* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download doc.gold.ac.uk
Information security wikipedia , lookup
Distributed firewall wikipedia , lookup
Cross-site scripting wikipedia , lookup
Signals intelligence wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Computer recycling wikipedia , lookup
Unix security wikipedia , lookup
Cryptography wikipedia , lookup
History of cryptography wikipedia , lookup
Cyberattack wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Wireless security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Social engineering (security) wikipedia , lookup
Mobile security wikipedia , lookup
Computer security wikipedia , lookup
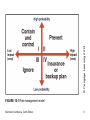
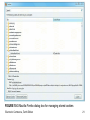
Electronic Commerce Tenth Edition Chapter 10 Electronic Commerce Security Learning Objectives In this chapter, you will learn: • What security risks arise in online business and how to manage them • How to create a security policy • How to implement security on Web client computers • How to implement security in the communication channels between computers Electronic Commerce, Tenth Edition 2 Learning Objectives (cont’d.) • How to implement security on Web server computers • What organizations promote computer, network, and Internet security Electronic Commerce, Tenth Edition 3 Online Security Issues Overview • Early Internet days – Most popular use: electronic mail • Today’s higher stakes – Electronic mail, shopping, all types of financial transactions • Common worry of Web shoppers – Stolen credit card as it transmits over the Internet – More likely to be stolen from computer where stored • Chapter topic: security in the context of electronic commerce Electronic Commerce, Tenth Edition 4 Origins of Security on Interconnected Computer Systems • Data security measures taken by Roman Empire – Coded information to prevent enemies from reading secret war and defense plans • Modern electronic security techniques – Defense Department wartime use • “Orange Book”: rules for mandatory access control • Business computers – Initially adopted military’s security methods • Today’s computing – Requires comprehensive computer security plans Electronic Commerce, Tenth Edition 5 Computer Security and Risk Management • Computer security – Asset protection from unauthorized access, use, alteration, and destruction • Physical security – Includes tangible protection devices • Alarms, guards, fireproof doors, security fences, safes or vaults, and bombproof buildings • Logical security – Asset protection using nonphysical means Electronic Commerce, Tenth Edition 6 Computer Security and Risk Management (cont’d.) • Threat – Any act or object posing danger to computer assets • Countermeasure – Procedure (physical or logical) • Recognizes, reduces, and eliminates threat – Extent and expense of countermeasures • Vary depending on asset importance Electronic Commerce, Tenth Edition 7 Computer Security and Risk Management (cont’d.) • Risk management model – Four general organizational actions • Impact (cost) and probability of physical threat – Also applicable for protecting Internet and electronic commerce assets from physical and electronic threats • Electronic threat examples: – Impostors, eavesdroppers, thieves • Eavesdropper (person or device) – Listen in on and copy Internet transmissions Electronic Commerce, Tenth Edition 8 © Cengage Learning 2013 FIGURE 10-1 Risk management model Electronic Commerce, Tenth Edition 9 Computer Security and Risk Management (cont’d.) • Crackers or hackers (people) – Write programs; manipulate technologies • Obtain unauthorized access to computers and networks • White hat hacker and black hat hacker – Distinction between good hackers and bad hackers • Good security scheme implementation – Identify risks – Determine how to protect threatened assets – Calculate costs to protect assets Electronic Commerce, Tenth Edition 10 Elements of Computer Security • Secrecy – Protecting against unauthorized data disclosure – Ensuring data source authenticity • Integrity – Preventing unauthorized data modification – Man-in-the-middle exploit • E-mail message intercepted; contents changed before forwarded to original destination • Necessity – Preventing data delays or denials (removal) – Delaying message or completely destroying it Electronic Commerce, Tenth Edition 11 Establishing a Security Policy • Security policy – Assets to protect and why, protection responsibility, acceptable and unacceptable behaviors – Physical security, network security, access authorizations, virus protection, disaster recovery • Military policy: stresses separation of multiple levels of security • Corporate information classifications – Public – Company confidential Electronic Commerce, Tenth Edition 12 Establishing a Security Policy (cont’d.) • Steps to create