* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Systeemanalyse in Ontwerpprojecten
Next-Generation Secure Computing Base wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cryptanalysis wikipedia , lookup
Cryptography wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Unix security wikipedia , lookup
Airport security wikipedia , lookup
Distributed firewall wikipedia , lookup
Wireless security wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Cyberattack wikipedia , lookup
Information security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Mobile security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Social engineering (security) wikipedia , lookup
Computer security wikipedia , lookup
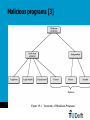
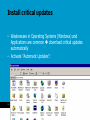
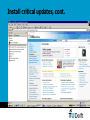
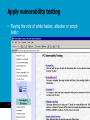
Security and Technology (WM0823TU) Lecture 5-6: Information and ICT Security, threats, cybercrime risks and how to deal with them Jan van den Berg May 5, 2017 1 Faculty Vermelding of Technology, onderdeel organisatie Policy and Management Course overview (still provisional…) Week # Date Subjects Lecturer 35 (1) Tuesday August 31 introduction: the risk society and the goals of the security & technology course JvdB 36 (2) Monday September 6 refresh first lecture; financial risks: dealing with market risk: Assignment 1 JvdB 36 (3) Wednesday September 8 financial risks cont.: dealing with credit risk, operational risk, … JvdB 37 (4) Monday September 13 risk analysis of the infrastructure Internet, an analysis framework: Assignment 2 JvdB 37 (5) Wednesday September 15 information security: an introduction JvdB 38 (6) Monday September 20 information security: threats, cybercrime, and how to deal deal with them: Assignment 3 JvdB 38 (7) Wednesday September 22 a topic from safety science Ben Ale 39 (8) Monday September 27 information quality in public safety networks NB 39 (9) Wednesday September 29 securing the supply chain: some case studies JvdB/YT?? 40 (10) Monday October 4 calculation techniques for risk analysis in river- and coastal engineering PvG 40 (11) Wednesday October 6 reliability of software, human factors, and their lessons for the management of the Maeslant storm surge barrier JvdB 41 (12) Monday October 11 wrap-up, preparation for the final examination JvdB May 5, 2017 2 Motivation: role of ICT in our society • ICT is an enabling technology for data /information provision: delivery of the right data and information at the right place, at the right time, to the right person (e.g., in finance, supply chain security, dealing with crises, public safety, …) information security (the term ‘information safety’ is not in use) • Certain ICT-facilities, including the Internet, can be considered as a critical infrastructure, the security and safety of which should be conserved Internet security • ICT is of importance for individuals and for society as a whole: in economics, information is sometimes even termed the 4th production factor (ex.: news steers stock price dynamics!) • Summarizing, there is a need for information and ICT security management (including the Internet) May 5, 2017 3 Agenda • Background and Conceptualization • Information Security • ICT Security • Intentional threats = Hacking attacks: how does it work? • Other cybercrime threats • Dealing with the threats • Information Security Measures & Management • Internet Security Measures & Management • Assignment of the week • References May 5, 2017 4 Information Security defined • Most common definition: Information Security = Computer Security = ICT Security (this is different from SRMBok book!!) • Information Security (IS) is about the safety & security features/requirements/values (CIAA) • Confidentiality (access to information for authorized entities/identities only) • Integrity (safeguarding accuracy and completeness of information and processing methods) • Availability (ensuring access to data and information when required) • Accountability (ensuring that each action is linked unambiguously to its initiator) (accountable = verantwoordelijk) • Note: this a very technical perspective: content/meaning of information are not considered! issues like correctness of source data, their effectiveness, human privacy, etc. are outside the scope of IS. May 5, 2017 5 Information Security defined, SRMBoK Section 7.5: ICT security • • 7.5.5 focuses on ICT security defined in terms of the preservation of CIA (like the BS7799 and its followers) 7.5.6 discusses some basic threats Section 7.6: Information security • • • • 7.6.1 focuses on Information security defined in terms of the preservation of CIA and, in addition, utility or usefulness, authenticity or non-repudation (= accountability), and control or possession 7.6.2 discusses the information lifecycle: 7.6.3 discusses some vulnerabilities 7.6.4 discusses classification of information, also important in non-ICT world May 5, 2017 6 7.6.4 Information Classification • Information should be classified in a certain way such that people are only authorized to