* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download William Stallings, Cryptography and Network Security 3/e
Multilevel security wikipedia , lookup
Information security wikipedia , lookup
Access control wikipedia , lookup
Trusted Computing wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Network tap wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Proxy server wikipedia , lookup
Wireless security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Mobile security wikipedia , lookup
Computer security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Deep packet inspection wikipedia , lookup
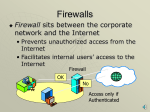
FIREWALLS The function of a strong position is to make the forces holding it practically unassailable —On War, Carl Von Clausewitz On the day that you take up your command, block the frontier passes, destroy the official tallies, and stop the passage of all emissaries —The Art of War, Sun Tzu Introduction • • • • seen evolution of information systems now everyone want to be on the Internet and to interconnect networks has persistent security concerns – can’t easily secure every system in org • need "harm minimisation" • a Firewall usually part of this What is a Firewall? • A firewall is hardware or software (or a combination of hardware and software) that monitors the transmission of packets of digital information that attempt to pass through the perimeter or a network. • A firewall is simply a program or hardware device that filters the information coming through the Internet connection into your private network or computer system. If an incoming packet of information is flagged by the filters, it is not allowed through. What is a Firewall? • a choke point of control and monitoring • interconnects networks with differing trust • imposes restrictions on network services – only authorized traffic is allowed • auditing and controlling access – can implement alarms for abnormal behavior • is itself immune to penetration • provides perimeter defense Perimeter Defense A firewall is said to provide “perimeter security” because it sits on the outer boundary, or perimeter, or a network. The network boundary is the point at which one network connects to another. Firewall Limitations • cannot protect from attacks bypassing it • cannot protect against internal threats – e.g. disgruntled employee • cannot protect against transfer of all virus infected programs or files – because of huge range of O/S & file types Firewalls – Packet Filters Firewalls – Packet Filters A packet filtering router applies a set of rules to each incoming IP packet and then forwards or discards the packet. The router is typically configured to filter packets going in both directions (from and to the internal network). Filtering rules are based on information contained in a network packet: • Source IP address: The IP address of the system that originated the IP packet (e.g., 192.168.1.1) • Destination IP address: The IP address of the system the IP packet is trying to reach (e.g. 192.168.1.2) • Source and destination transport-level address: The transport level (e.g., TCP or UDP) port number, which defines applications such as SNMP or TELNET Firewalls – Packet Filters • IP protocol filed: Defines the transport protocol • Interface: For a router with three or more ports, which interface of the router the packet came for or which interface of the router the packet is destined for • Source and destination transport-level address: The transport level (e.g., TCP or UDP) port number, which defines applications such as SNMP or TELNET Firewalls – Packet Filters: Default Policies Packet filtering is typically set up as a list of rules based on matches to fields in the IP or TCP header. When there is no match to any rule, a default action is taken. • possible default policies –Default = discard: that not expressly permitted is prohibited more conservative, everything is blocked—services must be added on a case-by-case basic, more visible to users who are more likely to see the firewall as a hindrance –Default = forward: that not expressly prohibited is permitted increases ease of use for end users but provides reduced security; the security administrator must, in essence, react to each new security threat as it becomes available Firewalls – Packet Filters Attacks on Packet Filters • IP address spoofing – fake source address to be trusted – add filters on router to block • source routing attacks – attacker sets a route other than default – block source routed packets • tiny fragment attacks – split header info over several tiny packets – either discard or reassemble before check Firewalls – Stateful Packet Filters • examine each IP packet in context – keeps tracks of client-server sessions – checks each packet validly belongs to one • better able to detect bogus packets out of context Firewalls - Application Level Gateway (or Proxy) Firewalls - Application Level Gateway (or Proxy) • use an application specific gateway / proxy • has full access to protocol – user requests service from proxy – proxy validates request as legal – then actions request and returns result to user • tend to be more secure than packet filters – need only scrutinize a few allowable apps – easy to log and audit all incoming traffic Firewalls - Application Level Gateway (or Proxy) • Main Disadvantage – Additional Processing overhead on each connection. • need separate proxies for each service – some services naturally support proxying – others are more problematic – custom services generally not supported Firewalls - Circuit Level Gateway Firewalls - Circuit Level Gateway • relays two TCP connections (one between itself and a TCP user on an inner host and one between itself and a TCP user on an outside host) • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS (a protocol) commonly used for this Bastion Host • highly secure host system that serves as a platform for an application-level or circuit-level gateway. • host hardware platform executes a secure version of it’s operating system, making it a trusted system. • only services that the network administrator considers essential are installed on the bastion host (e.g. Telnet, DNS, FTP, and user authentication) • may require additional authentication • each proxy maintains detailed audit information by logging all traffic, each connection, and the duration of each connection. The audit log is an essential tool for discovering and terminating intruder attacks. Bastion Host • Each proxy module is a very small software package specifically designed for network security. Because of it’s relative simplicity, it is easier to check such modifications for security flaws. • Each proxy is independent of other proxies on the bastion host—a problem with one will not affect the others. • A proxy generally performs no disk access other than to read its initial configuration file. This makes it difficult for an intruder to install Trojan horse sniffers or other dangerous files on the bastion host. • Each proxy runs as a nonprivileged user in a private and secured directory on the bastion host. Firewall Configurations Single-Homed Bastion: Advantages • Has greater security than simply a packet filtering router or an application level gateway alone. – Implements both packet-level and application-level filtering, allowing for considerable flexibility in defining security policy. – An intruder must generally penetrate two separate systems before the security of the internal network is compromised. • Affords flexibility in providing direct Internet access. Firewall Configurations Firewall Configurations Screened Subnet Firewall: Advantages • There are now three levels of defense to thwart intruders. • The outside router advertises only the existence of the screened subnet to the Internet; therefore, the internal network is invisible to the Internet. • Similarly, the inside router advertises only the existence of the screened subnet to the internal network; therefore, the systems on the inside network cannot construct direct routes to the Internet. 11.2 Trusted Systems One way to enhance the ability of a system to defend against intruders and malicious programs is to implement a trusted system technology. Access Control • given system has identified a user • determine what resources they can access • general model is that of access matrix with – subject - active entity (user, process) – object - passive entity (file or resource) – access right – way object can be accessed • can decompose by – columns as access control lists – rows as capability tickets Access Control Matrix Trusted Computer Systems • information security is increasingly important • have varying degrees of sensitivity of information – eg. military info classifications: confidential, secret etc • subjects (people or programs) have varying rights of access to objects (information) • want to consider ways of increasing confidence in systems to enforce these rights • known as multilevel security – subjects have maximum & current security level – objects have a fixed security level classification Bell LaPadula (BLP) Model • • • • one of the most famous security models implemented as mandatory policies on system has two key policies: no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object • no write down (*-property) – a subject can only append/write to an object if the current security level of the subject is dominated by (<=) the classification of the object Reference Monitor Reference Monitor • Properties – Complete mediation: The security rules are enforced on every access, not just for example, when a file is opened. – Isolation: The reference monitor and database are protected form unauthorized modification. – Verifiability: The reference monitor’s correctness must be provable. That is, it must be possible to demonstrate mathematically that the reference monitor enforces the security rules and provides complete mediation and isolation. A system that can provide this kind of verification is referred to as a trusted system. Summary • have considered: – firewalls – types of firewalls – configurations – access control – trusted systems