Operating- System Structures
... software levels. At the hardware level, all data transfers must be inspected to ensure that data have not been corrupted in transit. All data on media must be checked to be sure they have not changed since they were written to the media. At the software level, media must be checked for data consiste ...
... software levels. At the hardware level, all data transfers must be inspected to ensure that data have not been corrupted in transit. All data on media must be checked to be sure they have not changed since they were written to the media. At the software level, media must be checked for data consiste ...
Understanding and Installing Firewalls
... In 1988, an employee at the NASA Ames Research Center in California sent a memo by email to his colleagues [2] that read, "We are currently under attack from an Internet VIRUS! It has hit Berkeley, UC San Diego, Lawrence Livermore, Stanford, and NASA Ames." The Morris Worm spread itself through mult ...
... In 1988, an employee at the NASA Ames Research Center in California sent a memo by email to his colleagues [2] that read, "We are currently under attack from an Internet VIRUS! It has hit Berkeley, UC San Diego, Lawrence Livermore, Stanford, and NASA Ames." The Morris Worm spread itself through mult ...
POST MASTER DEGREE IN SECURITY IN COMPUTER SYSTEMS
... published and students need to choose one topic among this list. Semester Projects are all based on real-case studies of industrial relevance. Industrial partners can be involved. They allowed students to gain hands-on training and gain new skills, by developing prototypes, working with cutting-edge ...
... published and students need to choose one topic among this list. Semester Projects are all based on real-case studies of industrial relevance. Industrial partners can be involved. They allowed students to gain hands-on training and gain new skills, by developing prototypes, working with cutting-edge ...
Training
... • Dietel, H. M., An Introduction to Operating Systems, 2nd Edition, Addison Wesley, 1990. Assessment • Continuous assessment (30%) • Examination (70%) ...
... • Dietel, H. M., An Introduction to Operating Systems, 2nd Edition, Addison Wesley, 1990. Assessment • Continuous assessment (30%) • Examination (70%) ...
Real-Time Operating Systems Hard and Soft Real
... under all conditions – It is typically dedicated to processing real-time applications – E.g., guidance and control applications ...
... under all conditions – It is typically dedicated to processing real-time applications – E.g., guidance and control applications ...
S p
... Proving noninterference • Formalism (Communicating Sequential Formalisms) • Consider any possible system (with arbitrary user applications) • Induction over all possible sequences of moves a system can make (i.e., traces) • At each step, case-by-case analysis of all system calls in the interface. – ...
... Proving noninterference • Formalism (Communicating Sequential Formalisms) • Consider any possible system (with arbitrary user applications) • Induction over all possible sequences of moves a system can make (i.e., traces) • At each step, case-by-case analysis of all system calls in the interface. – ...
PPT
... distinct layers One monolithic kernel that is internally composed of distinct objects Micro-kernel with trusted user level applications that provide major OS functionality like virtual memory, scheduling, file systems, etc. Software engineering questions: Maintainability? Performance? Reliabil ...
... distinct layers One monolithic kernel that is internally composed of distinct objects Micro-kernel with trusted user level applications that provide major OS functionality like virtual memory, scheduling, file systems, etc. Software engineering questions: Maintainability? Performance? Reliabil ...
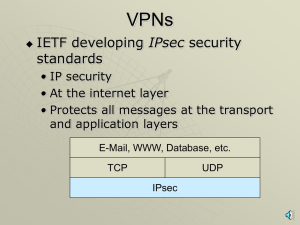
VPNs, PKIs, ISSs, SSLs with narration
... SSL ISS Process • Two sides negotiate security parameters • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
... SSL ISS Process • Two sides negotiate security parameters • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
TrustedOS - Radford University
... subsystems. The human–computer interface often falls outside the security kernel or security restrictions implemented by an operating system. – Code to interact with users is often much more complex and much more dependent on the specific device hardware than code for any other component of the comp ...
... subsystems. The human–computer interface often falls outside the security kernel or security restrictions implemented by an operating system. – Code to interact with users is often much more complex and much more dependent on the specific device hardware than code for any other component of the comp ...
Dan A CSC 345 Term Paper
... run. Viruses and worms can have a variety of effects, including deleting files, corrupting data, accessing private information, and sending spam. A Trojan horse is a program that is disguised as being benign, but allows other users to connect without being detected. The cost of having an infected o ...
... run. Viruses and worms can have a variety of effects, including deleting files, corrupting data, accessing private information, and sending spam. A Trojan horse is a program that is disguised as being benign, but allows other users to connect without being detected. The cost of having an infected o ...
Monolithic, Mikrokernel and Exokernel
... abstractions than the typical Unix primitives. In addition to the new mechanisms, providing an API compatible with Unix or another conventional operating system was a sine qua non; hence implementing Unix on top of the new systems was a natural consequence. Therefore, the microkernel idea became wid ...
... abstractions than the typical Unix primitives. In addition to the new mechanisms, providing an API compatible with Unix or another conventional operating system was a sine qua non; hence implementing Unix on top of the new systems was a natural consequence. Therefore, the microkernel idea became wid ...
PPT
... Monolithic Kernels • All OS services operate in kernel space • Good performance • Disadvantages – Dependencies between system component – Complex & huge (millions(!) of lines of code) – Larger size makes it hard to maintain ...
... Monolithic Kernels • All OS services operate in kernel space • Good performance • Disadvantages – Dependencies between system component – Complex & huge (millions(!) of lines of code) – Larger size makes it hard to maintain ...