access (read, write and execute) certain data, information and programs • Big organizations often apply role-based access control where rights are linked to the different roles people do have: a hard problem to keep it simple (why?) • In governments and military organzations, a hierarchical model like Bell-La Padula model is often applied with strict read and write rules in a hierarchical setting of document flows: ‘no read-up’ and ‘no write down’ are two basic principles (can you explain them?). May 5, 2017 7 7.6.5 Intellectual Property Rights • Intellectual property is a term referring to a number of distinct types of creations of the mind for which property rights are recognised—and the corresponding fields of law. • Under intellectual property law, owners are granted certain exclusive rights to a variety of intangible assets, such as musical, literary, and artistic works; discoveries and inventions; and words, phrases, symbols, and designs. • Common types of intellectual property include copyrights, trademarks, patents, industrial design rights and trade secrets in some jurisdictions. May 5, 2017 8 Information Security: why and how? • Why information security? (as part of Business Continuity) • To prevent/reduce/minimize damage to the ‘business’~minimize expected losses: often hard to quantify! • To be compliant: SOX, Basel II, Tabaksblat,… • Solution: What can we do? • Physical/Logical (20%), and Organizational measures (80%) of preventative, corrective and repressive character at a strategic, tactic and operational level • Implementation of ISM: how to do it in practice? • Using Best Practices like ISO-17799, ITIL, COBIT, SPRINT, … (not available for free: BS7799 is on BB!) which include all above-given types of measures… May 5, 2017 9 Framework of Thinking: repetition • Information Security (IS) is about the four generic safety & security features/requirements/values (CIAA) • Confidentiality (access to information for authorized entities/identities only) • Integrity (safeguarding accuracy and completeness of information and processing methods) • Availability (ensuring access to data and information when required) • Accountability (ensuring that each action is linked unambiguously to its initiator) May 5, 2017 10 Framework of Thinking, cont. • Security Services (SSs) are functions that enhance the security requirements of an information system (i.e., the probability that an IS is in a secure state) • Example SSs are identification, authentication, authorization, (role-based) access control, certification, digitally signing, time stamping, non-repudiation, data hiding, availability enhancement • A threat is a potential violation of information security which, by exploitation of vulnerabilities, may result into security incidents • Intentional actions that could violate IS are often termed attacks • Initiators of attacks are termed attackers, crackers, script-kiddies, white hats, black hats, … see further below May 5, 2017 11 Security requirements and some security services for enabling secure communication May 5, 2017 12 Framework of Thinking, cont. • A security mechanism or control (preventive, detective or corrective) is a measure/method/tool or procedure for implementing a security service • Examples are login software, encryption/decryption tools, segregation of duties, defining a security policy, incident management procedures, identification of risks from a third party, user training, physical entry controls, backing-up of data, clear desk/screen policy, controls against malicious software, user registration, forcing correct use of passwords, intrusion detection, system recovery procedures • Security is only as strong as the weakest link in the chain, so security is a matter of degree: there is no 100% secure system! May 5, 2017 13 Example: implementing access control • Security service Access Control at a computer system, banking system, public transport system, etc. is built up from several other security services 1. Identification using user id (implemented by security mechanisms like a login name, email address, banking or other pass), usually not secrete 2. 3. • Authentication: implemented by security mechanisms like ‘what you know’ (e.g., password), AND/OR ‘what you have’ (e.g., chipcard, banking pass, digipass), AND/OR ‘what you are’ (fingerprint, iris scan, DNA-string), AND/OR ‘where you are’… Authorisation: giving the authenticated user (possibly, in a specific role) access to system services based on a security mechanism like a (possibly role-based) ‘authorization matrix’ Other example will follow below (in section “dealing with the threats”) ICT as infrastructure: from Internet to WWW and Semantic Web • ARPA network: network with basic communication functionality (like TCP/IP) in the ’60ies of previous century • 1991: Tim-Berners Lee at CERN (Geneve) has the idea of connecting information sources using links (defined by URLs); this results into the World Wide Web • Business/government/individuals take up the challenge ebusiness, e-government, social networks, etc. • Development of the browser made Internet