security policy – – – – – Determine assets to protect from threats Determine access to various system parts Identify resources to protect assets Develop written security policy Commit resources • Comprehensive security plan goals – Protect privacy, integrity, availability; authentication – Selected to satisfy Figure 10-2 requirements Electronic Commerce, Tenth Edition 13 © Cengage Learning 2013 FIGURE 10-2 Requirements for secure electronic commerce Electronic Commerce, Tenth Edition 14 Establishing a Security Policy (cont’d.) • Security policies information sources – WindowSecurity.com site – Information Security Policy World site • Absolute security: difficult to achieve – Create barriers deterring intentional violators – Reduce impact of natural disasters and terrorist acts • Integrated security – Having all security measures work together • Prevents unauthorized disclosure, destruction, modification of assets Electronic Commerce, Tenth Edition 15 Establishing a Security Policy (cont’d.) • Security policy points – Authentication: Who is trying to access site? – Access control: Who is allowed to log on to and access site? – Secrecy: Who is permitted to view selected information? – Data integrity: Who is allowed to change data? – Audit: Who or what causes specific events to occur, and when? Electronic Commerce, Tenth Edition 16 Security for Client Computers • Client computers – Must be protected from threats • Threats – Originate in software and downloaded data – Malevolent server site masquerades as legitimate Web site • Chapter topics organized to follow the transaction-processing flow – Beginning with consumer – Ending with Web server at electronic commerce site Electronic Commerce, Tenth Edition 17 Cookies and Web Bugs • Internet connection between Web clients and servers – Stateless connection • Each information transmission is independent • No continuous connection (open session) maintained between any client and server • Cookies – Small text files Web servers place on Web client – Identify returning visitors – Allow continuing open session Electronic Commerce, Tenth Edition 18 Cookies and Web Bugs (cont’d.) • Time duration cookie categories – Session cookies: exist until client connection ends – Persistent cookies: remain indefinitely – Electronic commerce sites use both • Cookie sources – First-party cookies • Web server site places them on client computer – Third-party cookies • Different Web site places them on client computer Electronic Commerce, Tenth Edition 19 Cookies and Web Bugs (cont’d.) • Disable cookies entirely – Complete cookie protection – Problem • Useful cookies blocked (along with others) • Full site resources not available • Web browser cookie management functions – Refuse only third-party cookies – Review each cookie before accepted – Provided by most Web browsers Electronic Commerce, Tenth Edition 20 FIGURE 10-3 Mozilla Firefox dialog box for managing stored cookies Electronic Commerce, Tenth Edition 21 Cookies and Web Bugs (cont’d.) • Web bug – Tiny graphic that third-party Web site places on another site’s Web page – Purpose • Provide a way for a third-party site to place cookie on visitor’s computer • Internet advertising community: – Calls Web bugs “clear GIFs” or “1-by-1 GIFs” • Graphics created in GIF format • Color value of “transparent,” small as 1 pixel by 1 pixel Electronic Commerce, Tenth Edition 22 Active Content • Active content – Programs embedded transparently in Web pages – Cause action to occur – E-commerce example • Place items into shopping cart; compute tax and costs • Advantages – Extends HTML functionality – Moves data processing chores to client computer • Disadvantages – Can damage client computer Electronic Commerce, Tenth Edition 23 Active Content (cont’d.) • Cookies, Java applets, JavaScript, VBScript, ActiveX controls, graphics, Web browser plug-ins, e-mail attachments • Scripting languages: provide executable script – Examples: JavaScript and VBScript • Applet: small application program – Typically runs within Web browser • Some browsers include tools limiting applets’ actions • Active content modules – Embedded in Web pages (invisible) Electronic Commerce, Tenth Edition 24 FIGURE 10-4 Advanced JavaScript settings in Mozilla Firefox Electronic Commerce, Tenth Edition 25 Active Content (cont’d.) • Crackers: embed malicious active content • Trojan horse – Program hidden inside another program or Web page • Masking true purpose – May result in secrecy and integrity violations • Zombie (Trojan horse) – Secretly takes over another computer – Launches attacks on other computers • Botnet (robotic network, zombie farm) – All controlled computers act as an attacking unit Electronic Commerce, Tenth Edition 26 Java Applets • Java programming language – Developed by Sun Microsystems – Widespread use in Web pages: active content • Java: platform-independent programming language – – – – Provides Web page active content Server sends applets with client-requested pages Most cases: operation visible to visitor Possibility: functions not noticed by visitor Electronic Commerce, Tenth Edition 27 Java Applets (cont’d.) • Advantages – Adds functionality to business application’s functionality; relieves server-side programs • Disadvantage – Possible security violations (Trojan horse, zombie) Electronic Commerce, Tenth Edition 28 Java Applets (cont’d.) • Java sandbox – Confines Java applet actions to set of rules defined by security model – Rules apply to all untrusted Java applets • Not established as secure – Java applets running within sandbox constraint • Does not allow full client system access • Prevents secrecy (disclosure) and integrity (deletion or modification) violations Electronic Commerce, Tenth Edition 29 JavaScript • JavaScript – – – – Scripting language developed by Netscape Enables Web page designers to build active content Based loosely on Sun’s Java programming language Can be used for attacks • Cannot commence execution on its own • User must start ill-intentioned JavaScript program Electronic Commerce, Tenth Edition 30 ActiveX Controls • ActiveX control – Objects containing programs and properties Web designers place on Web pages • Component construction – Many different programming languages • Common: C++ and Visual Basic • Run on Windows operating systems computers • Executed on client computer like any other program Electronic Commerce, Tenth Edition 31 ActiveX Controls (cont’d.) • Comprehensive ActiveX controls list – ActiveX page at Download.com • Security danger – Execute like other client computer programs – Have access to full system resources • Cause secrecy, integrity, and necessity violations – Actions cannot be halted once started • Web browsers – Provide notice of Active-X download or install Electronic Commerce, Tenth Edition 32 FIGURE 10-5 ActiveX control download warning dialog box in Internet Explorer Electronic Commerce, Tenth Edition 33 Graphics and Plug-Ins • Graphics, browser plug-ins, and e-mail attachments can harbor executable content • Graphic: embedded code can harm client computer • Browser plug-ins (programs) – Enhance browser capabilities – Popular plug-ins: Adobe Flash Player, Apple’s QuickTime Player, Microsoft Silverlight, RealNetworks’ RealPlayer – Can pose security threats • 1999 RealPlayer plug-in • Plug-ins executing commands buried within media Electronic Commerce, Tenth Edition 34 Viruses, Worms, and Antivirus Software • Programs display e-mail attachments by automatically executing associated programs – Macro viruses within attached files can cause damage • Virus: software – Attaches itself to another program – Causes damage when host program activated • Worm: virus – Replicates itself on computers it infects – Spreads quickly through the Internet • Macro virus – Small program (macro) embedded in file Electronic Commerce, Tenth Edition 35 Viruses, Worms, and Antivirus Software (cont’d.) • ILOVEYOU virus (“love bug”) – – – – Spread with amazing speed Infected computers and clogged e-mail systems Replicated itself explosively through Outlook e-mail Caused other harm • 2001 Code Red and Nimda: virus-worm combinations – Multivector virus: entered computer system in several different ways (vectors) • 2002 and 2003: new virus-worm combinations – Example: Bugbear Electronic Commerce, Tenth Edition 36 Viruses, Worms, and Antivirus Software (cont’d.) • Antivirus software – Detects viruses and worms – Either deletes or isolates them on client computer • 2005 and 2006 Zotob – New breed of Trojan horse-worm combination • 2007: Storm virus • 2008 and continuing into 2009: Conflicker • 2009 and 2010: URLzone and Clampi – New viruses designed specifically to hijack users’ online banking sessions Electronic Commerce, Tenth Edition 37 Viruses, Worms, and Antivirus Software (cont’d.) • 2010: new Trojan horse-worm combination attack – Spread through a computer operating system – Designed to target industrial equipment • German industrial giant Siemens’ control systems • 2011: Zeus and SpyEye combined – Targeted bank account information – Not visible in Microsoft Windows Task Manager – Intercept credit card or online banking data entered in Web browser Electronic Commerce, Tenth Edition 38 FIGURE 10-6 Major viruses, worms, and Trojan horses Electronic Commerce, Tenth Edition 39 FIGURE 10-6 Major viruses, worms, and Trojan horses (continued) Electronic Commerce, Tenth Edition 40 FIGURE 10-6 Major viruses, worms, and Trojan horses (continued) Electronic Commerce, Tenth Edition 41 FIGURE 10-6 Major viruses, worms, and Trojan horses (continued) Electronic Commerce, Tenth Edition 42 FIGURE 10-6 Major viruses, worms, and Trojan horses (continued) Electronic Commerce, Tenth