* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Deployed and Emerging Security Systems for the Internet
Zero-configuration networking wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer network wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Computer security wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Packet switching wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
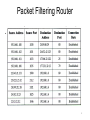
Lecture 20: Firewalls • motivation • ingredients – packet filters – application gateways – bastion hosts and DMZ • example firewall design • using firewalls – virtual private networks • problems with firewalls the pictures are from “Cryptography and Network Security” by William Stallings 1 Why Firewalls • a firewall is a security located between the private network and the Internet regulating traffic between two networks • reasons – eliminate unwanted traffic inside the private network – hard/expensive to enforce end-to-end security • users on the inside do not have to concern with security • a number of “standard” programs are a potential security risk and turned on by default: finger, telnet, rlogin/rsh, X Windows, ICMP – convenient point to combine security with unrelated services like NAT (what’s that?) 2 Packet Filtering Router • router applies a set of rules on the fields of the header of (typically incoming) IP packet and either lets it through or discards it • rules examine the fields and prescribe the action (allow or discard) • fields to use – source/destination IP address – transport layer protocol: port number (which defines the application telnet, ftp, web, etc) – interface (router has many) • can be – stateless – examines each packet individually – stateful – takes communication context into account: some outside packets are allowed to proceed if the inside and outside machine are in active communication • attacks and countermeasures – IP address spoofing – attacker puts IP address of the internal host: drop the packets with internal IP coming from external interface 3 – source routing – origin is internal address: what’s the countermeasure? Stateless Packet Filter Table Example A and C : only mail allowed B: everything blocked D: outside ACKs allowed 4 Packet Filtering Router • blah 5 Application Level Gateway • (also called proxy server) – connections outside are allowed only through proxy – internal host contact proxy, requests connection with the outside, after authenticating the user and if it is configured to provide service for this type of connection (ftp, web, telnet, etc.) proxy relays packets to the outside • adv: easy to monitor traffic and configure security, only allow allow traffic of specified kind • disadv: additional processing time and connection delays 6 Bastion Host and DMZ • bastion host – a secured machine that is allowed external access – must be made made secure: runs secure versions of the OS, inessential services are disabled, authentication before initiating connection, logs auditing and traffic information – implements application-level gateway • DMZ (demilitarized zone) – the portion of the network where (partially screened) external traffic is allowed – usually contains the bastion host 7 Firewall Setup Examples • the combination of packet filtering and application layer gateway makes firewall more effective • multiple layers of defense protect against the compromise of one router/gateway – multiple routers allow NAT-based network hiding 8 Tunneling and VPNs • tunnel – a point-to-point connection over which the communication takes of machines (not located at the endpoints of this connection) takes place • secure tunnel can be used to connect several parts of network of the same organization over (insecure) internet – such configuration is called virtual private network • Alice (in one portion of the network) sends an IP packet to Bob (in another), When the packet reaches Alice’s gateway, the gateway tunnels the packet to Bob’s gateway – IPsec is frequently used for this purpose, how? 9 Problems with Firewalls • firewalls without end-to-end security are not ideal – they do not protect from the attack from the inside (what kind of attack?) – once the security has been breached the network is vulnerable – firewall usually lets email and web traffic through and a number of attacks can be launched through that (think which?) – users are inconvenienced and think of ways of bypassing the security • IP over HTTP (why is that a threat)? 10