accessible to anyone; this includes accessible for hackers • Future: Semantic Web making the WWW a smart Web for data, information and knowledge exchange (http://en.wikipedia.org/wiki/Semantic_Web ) May 5, 2017 15 Agenda • Background and Conceptualization • Information Security • Internet Security • Intentional threats = Hacking Attacks: how does it work? • Other cybercrime • Dealing with the threats • Information Security Measures & Management • Internet Security Measures & Management • Assignment of the week • References May 5, 2017 16 Hackers terminology [2] • White hackers, gurus or wizards: hackers having specialist IT-knowledge to be used legally with best intentions (e.g., information security experts) • Black hats or crackers: hackers with illegal intentions (e.g., distribution of copyrighted software, trying to shut down systems with distributed-denial-of-service (ddos) attacks) • Script kiddies • (often young) people without technical knowledge having bad intentions; • use available cracking software, often just for fun • Grey hats or ethical hackers: illegal activities with best intentions (e.g., penetration in systems and making this public) May 5, 2017 17 Hacking: how does it work? From a technical perspective • Internet software (TCP/IP) uses so-called ports for connection purposes • Actually, more than 65000 port numbers are in use: e.g., email uses port 25, web pages use port 80 (behind ports you often find servers that answer requests from clients like a browser) • Port scanners check (by sending IP-packets) whether certain ports have open access: see e.g. www.insecure.org/nmap/ • Vulnerability scanners look for vulnerabilities like in the software used (old software that has not being patched): see e.g. www.nessus.org • Packet sniffers (or protocol analyzers) look at the content of incoming/outgoing IP-packets: see e.g. www.ethereal.com, e.g. look for passwords May 5, 2017 18 Hacking : how does it work?, cont. • Best known vulnerability is buffer overflow: a short program is placed in an unprotected memory location such that the computer starts to execute this code… • Identification of ‘all known exploits’ (techniques to exploit vulnerabilities) is not difficult: available on the Ethical Hacker Network • Virus and other malicious programs (malware) may exploit these vulnerabilities: there exist many types! • Password guessing software discovers passwords of users May 5, 2017 19 Malicious programs [3] May 5, 2017 20 Malicious programs, cont. • There exist malicious software of many types, often • as part of other software and • distributed via the WWW • A taxonomy of malicious software: • independent replicating bacteria: they just reproduce exponentially taking up all resources • independent worms: once active, they replicate themselves using email, remote login or remote execution software; in addition, they perform a ‘certain action’ • zombies: a zombie is a program that secretly takes over another Internet-attached computer to launch difficult to trace attacks May 5, 2017 21 Dependent malicious software • Dependent software need a host program: • trap doors: gain unauthorized access using a certain input sequence (built-in by programmers: ctrl-alt-del is a good, secure example); • logic bombs: embedded code that ‘explodes’ under special circumstances (a time or date e.g.) • Trojan horses: embedded code in an apparently useful routine • viruses: infect other executables, the corresponding code is embedded (resulting into an identifiable piece of code) • For more details, see [3] May 5, 2017 22 Other technical hacking practices • war driving: looking for non-encrypted WIFI networks using a laptop and a car: see e.g. http://wifiscanner.sourceforge.net/ • social engineering is about misleading people (here by letting them activate certain pieces of software or providing sensitive data including passwords) based on • pretending authority (being responsible computer system manager) or being a friend or colleague • flirting and flattering using personal conversation, spam (see slide 27), phishing and/or pharming (see next slide), … May 5, 2017 23 Phishing and Pharming • Phishing • Ask for confidential data like passwords • Ask for clicking on a hyperlink that imitates a well-known bank or other system’s website where user has to fill in confidential data • Very many phishing attacks do currently occur • Pharming (sophisticated type of phishing) • Even if user types correct name like www.abnamro.nl, user is re-routed without knowing this… May 5, 2017 24 Hacking : having entered, what’s next? • White hackers are done… (they have got their kick from being capable of entering the system) • Black and ethical hackers start collecting valuable information • Script kiddies are often just interested in ‘defacing web sites’… • Professional hackers remove traces and/or create a back door for future use… May 5, 2017 25 Agenda • Background and Conceptualization • Information Security • Internet Security • Intentional threats = Hacking attacks: how does it work? • Other cybercrime threats • Dealing with the threats • Information