Edition 43 FIGURE 10-6 Major viruses, worms, and Trojan horses (continued) Electronic Commerce, Tenth Edition 44 Viruses, Worms, and Antivirus Software (cont’d.) • Companies that track viruses, sell antivirus software, provide virus descriptions on Web sites – Symantec (Symantec Security Response) – McAfee (McAfee Virus Information) • Data files must be updated regularly – Recognize and eliminate newest viruses • Some Web e-mail systems: – Provide and update antivirus software • Used to scan attachments before downloading – Example: Yahoo! Mail Electronic Commerce, Tenth Edition 45 Digital Certificates • Digital certificate (digital ID) – E-mail message attachment or program embedded in Web page – Verifies sender or Web site – Contains a means to send encrypted message – Signed message or code • Provides proof of holder identified by the certificate – Used for online transactions • Electronic commerce, electronic mail, and electronic funds transfers Electronic Commerce, Tenth Edition 46 © Cengage Learning 2013 FIGURE 10-7 Delmar Cengage Learning’s digital certificate information displayed in Firefox browser Electronic Commerce, Tenth Edition 47 Digital Certificates (cont’d.) • Digital certificate for software: – Assurance software was created by specific company – Does not attest to quality of software • Certification authority (CA) – Issues digital certificates to organizations, individuals • Digital certificates cannot be forged easily • Six main elements: owner’s identifying information, owner’s public key, dates certificate is valid, serial number, issuer name, issuer digital signature Electronic Commerce, Tenth Edition 48 Digital Certificates (cont’d.) • Key – Number: usually long binary number • Used with encryption algorithm • “Lock” message characters being protected – Longer keys provide better protection • Identification requirements vary – Driver’s license, notarized form, fingerprints • Companies offering CA services – Thawte, VeriSign, Comodo, DigiCert, Entrust, GeoTrust, RapidSSL.com Electronic Commerce, Tenth Edition 49 Digital Certificates (cont’d.) • Secure Sockets Layer-Extended Validation (SSL-EV) digital certificate – Issued after more extensive verification confirmed • Annual fees – $200 to more than $1500 • Digital certificates expire after period of time – Provides protection (users and businesses) – Must submit credentials for reevaluation periodically Electronic Commerce, Tenth Edition 50 FIGURE 10-8 Internet Explorer address window display for an SSL-EV Web site Electronic Commerce, Tenth Edition 51 Steganography • Steganography – Hiding information within another piece of information • Can be used for malicious purposes • Hiding encrypted file within another file – Casual observer cannot detect anything of importance in container file – Two-step process • Encrypting file protects it from being read • Steganography makes it invisible • Al Qaeda used steganography to hide attack orders Electronic Commerce, Tenth Edition 52 Physical Security for Clients • Client computers – Control important business functions – Same physical security as early systems • New physical security technologies – Fingerprint readers (less than $100) • Stronger protection than password approaches • Biometric security device – Identification using element of person’s biological makeup • Writing pads, eye scanners, palm reading scanners, reading back of hand vein pattern Electronic Commerce, Tenth Edition 53 Client Security for Mobile Devices • Security measures – Access password – Remote wipe: clears all personal data • Can be added as an app • Capability through corporate e-mail synchronization – Antivirus software • Rogue apps: contain malware or collect information and forward to perpetrators – Apple App Store tests apps before authorizing sales – Android Market does less extensive testing – Users should not rush to install latest app Electronic Commerce, Tenth Edition 54 Communication Channel Security • Internet – Not designed to be secure – Designed to provide redundancy • Remains unchanged from original insecure state – Message traveling on the Internet • Subject to secrecy, integrity, and necessity threats Electronic Commerce, Tenth Edition 55 Secrecy Threats • Secrecy – Prevention of unauthorized information disclosure – Technical issue • Requiring sophisticated physical and logical mechanisms • Privacy – Protection of individual rights to nondisclosure – Legal matter Electronic Commerce, Tenth Edition 56 Secrecy Threats (cont’d.) • E-mail message – Secrecy violations protected using encryption • Protects outgoing messages – Privacy issues address whether supervisors are permitted to read employees’ messages randomly • Electronic commerce threat – Sensitive or personal information theft – Sniffer programs • Record information passing through computer or router Electronic