network IDS ▫ Use antivirus tools ▫ Know your software ▫ Disable all unneeded services and ports Is hacking ethical? • http://www.computerworld.com/s/article/9154 9/Is_hacking_ethical_ • Hacktivists: Those who hack as a form of political activism. • Hobbyist hackers: Those who hack to learn, for fun or to share with other hobbyists. • Research and security hackers: Those concerned with discovering security vulnerabilities and writing the code fixes. Conclusion • “Yes, I do believe that hacking -- when properly defined -- is an ethical activity.” - By Marcia J. Wilson • http://www.youtube.com/watch?v=dBSDfo 5g2tw&feature=related