Security Measures & Management • Assignment of the week • References May 5, 2017 26 Spam • Sending spam is cheap and success rate is not low: +/- 20% of people have at least once bought stuff based on spam email [2] • First spam was already sent in the 70ies… • Collecting email addresses is facilitated by spiders (see, e.g., www.massmailsoftware.com/extractweb ) • Measures against spam (not always very effective…!) • Filtering against blacklist (refuse) and white list (accept) • Bayesian filtering: look for similarities • … • Penalties can be high: up to 20.000 euro in the Netherlands! May 5, 2017 27 DoS attacks, mail bombs and more • 90-ies: Internet would make the world a better place… • March 2000: dotcom bubble bursts (by non-technical threats): NASDAQ collapses from 5048,62 till 1114,11 on October 2002 (did we forget something in the recent history??) • Anyway, the Internet is simply not a safe place: dos (denial-of-service) attacks by • sending many packets: IP-spoofing (other computers are requested to send messages to one single computer, example of distributed dos (ddos) attacks) • destabilization: packets that make computers crashing • true warfare: physical bombs or bullits May 5, 2017 28 Attacking crucial parts of the Internet • Domain Name System: originally 13 root servers (see http://www.root-servers.org/ for those and other important servers; see also http://www.isoc.org/briefings/ ) • October 21 2002: 9 of 13 root servers suffered from a ddos attack!! • Are we approaching ‘zero day’? Some experts do thing so, see e.g. http://www.pewinternet.org/Infographics/The-Future-of-the-Internet-I.aspx • Another ‘single-point-of-failure’: Amsterdam Internet Exchange (AMS_IX), 2nd biggest Internet junction in the world http://nl.wikipedia.org/wiki/Amsterdam_Internet_Exchange May 5, 2017 29 Cybercrime in the Netherlands [2] • August 1985, phone number database of PTT (KPN) is entered by two Dutch hackers: 008-database is protected with the easy-to-guess password ‘008’… • 1989: 1st publication of techno-anarchistic journal ‘Hack-Tic’ • 1992: ‘Hack-Tic’ decides to become an ISP based on telephone lines hired from the ‘enemy’, the PTT (KPN) • 1994: ISP activities of Hack-Tic are bundled in XS4ALL • 1998: KPN Telecom buys XS4ALL, the anarchists have changed their role from hackers to business men… Agenda • Background and Conceptualization • Information Security • Internet Security • Intentional threats = Hacking Attacks: how does it work? • Other Cybercrime • Dealing with the threats • Information Security Measures & Management • Assignment of the week • References May 5, 2017 31 IS Management = set of best practices • No ready-to-use solution is available! • Concerns a set of best practices, e.g., the BS7799 [1] (now an ISO standard with # 17799): “BS 7799-1 was first issued in 1995 to provide a comprehensive set of controls comprising best practices in information security” • BS7799 distinguishes 10 categories: security policy, security organization, asset classification and control, personnel security, physical and environmental security, communications and operations management, access control, systems development and maintenance, business continuity management, compliance May 5, 2017 32 Information security: risk analysis and response • preventive measures relate to • taking away threats (e.g., hackers) • minimization of vulnerabilities (e.g., repairing software errors, use of strong keys when using encryption) • detective measures relate to • discovery of IS incidents (e.g. virus scan, intrusion detection) in order to minimize the impact based on relieving measures (e.g., data saving & system shut down) • corrective measures relate to • return to business-as-usual state (based on repair or use of backup facilities) May 5, 2017 Threat Preventive measures Incident Detective measures Damage Corrective measures Recovery 33 Risk analysis in the business: look at information dependence of the critical processes Basic steps of an information security maturity assessment: Hacking: taking measures • Preventively taking away threats caused by hackers knowing that • • • • hackers act anonymously on the Internet collect their hacking software from the same Internet no worldwide central authorities exist, Internet crime is often part of the ‘organized crime’, … is a hard task and sometimes impossible • Next to preventive, we need many detection and recovery measures • Some things we can do: • secure the systems (e.g., separate internal network from Internet): see below • make their users aware of risks (see also below) • start investigations to understand the problems: bureaus digitale expertise (experts within Dutch police organization) • start forensic research (concerns ‘truth-finding in criminal proceedings’) e.g., by the ‘mining’ of all kinds of data sources (NFI) • involve society: meldpunt computercriminaliteit • deter hackers by imposing high penalties and long imprisonments: wet computercriminaliteit Technical Security Measures (from the BS7799 categories) • Physical security (not elaborated here) • System and Network (S&N) Security • Access control (identification, authentication, authorization) • Development (~ software engineering) and Maintenance (not elaborated here) May 5, 2017 36 System & Network Security • IT Systems' security is part of information security management; it consists of a balanced set of controls based on best practices, e.g., • IT-infrastructure (software and hardware): how to keep the systems up and running, e.g., against earthquakes and DDOSattacks? • Firewalls and Intrusion Detection systems (problem of false positives) • Access control and Authorization • Email and Web Security • Critical updates • Anti-virus software and vulnerability testing • Back-ups and overtaking places May 5, 2017 37 Infrastructure: segmentation • Demilitarized Zones (DMZs), at least one • Situated between 'hostile' outside network (Internet) and internal network: protected by firewalls and monitored • Access to each DMZ should be explicitly authorized • DMZs can be structured in a multi-level hierarchy • first level: publicly accessible services like web server, DNS, mail servers • second level: database services only accessible to application servers from the first level DMZ • Internal network may be protected by a separate firewall May 5, 2017 38 Example architecture May 5, 2017 39 Connections' control • Here done by a firewall having 5 network interfaces • Depending on the security policy implemented using • source and destination of requests • protocol used • firewall should (not) admit specific data traffic • Correct and save firewall configuration is essential • Preferably, firewalls apply Network Address Translation where internal addresses are used in the internal network (see: http://www.vicomsoft.com/knowledge/reference/nat.html ) May 5, 2017 40 Access Control and Authorization • Usually three steps • Identification, e.g., an id or name (sometimes on a card) • Authentication, usually based on (i) what you know (a key word or access code) and/or (ii) what you have ( passport or other (e-)card) and/or (iii) who you are (finger, iris, dna) and/or (iv) where you are (each moment in time), (e.g., you cannot be at one place at the same time nor travel faster then the velocity of light …) • Authorization, e.g., based on role-based access control matrix where you current role defines your current access rights May 5, 2017 41 Dealing with spam • Sending spam is cheap and success rate is not low: +/- 20% of people have at least once bought stuff based on spam email [2] • First spam was already sent in the 70ies… • Collecting email addresses is facilitated by spiders (see, e.g., www.massmailsoftware.com/extractweb ) • Measures against spam (not always very effective…!) • Filtering against blacklist (refuse) and white list (accept) • Bayesian filtering: look for similarities • … • Penalties can be high: up to 20.000 euro in the Netherlands! May 5, 2017 42 Role of Cryptography, some examples • Authorization: cryptography can help to verify correctness of pincode or passwords by applying ‘message digest’: passwords (together with idinformation) are stored in a ‘hashed way’ (so original pincode is nót stored!!); more details are here • Cryptography can also be used to implement confidentiality, integrity, non-repudiation by using • private key cryptography usually in combination with • public key cryptography May 5, 2017 43 Public and Private Key Cryptography • Private key cryptography: two communications parties encrypt and decrypt data using the same, secrete key there is a key distribution problem • applications: ensuring C and I (from CIAA) • Public key cryptography: two communications parties encrypt and decrypt data using two complementary keys, one public key for encryption and one secret key for decryption or digital signing • applications: secret key exchange for applying private key cryptography, digitally signatures need for digital certificates binding public keys uniquely to individuals (signed by trusted third parties) • For more details, see e.g. [3] May 5, 2017 44 Symmetric-key algorithms • In conventional cryptography, one key k is used both for encryption (E) of plaintext P and decryption (D) of ciphertext C: C Ek (P) P Dk (C ) • Examples: old DES algorithm and new AES algorithm 45 Public-key Cryptography: theory • In 1976, (code rebels) Diffie and Hellman proposed the idea of using different keys for encryption and decryption • More formally: C Ek (P) , P Dk ' (C ) where • the private key k' cannot be derived from the public key k • the private key k' cannot be found by a ‘chosen plaintext attack’ • However, they did not offer an implementation! • In 1977, Rivest, Shamir and Adleman (RSA) offered a successful one (see below) 46 Advantages of PK Cryptography • Communication partners not knowing each other (like you and ‘Amazon’) can send secure messages to each other provided • the secrete key is really kept secret by its owner • the public key is unambiguously linked to its owner (can be established based on a chain of trust: remember the way you are unambiguously linked to the person mentioned in your passport!!) Exercise: prove this statement! • Messages can be electronically signed enabling the implementation of non-repudiation (see below) 47 RSA (1) • Rivest, Shamir, and Adleman proposed the first public key algorithm, termed the RSA algorithm: 1. Choose two large primes, p and q (typically > 10^120, sic!) Simple example: p = 3, q = 11 2. Compute n = p x q and z = (p - 1) * (q - 1) Here, n = 33, z = 20 3. Choose a number called d, ‘relatively prime’ to z, i.e., d and z may not have common factors Here, we choose d = 7 48 RSA (2) 4. Find an f such that f x d = 1 mod z, i.e., dividing f x d by z should yield a remainder of 1 Here, solve 7f = 1 mod 20 f =3. 