Commerce, Tenth Edition 57 Secrecy Threats (cont’d.) • Electronic commerce threat (cont’d.) – Backdoor: electronic holes • Left open accidentally or intentionally • Content exposed to secrecy threats • Example: Cart32 shopping cart program backdoor – Stolen corporate information • Eavesdropper example • Web users continually reveal information – Secrecy breach – Possible solution: anonymous Web surfing Electronic Commerce, Tenth Edition 58 Integrity Threats • Also known as active wiretapping – Unauthorized party alters message information stream • Integrity violation example – Cybervandalism • Electronic defacing of Web site • Masquerading (spoofing) – Pretending to be someone else – Fake Web site representing itself as original Electronic Commerce, Tenth Edition 59 Integrity Threats (cont’d.) • Domain name servers (DNSs) – Internet computers maintaining directories • Linking domain names to IP addresses – Perpetrators use software security hole • Substitute their Web site address in place of real one • Spoofs Web site visitors • Phishing expeditions – Capture confidential customer information – Common victims • Online banking, payment system users Electronic Commerce, Tenth Edition 60 Necessity Threats • Also known as delay, denial, denial-of-service (DoS) attack – Disrupt or deny normal computer processing – Intolerably slow-speed computer processing • Renders service unusable or unattractive • Distributed denial-of-service (DDoS) attack – Launch simultaneous attack on a Web site via botnets • DoS attacks – Remove information altogether – Delete transmission or file information Electronic Commerce, Tenth Edition 61 Necessity Threats (cont’d.) • Denial attack examples: – Quicken accounting program diverted money to perpetrator’s bank account – High-profile electronic commerce company received flood of data packets • Overwhelmed sites’ servers • Choked off legitimate customers’ access Electronic Commerce, Tenth Edition 62 Threats to the Physical Security of Internet Communications Channels • Internet’s packet-based network design: – Precludes it from being shut down • By attack on single communications link • Individual user’s Internet service can be interrupted – Destruction of user’s Internet link • Larger companies, organizations – Use more than one link to main Internet backbone Electronic Commerce, Tenth Edition 63 Threats to Wireless Networks • Wireless Encryption Protocol (WEP) – Rule set for encrypting transmissions from the wireless devices to the wireless access points (WAPs) • Wardrivers – Attackers drive around in cars – Search for accessible networks • Warchalking – Place chalk mark on building • Identifies easily entered wireless network nearby – Web sites include wireless access locations maps Electronic Commerce, Tenth Edition 64 Threats to Wireless Networks (cont’d.) • Preventing attacks by wardrivers – Turn on WEP – Change default login and password settings • Example – Best Buy wireless point-of-sale (POS) • Failed to enable WEP • Customer launched sniffer program • Intercepted data from POS terminals Electronic Commerce, Tenth Edition 65 Encryption Solutions • Encryption: coding information using mathematically based program, secret key • Cryptography: science studying encryption – Science of creating messages only sender and receiver can read • Steganography – Makes text undetectable to naked eye • Cryptography converts text to other visible text – With no apparent meaning Electronic Commerce, Tenth Edition 66 Encryption Solutions (cont’d.) • Encryption algorithms – Encryption program • Transforms normal text (plain text) into cipher text (unintelligible characters string) – Encryption algorithm • Logic behind encryption program • Includes mathematics to do transformation – Decryption program • Encryption-reversing procedure: message is decoded or decrypted Electronic Commerce, Tenth Edition 67 Encryption Solutions (cont’d.) • Encryption algorithms (cont’d.) – National Security Agency controls dissemination – U.S. government banned publication of details • Illegal for U.S. companies to export – Encryption algorithm property • May know algorithm details • Unable to decipher encrypted message without knowing key encrypting the message – Key type subdivides encryption into three functions • Hash coding, asymmetric encryption, symmetric encryption Electronic Commerce, Tenth Edition 68 Encryption Solutions (cont’d.) • Hash coding – Process uses Hash algorithm – Calculates number (hash value) from any length message – Unique message fingerprint – Good hash algorithm design • Probability of collision is extremely small (two different messages resulting in same hash value) – Determining message alteration during transit • Mismatch between original hash value and receiver computed value Electronic Commerce, Tenth Edition 69 Encryption Solutions (cont’d.) • Asymmetric