Artificial Intelligence Machine Learning Commercial Niches of ML A
... occasional rewards: reinforcement learning no feedback: unsupervised learning ...
... occasional rewards: reinforcement learning no feedback: unsupervised learning ...
RM presentation for county offices
... law or in connection with the transaction of official business. – Preserves evidence of the ...
... law or in connection with the transaction of official business. – Preserves evidence of the ...
s - KDD - Kansas State University
... Given: concept learning problem and examples Learn: disjunctive set of propositional rules Goal: results competitive with those for current decision tree learning ...
... Given: concept learning problem and examples Learn: disjunctive set of propositional rules Goal: results competitive with those for current decision tree learning ...
PowerPoint Slides - Center for Excellence in Education
... Biked everywhere everyday (no car needed) – but had to look out for killer bunnies in the graveyard! ...
... Biked everywhere everyday (no car needed) – but had to look out for killer bunnies in the graveyard! ...
What’s Logic Analyzer? Why Leaptronix LA?
... Signal Capture • Structure of single signal capture ...
... Signal Capture • Structure of single signal capture ...
CEH
... “looking for system administrator to manage Solaris 10 network” This means that the company has Solaris networks on site E.g., www.jobsdb.com ...
... “looking for system administrator to manage Solaris 10 network” This means that the company has Solaris networks on site E.g., www.jobsdb.com ...
The Engineer`s Toolbox
... • Third, apply a linearizing transform. For example, consider two signals being multiplied to make a third: a[n] = b[n] × c[n]. Taking the logarithm of the signals changes the nonlinear process of multiplication into the linear process of addition: log(a[n]) = log(b[n]) + log(c[n]). The fancy name f ...
... • Third, apply a linearizing transform. For example, consider two signals being multiplied to make a third: a[n] = b[n] × c[n]. Taking the logarithm of the signals changes the nonlinear process of multiplication into the linear process of addition: log(a[n]) = log(b[n]) + log(c[n]). The fancy name f ...
CHAPTER : 04 Encoding & Modulation
... Digital to Analog conversion or D-to-A Modulation is the process of changing one of the characteristics of an analog signal based on the information in digital signal. When you transmit data from one computer to another across a public access phone line. The digital data must be modulated on an anal ...
... Digital to Analog conversion or D-to-A Modulation is the process of changing one of the characteristics of an analog signal based on the information in digital signal. When you transmit data from one computer to another across a public access phone line. The digital data must be modulated on an anal ...
Receiver
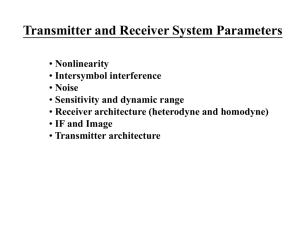
... Unwanted by-product beat signals from the mixing stage do not need any further processing, as they are completely rejected by use of a lowpass filter at the audio output stage. The receiver design has the additional advantage of high selectivity, and is therefore a precision demodulator. The design ...
... Unwanted by-product beat signals from the mixing stage do not need any further processing, as they are completely rejected by use of a lowpass filter at the audio output stage. The receiver design has the additional advantage of high selectivity, and is therefore a precision demodulator. The design ...
Presentation Title
... This presentation, including any supporting materials, is owned by Gartner, Inc. and/or its affiliates and is for the sole use of the intended Gartner audience or other authorized recipients. This presentation may contain information that is confidential, proprietary or otherwise legally protected, ...
... This presentation, including any supporting materials, is owned by Gartner, Inc. and/or its affiliates and is for the sole use of the intended Gartner audience or other authorized recipients. This presentation may contain information that is confidential, proprietary or otherwise legally protected, ...
protecting your radio equipment from emp
... due to effect in the ionosphere, increased noise or phase distortion. The atmospheric effect will dissipate over time, but the damage to your equipment could be permanent. ...
... due to effect in the ionosphere, increased noise or phase distortion. The atmospheric effect will dissipate over time, but the damage to your equipment could be permanent. ...
NRSC Best Practices Tutorial (2014)
... Significantly reduce the potential for a catastrophic failure of critical communications network infrastructure and/or services (e.g., telecommunication, public safety, energy sector, financial, etc.). Materially limit and/or contain the geographic area affected by a communications failure from casc ...
... Significantly reduce the potential for a catastrophic failure of critical communications network infrastructure and/or services (e.g., telecommunication, public safety, energy sector, financial, etc.). Materially limit and/or contain the geographic area affected by a communications failure from casc ...
ATLAS® Intelligence Feed
... Network Security Intelligence, organizations can monitor traffic and activity going to and from the most critical assets, with the context and information to escalate events for further investigation. • Pravail® Security Analytics: ATLAS security intelligence within Pravail Security Analytics enable ...
