Operating Systems - The College of Saint Rose
... Kernel relinquishes control to a user process, but may set a timer to ensure a process does not run beyond its allotted time ...
... Kernel relinquishes control to a user process, but may set a timer to ensure a process does not run beyond its allotted time ...
CS5038: The Electronic Society - Homepages | The University of
... Targets for all of C, I, and A are 0. When the shock hits, C (blue) is way below target. This causes spend (red) to go way above target, and system availability to go way below target; that is, the system’s operations have to be curtailed and money spent to fix the problem; with these actions taken, ...
... Targets for all of C, I, and A are 0. When the shock hits, C (blue) is way below target. This causes spend (red) to go way above target, and system availability to go way below target; that is, the system’s operations have to be curtailed and money spent to fix the problem; with these actions taken, ...
Chapter 9
... security levels negotiated in the SA. The policy also define which traffic is “interesting” and whether or not to negotiate IPSec or just send the information with out modification. Components of a Policy: Tunnel setting ...
... security levels negotiated in the SA. The policy also define which traffic is “interesting” and whether or not to negotiate IPSec or just send the information with out modification. Components of a Policy: Tunnel setting ...
Systems Software
... Multiple User Classify by Task Single Task Multitasking Real-time Systems ...
... Multiple User Classify by Task Single Task Multitasking Real-time Systems ...
Assignment 1 Solution
... 1. In a multiprogramming and time-sharing environment, several users share the system simultaneously. This situation can result in various security problems. a. What are two such problems? b. Can we ensure the same degree of security in a time-shared machine as we have in a dedicated machine? Explai ...
... 1. In a multiprogramming and time-sharing environment, several users share the system simultaneously. This situation can result in various security problems. a. What are two such problems? b. Can we ensure the same degree of security in a time-shared machine as we have in a dedicated machine? Explai ...
CS101 Lecture - Sonoma State University
... • Open = No one owns the rights to making a computer with that operating system installed on the computer. • Closed = Someone dose own the rights to making a computer with that operating system on the computer. ...
... • Open = No one owns the rights to making a computer with that operating system installed on the computer. • Closed = Someone dose own the rights to making a computer with that operating system on the computer. ...
TNS03%20Introduction%20to%20Network%20Security
... For a Trojan horse to spread, you must invite these programs onto your computers. For example, by opening an email attachment or downloading and running a file from the Internet. ...
... For a Trojan horse to spread, you must invite these programs onto your computers. For example, by opening an email attachment or downloading and running a file from the Internet. ...
New work,” by mail order. Once I had decid-
... we see with today’s Internet? Not at all. The real problems sit on people’s desktops, and these involve insecure operating systems and applications. I believe that if it were possible to filter out all dangerous content, there would be a thriving market in doing so today. You have certainly observed ...
... we see with today’s Internet? Not at all. The real problems sit on people’s desktops, and these involve insecure operating systems and applications. I believe that if it were possible to filter out all dangerous content, there would be a thriving market in doing so today. You have certainly observed ...
OUTLINE - Bilkent University
... Windows File Systems • include FAT which is File Allocate Table. • File Allocate Table is a partially -patented file system -developed by Microsoft -for MS-DOS and versions of Microsoft Windows. • a cluster is the unit of disk space allocation for files and directories. • Fragmentation is a alloca ...
... Windows File Systems • include FAT which is File Allocate Table. • File Allocate Table is a partially -patented file system -developed by Microsoft -for MS-DOS and versions of Microsoft Windows. • a cluster is the unit of disk space allocation for files and directories. • Fragmentation is a alloca ...
1-web
... distributed systems. Answer: The client-server model firmly distinguishes the roles of the client and server. Under this model, the client requests services that are provided by the server. The peer-to-peer model doesn’t have such strict roles. In fact, all nodes in the system are considered peers a ...
... distributed systems. Answer: The client-server model firmly distinguishes the roles of the client and server. Under this model, the client requests services that are provided by the server. The peer-to-peer model doesn’t have such strict roles. In fact, all nodes in the system are considered peers a ...
Comprehensive Security Protection for
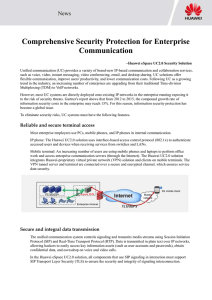
... flexible communication, improve users' productivity, and lower communication costs. Following UC as a growing trend in the industry, an increasing number of enterprises are upgrading from their traditional Time-division Multiplexing (TDM) to VoIP networks. However, most UC systems are directly deplo ...