encryption (public-key encryption) – Encodes messages using two mathematically related numeric keys – Public key: one key freely distributed to public • Encrypt messages using encryption algorithm – Private key: second key belongs to key owner • Kept secret • Decrypt all messages received Electronic Commerce, Tenth Edition 70 Encryption Solutions (cont’d.) – Pretty Good Privacy (PGP) – Software tools using different encryption algorithms • Perform public key encryption – Individuals download free versions • PGP Corporation site, PGP International site • Encrypt e-mail messages – Sells business site licenses Electronic Commerce, Tenth Edition 71 Encryption Solutions (cont’d.) • Symmetric encryption (private-key encryption) – Encodes message with one of several available algorithms • Single numeric key to encode and decode data – Message receiver must know the key – Very fast and efficient encoding and decoding – Key must be guarded Electronic Commerce, Tenth Edition 72 Encryption Solutions (cont’d.) – Problems • Difficult to distribute new keys to authorized parties while maintaining security, control over keys • Private keys do not work well in large environments – Data Encryption Standard (DES) • Encryption algorithms adopted by U.S. government • Most widely used private-key encryption system • Fast computers break messages encoded with smaller keys Electronic Commerce, Tenth Edition 73 Encryption Solutions (cont’d.) – Triple Data Encryption Standard (Triple DES, 3DES) • Stronger version of Data Encryption Standard – Advanced Encryption Standard (AES) • Alternative encryption standard • Most government agencies use today – Longer bit lengths increase difficulty of cracking keys Electronic Commerce, Tenth Edition 74 Encryption Solutions (cont’d.) • Comparing asymmetric and symmetric encryption systems – Advantages of public-key (asymmetric) systems • Small combination of keys required • No problem in key distribution • Implementation of digital signatures possible – Disadvantages of public-key systems • Significantly slower than private-key systems – Public-key systems: complement rather than replace private-key systems Electronic Commerce, Tenth Edition 75 © Cengage Learning 2013 FIGURE 10-9 Comparison of (a) hash coding, (b) private-key, and (c) public-key encryption Electronic Commerce, Tenth Edition 76 Encryption Solutions (cont’d.) – Web servers accommodate encryption algorithms • Must communicate with variety of Web browsers – Secure Sockets Layer (SSL) • Goal: secures connections between two computers – Secure Hypertext Transfer Protocol (S-HTTP) • Goal: send individual messages securely Electronic Commerce, Tenth Edition 77 Encryption Solutions (cont’d.) • Secure sockets layer (SSL) protocol – Provides security “handshake” – Client and server exchange brief burst of messages – All communication encoded • Eavesdropper receives unintelligible information – Secures many different communication types • HTTP, FTP, Telnet – HTTPS: protocol implementing SSL • Precede URL with protocol name HTTPS Electronic Commerce, Tenth Edition 78 Encryption Solutions (cont’d.) – Encrypted transaction generates private session key • Bit lengths vary (40-bit, 56-bit, 128-bit, 168-bit) – Session key • Used by encryption algorithm • Creates cipher text from plain text during single secure session – Secrecy implemented using public-key and privatekey encryption • Private-key encryption for nearly all communications Electronic Commerce, Tenth Edition 79 © Cengage Learning 2013 FIGURE 10-10 Establishing an SSL session Electronic Commerce, Tenth Edition 80 Encryption Solutions (cont’d.) – After secure session established: • Public-key encryption no longer used • Message transmission protected by private-key encryption • Session key (private key) discarded when session ends – Each new connection between client and secure server requires entire process: • Beginning with handshake Electronic Commerce, Tenth Edition 81 Encryption Solutions (cont’d.) • Secure HTTP (S-HTTP) – Extension to HTTP providing security features • Client and server authentication, spontaneous encryption, request/response nonrepudiation – Symmetric encryption for secret communications – Public-key encryption to establish client/server authentication – Session negotiation: process between client and server of proposing and accepting (or rejecting) various transmission conditions Electronic Commerce, Tenth Edition 82 Encryption Solutions (cont’d.) – Establishing secure session • SSL carries out client-server handshake exchange to set up secure communication • S-HTTP sets up security details with special packet headers exchanged in S-HTTP – Headers define security technique type – Header exchanges state: • Which specific algorithms that each side supports • Whether client or server (or both) supports algorithm • Whether