Are Clouds Secure?
... logs logs that may be • Monitor application available – No standard vulnerabilities using your preferred tool ...
... logs logs that may be • Monitor application available – No standard vulnerabilities using your preferred tool ...
This course is an introduction to computer operating systems
... MAC230 Comparative Operating Systems 3 Credits; 4 Hours (3 lecture, 1 lab) ...
... MAC230 Comparative Operating Systems 3 Credits; 4 Hours (3 lecture, 1 lab) ...
Unit I Introduction
... has the basic routines of an OS. • Some OS use the microkernel concept, this have the function to coordinate to the other parts of an OS such as : I/O Devices, Process, Memory and File Systems. • The structure of and OS could be different but in most of the time are very similar because some OS use ...
... has the basic routines of an OS. • Some OS use the microkernel concept, this have the function to coordinate to the other parts of an OS such as : I/O Devices, Process, Memory and File Systems. • The structure of and OS could be different but in most of the time are very similar because some OS use ...
JRA1.4 AAs in eduGAIN
... with existing architectures (to simplify technical adoption of such a solution by all the participants to the federation). ● Leverage the existing federations in building the reciprocal trust, needed to guarantee security. ...
... with existing architectures (to simplify technical adoption of such a solution by all the participants to the federation). ● Leverage the existing federations in building the reciprocal trust, needed to guarantee security. ...
BitLocker - Microsoft
... Businesses can move to a better-managed desktop and parental controls for consumers Make the system work well for standard users Allow standard users to change relevant settings High application compatibility with file/registry virtualization Make it clear when elevation is required ...
... Businesses can move to a better-managed desktop and parental controls for consumers Make the system work well for standard users Allow standard users to change relevant settings High application compatibility with file/registry virtualization Make it clear when elevation is required ...
2.3 Operating System Design and Implementation
... only on Intel X86, emulators of the X86 instruction set allow the operating system to run non-natively slower, with more resource use-on other CPUs, are programs that duplicate the functionality of one system with another system.) The Linux operating system, in contrast, is written mostly in C and i ...
... only on Intel X86, emulators of the X86 instruction set allow the operating system to run non-natively slower, with more resource use-on other CPUs, are programs that duplicate the functionality of one system with another system.) The Linux operating system, in contrast, is written mostly in C and i ...
Processor Folding for Linux
... the music in the iTunes catalog in 60 seconds. Performance like this is only achieved with the careful tuning of both the hardware and software of the computer. IBM’s Power Hypervisor software allows multiple operating systems to run simultaneously on a server. This is difficult because it requires ...
... the music in the iTunes catalog in 60 seconds. Performance like this is only achieved with the careful tuning of both the hardware and software of the computer. IBM’s Power Hypervisor software allows multiple operating systems to run simultaneously on a server. This is difficult because it requires ...
IO Systems - monismith.info
... • This will prevent user processes from disrupting the OS • Protect memory-mapped and I/O memory port locations from user access, too • Kernel must provide a locking mechanism to allow only protected access to these features ...
... • This will prevent user processes from disrupting the OS • Protect memory-mapped and I/O memory port locations from user access, too • Kernel must provide a locking mechanism to allow only protected access to these features ...
Test Bank for Crypto..
... message. Thus, when a message is sent, the receiver can prove that the alleged sender in fact sent the message and when a message is received, the sender can prove that the alleged receiver in fact received the message. 13. Viruses and worms are two examples of _________ attacks. Such attacks can be ...
... message. Thus, when a message is sent, the receiver can prove that the alleged sender in fact sent the message and when a message is received, the sender can prove that the alleged receiver in fact received the message. 13. Viruses and worms are two examples of _________ attacks. Such attacks can be ...
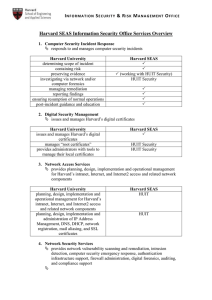
Harvard SEAS Information Security Office Services Overview
... attacks or network Denial of Service attack establishes configuration baseline and monitors infrastructure resources aggregates security event log data from infrastructure resources ...
... attacks or network Denial of Service attack establishes configuration baseline and monitors infrastructure resources aggregates security event log data from infrastructure resources ...
Introduction - Computer Science
... – A service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers ...
... – A service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers ...
