Research Article Classification of Textual E-Mail Spam
... Clustering of spam messages means automatic grouping of thematically close spam messages. In case of information streams as E-mails, this problem becomes complicated necessity to carry out this process in real-time mode. There are some complications connected with plurality of a choice of algorithms ...
... Clustering of spam messages means automatic grouping of thematically close spam messages. In case of information streams as E-mails, this problem becomes complicated necessity to carry out this process in real-time mode. There are some complications connected with plurality of a choice of algorithms ...
Telit_HE910_A-GPS_Application_Note_r4
... the module, to perform its First Fixing activity without assistance data coming from cellular network. The GPS receiver estimates its position directly from GPS satellites in its line of sight. The S-GPS is sometime slower to compute its First Fix; this phenomenon is evident in very poor signal cond ...
... the module, to perform its First Fixing activity without assistance data coming from cellular network. The GPS receiver estimates its position directly from GPS satellites in its line of sight. The S-GPS is sometime slower to compute its First Fix; this phenomenon is evident in very poor signal cond ...
The Relation between Granger Causality and Directed Information
... This review deals with the analysis of influences that one system, be it physical, economical, biological or social, for example, can exert over another. In several scientific fields, the finding of the influence network between different systems is crucial. As examples, we can think of gene influen ...
... This review deals with the analysis of influences that one system, be it physical, economical, biological or social, for example, can exert over another. In several scientific fields, the finding of the influence network between different systems is crucial. As examples, we can think of gene influen ...
Cyber Security
... Tactics Team was immediately sent to the home of a couple with two sleeping toddlers. The SWAT team handcuffed the husband and wife before deciding it was a prank. Says the article, 'Other law enforcement agencies have seen similar breaches into their 911 systems as part of a trend picked up by comp ...
... Tactics Team was immediately sent to the home of a couple with two sleeping toddlers. The SWAT team handcuffed the husband and wife before deciding it was a prank. Says the article, 'Other law enforcement agencies have seen similar breaches into their 911 systems as part of a trend picked up by comp ...
Near-Field Probe Set User Guide
... desired, subtract 51.52 dB from the performance factor indicated on the graphs in Figure 2-1. Obtaining accurate, repeatable results from EMI testing requires a carefully established and calibrated test setup, usually an open field test site or a shielded room. Final qualification must be performed ...
... desired, subtract 51.52 dB from the performance factor indicated on the graphs in Figure 2-1. Obtaining accurate, repeatable results from EMI testing requires a carefully established and calibrated test setup, usually an open field test site or a shielded room. Final qualification must be performed ...
Biomedical Instrumentation
... is the lower frequency < 1000Hz phenomenon and is due to manufacturing defects • A wide class of electronic devices demonstrate so called flicker effect or wobble (=trembling), its intensity depends on frequency as 1/f, ~1, in the wide band of frequencies; • For example, flicker effect in the elec ...
... is the lower frequency < 1000Hz phenomenon and is due to manufacturing defects • A wide class of electronic devices demonstrate so called flicker effect or wobble (=trembling), its intensity depends on frequency as 1/f, ~1, in the wide band of frequencies; • For example, flicker effect in the elec ...
doc.gold.ac.uk
... – Cause action to occur – E-commerce example • Place items into shopping cart; compute tax and costs ...
... – Cause action to occur – E-commerce example • Place items into shopping cart; compute tax and costs ...
Multiuser MISO Beamforming for Simultaneous
... the other hand, radio signals have been widely used for wireless information transmission. As a result, a unified study on simultaneous wireless information and power transfer (SWIPT) has recently drawn significant attention, which is not only theoretically intricate but also practically valuable fo ...
... the other hand, radio signals have been widely used for wireless information transmission. As a result, a unified study on simultaneous wireless information and power transfer (SWIPT) has recently drawn significant attention, which is not only theoretically intricate but also practically valuable fo ...
Knowledge Engineering - KDD
... concepts, primitive relations, and definitions needed to talk about and understand this problem and its solutions. The following is a sample dialogue between the knowledge engineer and the expert: KE: Suppose you were told that a spill had been detected in White Oak Creek one mile before it enters W ...