5. Encryption is done by calculating C P f (mod n) To do so, plaintext is 'coded', e.g., a =1, b=2, c=3, d=4, e=5, etc. To encrypt an ‘e’, we calculate 5^3 (mod 33) = 125 (mod 33) = 26 = cipher text C 6. Decryption is done by calculating C d (mod n) P (!) Here: 26^7 (mod 33) =8031810176 (mod 33) = 5 = P, so we recovered the ‘e’!! 49 Install critical updates • Weaknesses in Operating Systems (Windows) and Applications are common download critical updates automatically • Activate "Automatic Updates": May 5, 2017 50 Install critical updates, cont. May 5, 2017 51 Anti-virus/anti-malicious software • Install McAfee/AVG/… software • Let system automatically look for new anti-virus updates: the standard of today May 5, 2017 52 Apply vulnerability testing • Playing the role of white hacker, attacker or scriptkiddy: May 5, 2017 53 Apply vulnerability testing, cont. May 5, 2017 54 Back-ups • The need of making back-ups needs no further explanation • Outsourced Automatic Back-up services are available • Idem: need for 'overtaking places' = back-up systems May 5, 2017 55 Intrusion detection • Network-based and Host-based Intrusion Detection • Two general approaches • statistically anomaly detection: threshold based (using frequency of occurrences) or profile based (compare credit card fraud) • rule-based detection: anomaly = deviation from previous used patterns • Intelligent intrusion detection is still a very hard problem: • need for learning systems • need for decision making based on multi-sensor data to avoid too many false positives May 5, 2017 56 Last but not least: execute awareness programs • All technical measures (may) fail in case users are not aware of the risks and behave accordingly… (do you also lock your computer when leaving the room?) (do you have a clean desk policy?) • Awareness programs concern 40% of the informtion security investment costs Research topics related to Information and Internet Security • Ideally: Integrated Security in a Networked World • Technical topics • managing your private information • biometric authentication • security of mobile applications • security on the Semantic Web • implementing role-based access control • Organizational topics • costs-benefits analysis of security programs • where to save biometric data? • from accountancy to e-accountancy • efficiently estimating the security level needed • governance of Internet: a hot topic of research! (see ECP.nl) May 5, 2017 58 Agenda • Background and Conceptualization • Information Security • Internet Security • Intentional threats = Hacking Attacks: how does it work? • Other Cybercrime • Dealing with the treats • Information Security Measures & Management • Internet Security Measures & Management • Assignment of the week • References May 5, 2017 59 Assignment 3: choose one of the following small group assignments 1. Explain the working of the RSA algorithm by constructing an example: show all calculations by using excel. Also describe a) the strength of this algorithm (which relates to the length used for the keys) and b) the underlying mathematics 2. To implement digital confidentiality, integrity and nonrepudiation, etc. a Public Key Infrastructure (PKI) should be set up based on certificates and Certifying Authorities. Describe the structure and working of a PKI, and analyse critically the chain of trust of examples of PKIs that are in use. Assignment 3, cont. 3. Do a literature review to collect information on how the NLs and/or European community deals with the hacking problem: describe threats, vulnerabilities and all kinds of measures that are taken at national and international level: find your own scope 4. Like above #3.: focus on the work by the police and international security organizations (like the AIVD in the NLs) to track and trace hackers (individuals and members of the organized crime like the maffia) Agenda • Background and Conceptualization • Information Security • Internet Security • Intentional threats = Hacking Attacks: how does it work? • Other Cybercrime • Dealing with the treats • Information Security Measures & Management • Internet Security Measures & Management • Assignment of the week • References May 5, 2017 62 References [1] BS7799: available in BlackBoard under “Course Documents” [2] Arjan Dasselaar, “Handboek Digitale Criminaliteit, over daders, daden en opsporing”, Van Duuren Media, 2005 [3] William Stallings, “Network Security Essentials”, 2nd ed., Prentice Hall, 2003 May 5, 2017 63