* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Access Control Policies
Cyber-security regulation wikipedia , lookup
Storm botnet wikipedia , lookup
Trusted Computing wikipedia , lookup
Computer virus wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Password strength wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Information security wikipedia , lookup
Wireless security wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Cyberattack wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer security wikipedia , lookup
Mobile security wikipedia , lookup
Social engineering (security) wikipedia , lookup
Unix security wikipedia , lookup
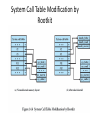
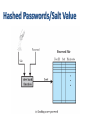
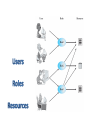
Principles of Operating Systems Lecture 19 Abhishek Dubey Daniel Balasubramanian Security Fall 2014 • Security Objectives: – Confidentiality - a loss of confidentiality is the unauthorized disclosure of information – Integrity - a loss of integrity is the unauthorized modification or destruction of information – Availability - a loss of availability is the disruption of access to or use of information or an information system THREATS TO COMPUTER SYSTEMS Stolen Credentials • One of the biggest threats • Serves as entry point for other attacks • Good security practices are required – Use strong (and different) passwords – Change passwords periodically – Do not introduce passwords where not sure if legitimate – For extra security: use multi-factor authentication methods Malware • Viruses and worms are example of malwares General term for any malicious software Software designed to cause damage to or use up the resources of a target computer Frequently concealed within or masquerades as legitimate software In some cases it spreads itself to other computers via e-mail or infected discs Infected PCs become zombies Zombies are included into a malicious network (botnet) Triggered by the attacker to perform automated tasks Rootkits and Trojans • Software that uses different techniques in order to open (and hide) a backdoor in a host/service – May behave as malware • Commonly used for (major) targeted attacks – Very sophisticated – Maintain access to the compromised hosts System Call Table Modification by Rootkit E-Mail Viruses • Attachment • Open e-mail • Uses e-mail software to replicate Worms • Use network connections to spread from system to system • Electronic mail facility – A worm mails a copy of itself to other systems 9 Worms • Remote execution capability – A worm executes a copy of itself on another system • Remote log-in capability – A worm logs on to a remote system as a user and then uses commands to copy itself from one system to the other Worm Propagation Model Bots • Zombie or drone • Program secretly takes of another Internetattached computer • Launch attacks that are difficult to trace to bot’s creator • Collection of bots is a botnet Denial of Service Attacks • (Distributed) Denial Of Service • Used to disturb online (public) services • Triggered on zombie PCs or through driven-by software • LOIC (Low Orbit Ion Cannon) software used by Anonymous PROTECTION MECHANISMS: • Serves three purposes: 1. prevents duplicate passwords from being visible in the password file » even if two users choose the same password, the passwords will be assigned different salt values 2. greatly increases the difficulty of offline dictionary attacks 3. it becomes nearly impossible to find out whether a person with passwords on two or more systems has used the same password on all of them • There are two threats to the UNIX password scheme: – a user can gain access on a machine using a guest account – Password cracker – password guessing program – If an opponent is able to obtain a copy of the password file, a cracker program can be run on another machine at leisure • this enables the opponent to run through millions of possible passwords in a reasonable period Introduction to access control • Who should have access to each resource? • Common principles for access control policies are: – blacklists – whitelists • Access generally permitted unless expressly forbidden – If your name is on the list, you will be denied access – These are the sites that you are not permitted to visit • Access is generally forbidden unless expressly permitted – If your name is on the list, you will be granted access – These are the only sites that you are permitted to visit Principle of Least privilege • Access is generally restricted to the minimum resources and authorizations required for an entity to perform their day-today function • Intended to limit the level of damage if a security incident occurs • Where the resource is information, may be known as need to know principle – Only given information needed now to perform your job Terminology • Subjects – Entities requesting access to a resource • Examples: Person (User), Process, Device – This is an active role: • Entity initiates access request and is user of information • Objects – Resources or entities which contain information • Examples: Disks, files, records, directories – This is a passive role • Object is repository for information, the resources that a subject tries to access • Dictates what types of access are permitted, under what circumstances, and by whom • Access control policies are generally grouped into the following categories: – Discretionary access control (DAC) – controls access based on the identity of the requestor and on access rules stating what requestors