... concepts, primitive relations, and definitions needed to talk about and understand this problem and its solutions. The following is a sample dialogue between the knowledge engineer and the expert: KE: Suppose you were told that a spill had been detected in White Oak Creek one mile before it enters W ...
TCA Report Template - Transport Certification Australia
... transport operator will then be given the opportunity to provide any further information that may be of assistance where the assessment report indicated that there is insufficient information available or identified a deficiency in the IVU that could be addressed through more detailed information. ...
... transport operator will then be given the opportunity to provide any further information that may be of assistance where the assessment report indicated that there is insufficient information available or identified a deficiency in the IVU that could be addressed through more detailed information. ...
Note Detection and Multiple Fundamental Frequency Estimation in
... and writing sheet music by hand to preserve a good improvised solo can be tedious and difficult, particularly for someone untrained. Imagine teaching-software that could analyze every second of a student’s practice away from his teacher. It might not only notice his wrong notes, but also notice an ine ...
... and writing sheet music by hand to preserve a good improvised solo can be tedious and difficult, particularly for someone untrained. Imagine teaching-software that could analyze every second of a student’s practice away from his teacher. It might not only notice his wrong notes, but also notice an ine ...
071112 translational research of sleep medicine
... For the fixed polysomnography The size is too large, users must sleep in an unfamiliar environment. This may affect the accuracy of the collected data. For the ambulatory polysomnography The device is still large, and too expensive. Animal study The wires may cause some interference, including elect ...
... For the fixed polysomnography The size is too large, users must sleep in an unfamiliar environment. This may affect the accuracy of the collected data. For the ambulatory polysomnography The device is still large, and too expensive. Animal study The wires may cause some interference, including elect ...
Modeling Others from Observations AAAI Press Papers from the AAAI Workshop
... AAAI maintains compilation copyright for this technical report and retains the right of first refusal to any publication (including electronic distribution) arising from this AAAI event. Please do not make any inquiries or arrangements for hardcopy or electronic publication of all or part of the pap ...
... AAAI maintains compilation copyright for this technical report and retains the right of first refusal to any publication (including electronic distribution) arising from this AAAI event. Please do not make any inquiries or arrangements for hardcopy or electronic publication of all or part of the pap ...
Aurally Informed Performance: Integrating Machine Listening and Auditory Presentation in Robotic Systems
... retains the right of first refusal to any publication (including electronic distribution) arising from this AAAI event. Please do not make any inquiries or arrangements for hardcopy or electronic publication of all or part of the papers contained in these working notes without first exploring the op ...
... retains the right of first refusal to any publication (including electronic distribution) arising from this AAAI event. Please do not make any inquiries or arrangements for hardcopy or electronic publication of all or part of the papers contained in these working notes without first exploring the op ...
Understanding Ford`s F-Series VSS Systems Understanding
... of these questions are fairly common, ranging from the basic system operation to step-by-step diagnostic routines. One of the most common questions asked is, “how does the VSS system work?” To address this, we’re going to start by examining the early 1989-91 Fseries VSS system, then concentrate on t ...
... of these questions are fairly common, ranging from the basic system operation to step-by-step diagnostic routines. One of the most common questions asked is, “how does the VSS system work?” To address this, we’re going to start by examining the early 1989-91 Fseries VSS system, then concentrate on t ...
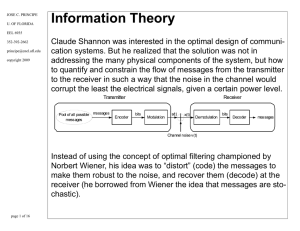
Information Theory
... receiver knows exactly the joint PDF of the received and the transmitted signals. In learning, the system does not know the joint PDF of the input and desired (or the PDF of the input if unsupervised). The problem is exactly how to best estimate these quantities. Shannon left (on purpose) “meaning” ...
... receiver knows exactly the joint PDF of the received and the transmitted signals. In learning, the system does not know the joint PDF of the input and desired (or the PDF of the input if unsupervised). The problem is exactly how to best estimate these quantities. Shannon left (on purpose) “meaning” ...
How to Identify Advanced Persistent, Targeted Malware Threats with Multidimensional Analysis
... Figure 2: Malware Detection with Multiple Analysis Technologies ...