... flexible communication, improve users' productivity, and lower communication costs. Following UC as a growing trend in the industry, an increasing number of enterprises are upgrading from their traditional Time-division Multiplexing (TDM) to VoIP networks. However, most UC systems are directly deplo ...
Robust. Reliable. Factory Line. Industrial Security redefined protecting industrial networks
... (QoS) functionalities and helps with intrusion detection and antivirus protection. The mGuard portfolio is complemented by a highly scalable device management software. Innominate products are marketed worldwide under the mGuard brand through system integrators and OEM partners. Further information ...
... (QoS) functionalities and helps with intrusion detection and antivirus protection. The mGuard portfolio is complemented by a highly scalable device management software. Innominate products are marketed worldwide under the mGuard brand through system integrators and OEM partners. Further information ...
ppt in chapter 11
... These are simply paths leading into a computer or network. Through simple invasions, or via more elaborate “Trojan horse” code, bad guys can use their implanted inroads into a specific host or even a network whenever they want to—until you detect and stop them. ...
... These are simply paths leading into a computer or network. Through simple invasions, or via more elaborate “Trojan horse” code, bad guys can use their implanted inroads into a specific host or even a network whenever they want to—until you detect and stop them. ...
vaibhav1410945.doc
... It is abbreviated as Win10 or WinX, Microsoft Windows 10 is the latest version of Microsoft Windows that is an upgrade to Windows 8.1 (skipping Windows 9) and was released on July 29, 2015. Windows is a personal computer operating system from Microsoft that, together with some commonly used business ...
... It is abbreviated as Win10 or WinX, Microsoft Windows 10 is the latest version of Microsoft Windows that is an upgrade to Windows 8.1 (skipping Windows 9) and was released on July 29, 2015. Windows is a personal computer operating system from Microsoft that, together with some commonly used business ...
Introduction to UNIX/Linux - gozips.uakron.edu
... the API to perform these functions and also interface with the resource managers ...
... the API to perform these functions and also interface with the resource managers ...
Overview of IT Security at Nottingham
... Corporate Anti-Spyware solution for stopping known and unknown Spyware at the gateway Anti-Crimeware protects your sensitive business data Anti-Phishing prevents identity theft SSL Inspection for “in-box” scanning of HTTPS traffic and enforcement of SSL certificates Choice of leading Anti- ...
... Corporate Anti-Spyware solution for stopping known and unknown Spyware at the gateway Anti-Crimeware protects your sensitive business data Anti-Phishing prevents identity theft SSL Inspection for “in-box” scanning of HTTPS traffic and enforcement of SSL certificates Choice of leading Anti- ...
Lecture 8 - Bhecker.com
... • Public key encryption: Uses two different keys, one private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination ...
... • Public key encryption: Uses two different keys, one private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination ...
Input and Output Optimization in Linux for Appropriate Resource
... create the I/O node, each one sought to optimize the Linux operating system through aggregation. These techniques are building on one another in order to achieve similar goals. Additionally, the last source concerning I/O scheduling built on the idea of the Linux anticipatory scheduler. This demonst ...
... create the I/O node, each one sought to optimize the Linux operating system through aggregation. These techniques are building on one another in order to achieve similar goals. Additionally, the last source concerning I/O scheduling built on the idea of the Linux anticipatory scheduler. This demonst ...
Shin Liu 2/26/2015 Chapter 4 Power Point Answers and Questions 1
... program is installed them the window will run a Windows Update so it can read the device or data. ...
... program is installed them the window will run a Windows Update so it can read the device or data. ...
Foundations of Information Security Webcast
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
Foundations of Information Security Webcast - ABA
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
Slide 1
... • Blocks of code contained in the operating system • Coordinate the operating system with software applications – Similar toolbars and menus ...
... • Blocks of code contained in the operating system • Coordinate the operating system with software applications – Similar toolbars and menus ...
Computer Operating Systems (COP 4610)
... Catalog description: An introduction to what makes up a digital computer operating systems, includes developing an understanding of interrupts, interrupt handling, processes, process management, file and device management, and other features of control programs. A team design project is required. ...
... Catalog description: An introduction to what makes up a digital computer operating systems, includes developing an understanding of interrupts, interrupt handling, processes, process management, file and device management, and other features of control programs. A team design project is required. ...