security technique required, optional, refused Electronic Commerce, Tenth Edition 83 Encryption Solutions (cont’d.) – Secure envelope (complete package) • Encapsulates message • Provides secrecy, integrity, and client/server authentication • SSL has become: – More generally accepted standard over S-HTTP Electronic Commerce, Tenth Edition 84 Using a Hash Function to Create a Message Digest • Integrity violation – Message altered while in transit • Difficult and expensive to prevent • Security techniques to detect • Harm: unauthorized message changes undetected • Apply two algorithms to eliminate fraud and abuse – Hash algorithm – Message digest • Number summarizing encrypted information Electronic Commerce, Tenth Edition 85 Converting a Message Digest into a Digital Signature • Hash functions: potential for fraud – Solution: sender encrypts message digest using private key • Digital signature – Encrypted message digest (message hash value) • Digital signature provides: – Integrity, nonrepudiation, and authentication • Provide transaction secrecy – Encrypt entire string (digital signature, message) • Digital signatures: same legal status as traditional signatures Electronic Commerce, Tenth Edition 86 © Cengage Learning 2013 FIGURE 10-11 Sending and receiving a digitally signed message Electronic Commerce, Tenth Edition 87 Security for Server Computers • Server vulnerabilities – Exploited by anyone determined to cause destruction or acquire information illegally • Entry points – Web server and its software – Any back-end programs containing data • No system is completely safe • Web server administrator – Ensures security policies documented; considered in every electronic commerce operation Electronic Commerce, Tenth Edition 88 Web Server Threats • Compromise of secrecy – By allowing automatic directory listings – Solution: turn off folder name display feature • Sensitive file on Web server – Holds Web server username-password pairs – Solution: store authentication information in encrypted form Electronic Commerce, Tenth Edition 89 Web Server Threats (cont’d.) • Passwords that users select – Easily guessable • Dictionary attack programs cycle through electronic dictionary, trying every word as password – Solutions • User password requirements • Use password assignment software to check user password against dictionary • Help creating very strong passwords: – Gibson Research Corporation’s Ultra High Security Password Generator Electronic Commerce, Tenth Edition 90 © Cengage Learning 2013 FIGURE 10-12 Examples of passwords, from very weak to very strong Electronic Commerce, Tenth Edition 91 Database Threats • Usernames and passwords – Stored in unencrypted table – Database fails to enforce security altogether • Relies on Web server to enforce security • Unauthorized users – Masquerade as legitimate database users • Trojan horse programs hide within database system – Reveal information – Remove all access controls within database Electronic Commerce, Tenth Edition 92 Other Programming Threats • Java or C++ programs executed by server – Passed to Web servers by client – Reside on server – Use a buffer • Memory area set aside holding data read from file or database – Buffer overrun (buffer overflow) error • • • • Programs filling buffers malfunction and overfill buffer Excess data spilled outside designated buffer memory Cause: error in program or intentional 1998 Internet worm Electronic Commerce, Tenth Edition 93 Other Programming Threats (cont’d.) • Insidious version of buffer overflow attack – Writes instructions into critical memory locations – Web server resumes execution by loading internal registers with address of attacking program’s code • Reducing potential buffer overflow damage – Good programming practices – Some hardware functionality • Mail bomb attack – Hundreds (thousands) send message to particular address Electronic Commerce, Tenth Edition 94 Threats to the Physical Security of Web Servers • Protecting Web servers – Put computers in commerce service provider (CSP) facility • Very high-level physical security on CSP – Maintain server content’s backup copies at remote location – Rely on service providers • Offer managed services including Web server security – Hire smaller, specialized security service providers Electronic Commerce, Tenth Edition 95 Access Control and Authentication • Controlling who and what has access to Web server • Authentication – Identity verification of entity requesting computer access • Server user authentication – Server must successfully decrypt user’s digital signature-contained certificate – Server checks certificate timestamp – Server uses callback system • Certificates authenticate client computers and their users Electronic Commerce, Tenth Edition 96 Access Control and Authentication (cont’d.) • Usernames and passwords – Provide some