... Figure 2: Malware Detection with Multiple Analysis Technologies ...
Managed Network Anomaly Detection
... Legal Notice: The information transmitted in this document is intended only for the addressee and may contain confidential and/or privileged material. Any interception, review, retransmission, dissemination, or other use of, or taking of any action upon this information by persons or entities other ...
... Legal Notice: The information transmitted in this document is intended only for the addressee and may contain confidential and/or privileged material. Any interception, review, retransmission, dissemination, or other use of, or taking of any action upon this information by persons or entities other ...
Wireless Daylight Sensor
... • The arrow on the daylight sensor points toward the area viewed by the sensor. • Place the daylight sensor so its viewing area is centered on the nearest window at a distance from the window of one to two times the effective window height (H). • The effective window height (H) starts at the window ...
... • The arrow on the daylight sensor points toward the area viewed by the sensor. • Place the daylight sensor so its viewing area is centered on the nearest window at a distance from the window of one to two times the effective window height (H). • The effective window height (H) starts at the window ...
aspects of analysis (from context to specification)
... • The ‘best bits’ of each iteration can be used next time around • Motto: “The more often you do it, the better will be the end product” www.monash.edu.au ...
... • The ‘best bits’ of each iteration can be used next time around • Motto: “The more often you do it, the better will be the end product” www.monash.edu.au ...
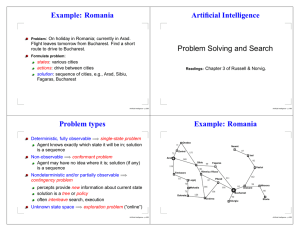
Artificial Intelligence Problem Solving and Search Example
... initial state e.g., “at Arad” successor function S(x) = set of action–state pairs e.g., S(Arad) = {hArad → Zerind, Zerindi, . . .} goal test, can be explicit, e.g., x = “at Bucharest” implicit, e.g., N oDirt(x) path cost (additive) e.g., sum of distances, number of actions executed, etc. Usually giv ...
... initial state e.g., “at Arad” successor function S(x) = set of action–state pairs e.g., S(Arad) = {hArad → Zerind, Zerindi, . . .} goal test, can be explicit, e.g., x = “at Bucharest” implicit, e.g., N oDirt(x) path cost (additive) e.g., sum of distances, number of actions executed, etc. Usually giv ...
Today Iterative improvement algorithms Example: Travelling
... if assigned is complete then return assigned var ← Select-Unassigned-Variable(Variables[csp], assigned, csp) for each value in Order-Domain-Values(var, assigned, csp) do if value is consistent with assigned according to Constraints[csp] then result ← Recursive-Backtracking([var = value |assigned ], ...
... if assigned is complete then return assigned var ← Select-Unassigned-Variable(Variables[csp], assigned, csp) for each value in Order-Domain-Values(var, assigned, csp) do if value is consistent with assigned according to Constraints[csp] then result ← Recursive-Backtracking([var = value |assigned ], ...
Medtronic/Minimed Paradigm® Real-Time
... PART 3: a receiver with a built in Freestyle blood glucose meter. It receives information wirelessly from the sensor/transmitter every ...
... PART 3: a receiver with a built in Freestyle blood glucose meter. It receives information wirelessly from the sensor/transmitter every ...
22-06-0187-03-0000
... • The source signal is generated as evenly distributed real number in (-1,1). We assume that the signal has been down converted to the IF with central frequency 5.381119 MHz (the same as the captured DTV signal). The sampling rate is 21.524476 MHz (the same as the captured DTV signal). The signal an ...
... • The source signal is generated as evenly distributed real number in (-1,1). We assume that the signal has been down converted to the IF with central frequency 5.381119 MHz (the same as the captured DTV signal). The sampling rate is 21.524476 MHz (the same as the captured DTV signal). The signal an ...
Signals intelligence

Signals intelligence (SIGINT) is intelligence-gathering by interception of signals, whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly used in communication (electronic intelligence—abbreviated to ELINT). Signals intelligence is a subset of intelligence collection management.As sensitive information is often encrypted, signals intelligence often involves the use of cryptanalysis to decipher the messages. Traffic analysis—the study of who is signaling whom and in what quantity—is also used to derive information.