are (or are not) allowed to do – Mandatory access control (MAC) – controls access based on comparing security labels with security clearances – Role-based access control (RBAC) – controls access based on the roles that users have within the system and on rules stating what accesses are allowed to users in given roles Discretionary Access Control Access rights to an object or resource are granted at the discretion of the owner • For example, the security administrator, the owner of the resource, or the person who created the asset – DAC is discretionary in the sense that a subject with a certain access authorization is capable of passing that authorization (directly or indirectly) to any other subject. – Often implemented access control lists or matrices – Popular operating systems use DAC. Discretionary Access Control DAC in Apple OS X/Unix/Linux – Object on each line – Permissions indicated for • Owner • Group, and • Other – Type of permissions • r read • w write • x execute Mandatory Access Control • A central authority assigns attributes to objects and to subjects – For example: clearance and classification levels • A system-wide set of rules is formed relating the attributes of the objects and subjects to the modes of access that are permitted • MAC is mandatory in the sense that entities are not able to decide which other entities they want to allow to access resources, the system rules apply the system denies users full control over access to the resources they create Mandatory Access Control Example Categories • Based on the roles that users assume in a system rather than the user’s identity • Models define a role as a job function within an organization • Systems assign access rights to roles instead of individual users • in turn, users are assigned to different roles, either statically or dynamically, according to their responsibilities • NIST has issued a standard that requires support for access control and administration through roles • Intrusion detection is based on the assumption that the behavior of the intruder differs from that of a legitimate user in ways that can be quantified • If an intrusion is detected quickly enough, the intruder can be identified and ejected from the system before any damage is done or any data are compromised • An effective IDS can serve as a deterrent, thus acting to prevent intrusions • Intrusion detection enables the collection of information about intrusion techniques that can be used to strengthen instrusion prevention measures • Monitors activity on the system in a variety of ways to detect suspicious behavior • Primary purpose is to detect intrusions, log suspicious events, and send alerts • Can detect both external and internal intrusions • Anomaly detection – collection of data relating to behavior of legitimate users over time • threshold detection • profile based detection • Signature detection – define a set of rules or attack patterns that can be used to decide that a given behavior is that of an intruder • Ideal solution to the threat of viruses is prevention, don’t allow a virus onto the system in the first place! • That goal is, in general, impossible to achieve, although prevention can reduce the number of successful viral attacks – If detection succeeds but either identification or removal is not possible, then the alternative is to discard the infected program and reload a clean backup version Detection once the infection has occurred, determine that it has occurred and locate the virus Identification once detection has been achieved, identify the specific virus that has infected a program Removal once the specific virus has been identified, remove all traces of the virus from the infected program and restore it to its original state remove the virus from all infected systems so that the disease cannot spread further Botnet • • IDS and digital immune systems are useful against bots • once bots are activated and an attack is underway these countermeasures can be used to detect the attack The primary objective is to try to detect and disable the botnet during its construction phase Rootkit • • • • • • Can be difficult to detect and neutralize Many of the administrative tools can be compromised Countering rootkits requires a varitey of network and computer level security tools Network-based and host-based intrusion detection systems can look for the code signatures of known rootkit attacks in incoming traffic Host based anitvirus software can also be used to recognize the known signatures Do some sort of integrity check Protection from stack buffer overflows can be broadly classified into two categories: Compile-time defenses • aims to harden programs to resist attacks in new programs Stack protection mechanisms • aims to detect and abort attacks in existing programs • Aim to prevent or detect buffer overflows by instrumenting programs when they are compiled • Choice of Programming Language • Safe Coding Techniques • Language Extensions and Use of Safe Libraries • Stack Protection Mechanisms Address space randomization Executable address space protection Guard pages These defenses involve changes to the memory management of the virtual address space of processes • Authentication • password based • token based • biometric • Access control • discretionary • role-based • Intrusion detection • host-based • audit records • Malware defense – – – – antivirus approaches worm countermeasures bot countermeasures rootkit countermeasures – Buffer overflow attacks – compile-time defenses – real-time defenses