... Network Security Intelligence, organizations can monitor traffic and activity going to and from the most critical assets, with the context and information to escalate events for further investigation. • Pravail® Security Analytics: ATLAS security intelligence within Pravail Security Analytics enable ...
Problem Set 5 w - Rutgers WINLAB
... think of an time-limited signal s(t) as an unlimited time signal q(t) (that has limited bandwidth) multiplied by a window function w(t) (a unit pulse of a certain duration which is zero everywhere else). So, s(t) = q(t)w(t). Multiplication in time domain implies convolution in frequency domain and s ...
... think of an time-limited signal s(t) as an unlimited time signal q(t) (that has limited bandwidth) multiplied by a window function w(t) (a unit pulse of a certain duration which is zero everywhere else). So, s(t) = q(t)w(t). Multiplication in time domain implies convolution in frequency domain and s ...
sample-tdm
... There is more detailed information on this quite complex problem in the section on aliasing. The important thing is to recognise that aliasing can happen; to recognise when it does and not to be misled by its effects. In the Practical you will be able to see aliasing at work. Interestingly, there ar ...
... There is more detailed information on this quite complex problem in the section on aliasing. The important thing is to recognise that aliasing can happen; to recognise when it does and not to be misled by its effects. In the Practical you will be able to see aliasing at work. Interestingly, there ar ...
Turbidity Meter Progress Report I
... assembly would be limited. If your minimum turbidity is 0 NTU and your maximum is 254 NTU then your resolution is going to be limited to 1 NTU, the solution to this problem is to get a higher bit chip, but that costs more. Another issue with the micro controller is that the initial cost can be rathe ...
... assembly would be limited. If your minimum turbidity is 0 NTU and your maximum is 254 NTU then your resolution is going to be limited to 1 NTU, the solution to this problem is to get a higher bit chip, but that costs more. Another issue with the micro controller is that the initial cost can be rathe ...
The United States Secret Service - Federal Reserve Bank of San
... Irish Reporting & Information Security Service (IRISSCERT) London Metropolitan Police Central e-Crime Unit (PCeU) ...
... Irish Reporting & Information Security Service (IRISSCERT) London Metropolitan Police Central e-Crime Unit (PCeU) ...
Gonzalo Mateos, Ioannis Schizas and Georgios B. Giannakis
... Challenges Data model not completely known Channel fades at the frequencies occupied by ...
... Challenges Data model not completely known Channel fades at the frequencies occupied by ...
Homework 3. - Purdue College of Engineering
... and consider the vector xθ , the result of rotating x counterclockwise by angle θ: xθ (1) = R cos(φ + θ), ...
... and consider the vector xθ , the result of rotating x counterclockwise by angle θ: xθ (1) = R cos(φ + θ), ...
A Decision-making Model to Choose Business Intelligence
... the data from multiple points of view, calculate the aggregations and store them directly in the OLAP databases[1]. The other tools that are provided by some BI venders are Data Mining applications. Data mining, also known as Knowledgee Discovery in Databases (KDD), is the process of automatically s ...
... the data from multiple points of view, calculate the aggregations and store them directly in the OLAP databases[1]. The other tools that are provided by some BI venders are Data Mining applications. Data mining, also known as Knowledgee Discovery in Databases (KDD), is the process of automatically s ...
DRAFT DRAFT DRAFT Terremark Worldwide (NASDAQ:TMRK) is a
... government list. However, none of the Cyveillance IP addresses matched. Based on other factors, the IP address appears to be legitimate traffic from authorized business processes and was provided to QNA for confirmation. Several advanced analysis techniques were used to reduce the massive amount of ...
... government list. However, none of the Cyveillance IP addresses matched. Based on other factors, the IP address appears to be legitimate traffic from authorized business processes and was provided to QNA for confirmation. Several advanced analysis techniques were used to reduce the massive amount of ...
What is a p with a line over it
... Offers discussion forums, directories, technical information libraries, and equipment marketplace for electronics manufacturing industry. (Third edition) by Stuart Russell and Peter Norvig. The leading textbook in Artificial Intelligence. Used in over 1300 universities in over 110 countries. Trapper ...
... Offers discussion forums, directories, technical information libraries, and equipment marketplace for electronics manufacturing industry. (Third edition) by Stuart Russell and Peter Norvig. The leading textbook in Artificial Intelligence. Used in over 1300 universities in over 110 countries. Trapper ...
Signals intelligence

Signals intelligence (SIGINT) is intelligence-gathering by interception of signals, whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly used in communication (electronic intelligence—abbreviated to ELINT). Signals intelligence is a subset of intelligence collection management.As sensitive information is often encrypted, signals intelligence often involves the use of cryptanalysis to decipher the messages. Traffic analysis—the study of who is signaling whom and in what quantity—is also used to derive information.