protection element • Maintain usernames in plain text – Encrypt passwords with one-way encryption algorithm • Problem – Site visitor may save username and password as a cookie • Might be stored in plain text • Access control list (ACL) – Restrict file access to selected users Electronic Commerce, Tenth Edition 97 Firewalls • Firewall – Software, hardware-software combination – Installed in a network to control packet traffic • Placed at Internet entry point of network – Defense between network and the Internet • Between network and any other network • Principles – All traffic must pass through it – Only authorized traffic allowed to pass – Immune to penetration Electronic Commerce, Tenth Edition 98 Firewalls (cont’d.) • • • • Trusted: networks inside firewall Untrusted: networks outside firewall Filter permits selected messages though network Separate corporate networks from one another – Coarse need-to-know filter • Firewalls segment corporate network into secure zones • Large organizations with multiple sites – Install firewall at each location • All locations follow same security policy Electronic Commerce, Tenth Edition 99 Firewalls (cont’d.) • Should be stripped of unnecessary software • Packet-filter firewalls – Examine all data flowing back and forth between trusted network (within firewall) and the Internet • Gateway servers – Filter traffic based on requested application – Limit access to specific applications • Telnet, FTP, HTTP • Proxy server firewalls – Communicate with the Internet on private network’s behalf Electronic Commerce, Tenth Edition 100 Firewalls (cont’d.) • Perimeter expansion problem – Computers outside traditional physical site boundary • Servers under almost constant attack – Install intrusion detection systems • Monitor server login attempts • Analyze for patterns indicating cracker attack • Block further attempts originating from same IP address • Cloud computing: firewall products lagging behind • Personal firewalls – Software-only firewalls on individual client computers – Gibson Research Shields Up! Web site Electronic Commerce, Tenth Edition 101 Organizations that Promote Computer Security • Following the Internet Worm of 1988 – Organizations formed to share information • About threats to computer systems • Principle followed – Sharing information about attacks and defenses for attacks • Helps everyone create better computer security Electronic Commerce, Tenth Edition 102 CERT • Computer Emergency Response Team • Housed at Carnegie Mellon University – Software Engineering Institute • Maintains effective, quick communications infrastructure among security experts – Security incidents avoided, handled quickly • Provides security risk information • Posts security event alerts • Primary authoritative source for viruses, worms, and other types of attack information Electronic Commerce, Tenth Edition 103 Other Organizations • 1989: System Administrator, Audit, Network and Security (SANS) Institute – Education and research efforts • Research reports, security alerts, and white papers – SANS Internet Storm Center Web site • Current information on location, intensity of computer attacks worldwide • CERIAS (Center for Education and Research in Information Assurance and Security) – Multidisciplinary information security research and education Electronic Commerce, Tenth Edition 104 Other Organizations (cont’d.) • Center for Internet Security – Not-for-profit cooperative organization – Helps electronic commerce companies • CSO Online – Articles from CSO Magazine – Computer security-related news items • Infosecurity.com – Articles about all types of online security issues Electronic Commerce, Tenth Edition 105 Computer Forensics and Ethical Hacking • Computer forensics experts (ethical hackers) – Computer sleuths hired to probe PCs – Locate information usable in legal proceedings – Job of breaking into client computers • Computer forensics field – Responsible for collection, preservation, and computer-related evidence analysis • Companies hire ethical hackers to test computer security safeguards Electronic Commerce, Tenth Edition 106 Summary • Physical and logical computer security important in electronic commerce – Security policy can identify risks and countermeasures to reduce risks • Key security provisions – Secrecy, integrity, available service • Client threats and solutions – Virus threats, active content threats, cookies • Communication channels’ threats and solutions – Encryption provides secrecy Electronic Commerce, Tenth Edition 107 Summary (cont’d.) • Web Server threats and solutions – Threats from programs, backdoors • Security organizations – Share information about threats, defenses • Computer forensics – “Break into” computers searching for legal use data – Assist in identifying security weaknesses Electronic Commerce, Tenth Edition 108