Importance of SETA programs
... “Training criteria are established according to trainees’ role(s) within their organizations, and are measured by their on-the-job performance. This emphasis on roles and results, rather than on fixed content, gives the Training Requirements flexibility, adaptability, and longevity… Organizations ...
... “Training criteria are established according to trainees’ role(s) within their organizations, and are measured by their on-the-job performance. This emphasis on roles and results, rather than on fixed content, gives the Training Requirements flexibility, adaptability, and longevity… Organizations ...
NGSCB
... Block access of malicious code Claimed: “no illegitimate access will occurring in protected environment” NGSCB ...
... Block access of malicious code Claimed: “no illegitimate access will occurring in protected environment” NGSCB ...
4 - Operating System Basics.ppt
... • Command line interfaces – Older interface • DOS, Linux, UNIX ...
... • Command line interfaces – Older interface • DOS, Linux, UNIX ...
18_DataCenter_Security_Overview
... Vulnerabilities & Common Attack (cont) Common attacks – After talking about Threats and Vulnerabilities, we will discuss how they are exploited by the most frequent attacks. •Scanning or Probing – this activity precedes an attack to gain access by discovering information about system or network. - ...
... Vulnerabilities & Common Attack (cont) Common attacks – After talking about Threats and Vulnerabilities, we will discuss how they are exploited by the most frequent attacks. •Scanning or Probing – this activity precedes an attack to gain access by discovering information about system or network. - ...
18_DataCenter_Security_Overview
... Vulnerabilities & Common Attack (cont) Common attacks – After talking about Threats and Vulnerabilities, we will discuss how they are exploited by the most frequent attacks. •Scanning or Probing – this activity precedes an attack to gain access by discovering information about system or network. - ...
... Vulnerabilities & Common Attack (cont) Common attacks – After talking about Threats and Vulnerabilities, we will discuss how they are exploited by the most frequent attacks. •Scanning or Probing – this activity precedes an attack to gain access by discovering information about system or network. - ...
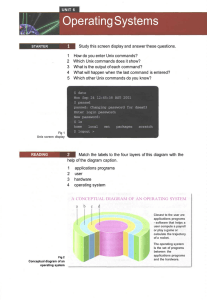
Operating Systems
... Stallman's Free Software Foundation, an organisation of volunteers dedicated to fulfilling Stallman's ideal of making good software that anyone could use without paying. When he'd written a basic kernel, he released the source code to the Linux kernel on the Internet. Source code is important. It's ...
... Stallman's Free Software Foundation, an organisation of volunteers dedicated to fulfilling Stallman's ideal of making good software that anyone could use without paying. When he'd written a basic kernel, he released the source code to the Linux kernel on the Internet. Source code is important. It's ...
IP security - WordPress.com
... Main purpose of Windows is to serve Web server, email server, DNS server, domain/login server etc. So system will be then disable a service which is not necessary. 2) Restrict permissions on files and access to the registry: Restrict permissions like read, write, execute certain files. 3) Remove unn ...
... Main purpose of Windows is to serve Web server, email server, DNS server, domain/login server etc. So system will be then disable a service which is not necessary. 2) Restrict permissions on files and access to the registry: Restrict permissions like read, write, execute certain files. 3) Remove unn ...
CS 494/594 Computer and Network Security - UTK-EECS
... potential to cause loss or harm A vulnerability is a weakness that may be exploited to cause loss or harm A vulnerability can be exploited to perpetrate an attack ...
... potential to cause loss or harm A vulnerability is a weakness that may be exploited to cause loss or harm A vulnerability can be exploited to perpetrate an attack ...
CS 494/594 Computer and Network Security - UTK-EECS
... potential to cause loss or harm A vulnerability is a weakness that may be exploited to cause loss or harm A vulnerability can be exploited to perpetrate an attack ...
... potential to cause loss or harm A vulnerability is a weakness that may be exploited to cause loss or harm A vulnerability can be exploited to perpetrate an attack ...
Computer Security Presentation
... Inc. found that 20% of home computers were infected by a virus or worm, and that various forms of snooping programs such as spyware and adware are on a whopping 80% of systems. Even so, more than two-thirds of home users think they are safe from online threats. [ComputerWorld, OCTOBER 25, 2004] “A z ...
... Inc. found that 20% of home computers were infected by a virus or worm, and that various forms of snooping programs such as spyware and adware are on a whopping 80% of systems. Even so, more than two-thirds of home users think they are safe from online threats. [ComputerWorld, OCTOBER 25, 2004] “A z ...