PDF
... Monolithic Kernels • All OS services operate in kernel space • Good performance • Disadvantages – Dependencies between system component – Complex & huge (millions(!) of lines of code) – Larger size makes it hard to maintain ...
... Monolithic Kernels • All OS services operate in kernel space • Good performance • Disadvantages – Dependencies between system component – Complex & huge (millions(!) of lines of code) – Larger size makes it hard to maintain ...
Operating Systems
... Face to face Type and Level of Course Elective / 3.Year / Fall Semester Lecturers Name(s) Contacts Lecture Hours Office Hours Course Coordinator Asst.Prof.Dr. Mutlu AVCI [email protected] Course Objective The objective of this course is to introduce students the modern operating systems, their structu ...
... Face to face Type and Level of Course Elective / 3.Year / Fall Semester Lecturers Name(s) Contacts Lecture Hours Office Hours Course Coordinator Asst.Prof.Dr. Mutlu AVCI [email protected] Course Objective The objective of this course is to introduce students the modern operating systems, their structu ...
Intrusion Prevention Systems
... • Keep up with the reading – Midterm on March 2nd • Computer Networks Basics: OSI stack, subnets, Basic protocols: ARP, ICMP, NAT, DHCP, DNS, TCP/IP • Penetration testing: recon, scanning, exploits (ch. 1-4 of book: ”The basics of Hacking and Penetration Testing”) • IDS/IPS • Firewalls • Network Sec ...
... • Keep up with the reading – Midterm on March 2nd • Computer Networks Basics: OSI stack, subnets, Basic protocols: ARP, ICMP, NAT, DHCP, DNS, TCP/IP • Penetration testing: recon, scanning, exploits (ch. 1-4 of book: ”The basics of Hacking and Penetration Testing”) • IDS/IPS • Firewalls • Network Sec ...
Intro to Linux Slides - Raspberry PI Summer Camp at IPFW
... Internet services, the amount of Internet software is endless. Like UNIX, Linux can be just as well used and administered from a remote location, using one of several solutions for remote execution of programs. We briefly touched the subject of security. Linux is an ideal firewall system, light an ...
... Internet services, the amount of Internet software is endless. Like UNIX, Linux can be just as well used and administered from a remote location, using one of several solutions for remote execution of programs. We briefly touched the subject of security. Linux is an ideal firewall system, light an ...
Leaders` Forum, March 16, 2006 - University of Western Ontario
... – Implements and supports the ‘many layers’ of protection – Monitors network activity for anomalies and deals with problems – Responds to security incidents or calls for help – Makes new tools available to campus • ITS Computer Wellness Clinics – Laptops and computers may be brought to the clinic to ...
... – Implements and supports the ‘many layers’ of protection – Monitors network activity for anomalies and deals with problems – Responds to security incidents or calls for help – Makes new tools available to campus • ITS Computer Wellness Clinics – Laptops and computers may be brought to the clinic to ...
Digital Billboard Security Guidelines
... Multi-factor Authentication: The use of two or more disparate methods of determining access privileges. This authentication method typically uses the categories of something you know, something you have, and something you are. Some current implementations include the use of a password with one of th ...
... Multi-factor Authentication: The use of two or more disparate methods of determining access privileges. This authentication method typically uses the categories of something you know, something you have, and something you are. Some current implementations include the use of a password with one of th ...
Module F - Columbus State University
... Modules (TPM) chips, a hardware-based security scheme that stores cryptographic keys, passwords, and digital certificates on the motherboard. A driver has been introduced to support the embedding of security measures in hardware, including TPM devices from National Semiconductor and Atmel. Also, enh ...
... Modules (TPM) chips, a hardware-based security scheme that stores cryptographic keys, passwords, and digital certificates on the motherboard. A driver has been introduced to support the embedding of security measures in hardware, including TPM devices from National Semiconductor and Atmel. Also, enh ...
Resume - OPResume.com
... Provided troubleshooting via telephone and in-person to 1550 internal and external customers, including the installation and configuration of software, password resets and first-line diagnosis/troubleshooting for computer hardware and software problems. Implemented an organization’s computer informa ...
... Provided troubleshooting via telephone and in-person to 1550 internal and external customers, including the installation and configuration of software, password resets and first-line diagnosis/troubleshooting for computer hardware and software problems. Implemented an organization’s computer informa ...
- Mitra.ac.in
... • 1- THE KERNEL : it is s in charge for maintaining all the vital abstractions of the operating system . • The linux kernel forms the central part of linux operating system. It provides all the functionality compulsory to run processes, and it also provides "system services" • 2- THE SYSTEM LIBRARIE ...
... • 1- THE KERNEL : it is s in charge for maintaining all the vital abstractions of the operating system . • The linux kernel forms the central part of linux operating system. It provides all the functionality compulsory to run processes, and it also provides "system services" • 2- THE SYSTEM LIBRARIE ...
Operating Systems Security
... TCB Requirements Quiz An attack that exploits a vulnerability in an operating system turns off the check that is performed before access to a protected resource is granted. ...
... TCB Requirements Quiz An attack that exploits a vulnerability in an operating system turns off the check that is performed before access to a protected resource is granted. ...
Chapter 1 Basic Concepts of Operating Systems
... System Software • The system software is the set of programs that control the activities and functions of the various hardware components, programming tools and abstractions, and other utilities to monitor the state of the computer system. • The system software forms an environment for the programm ...
... System Software • The system software is the set of programs that control the activities and functions of the various hardware components, programming tools and abstractions, and other utilities to monitor the state of the computer system. • The system software forms an environment for the programm ...