pdf
... • Soft real-time • OS provides prioritization, on a best-effort basis • No deadline guarantees, but bounded delays • Examples: most electronic appliances ...
... • Soft real-time • OS provides prioritization, on a best-effort basis • No deadline guarantees, but bounded delays • Examples: most electronic appliances ...
Lecture12
... the Clark-Wilson model is a Constrained Data Item (CDI). An Integrity Verification Procedure (IVP) ensures that all CDIs in the system are valid at a certain state. Transactions that enforce the integrity policy are represented by Transformation Procedures (TPs). A TP takes as input a CDI or Unconst ...
... the Clark-Wilson model is a Constrained Data Item (CDI). An Integrity Verification Procedure (IVP) ensures that all CDIs in the system are valid at a certain state. Transactions that enforce the integrity policy are represented by Transformation Procedures (TPs). A TP takes as input a CDI or Unconst ...
2. Operating System Case Study: Linux
... single-user single-process system Apple MAC is better, but expensive UNIX is much better,, but much much expensive. p Onlyy for minicomputer for commercial applications People was looking for a UNIX based system, which i cheaper is h and d can run on PC Both DOS, MAC and UNIX are proprietary, i.e., ...
... single-user single-process system Apple MAC is better, but expensive UNIX is much better,, but much much expensive. p Onlyy for minicomputer for commercial applications People was looking for a UNIX based system, which i cheaper is h and d can run on PC Both DOS, MAC and UNIX are proprietary, i.e., ...
Judul - my documentation
... – The OS that runs on Apple Macintosh computers – Pioneered the easy-to-use GUI – Proprietary OS • System 9 is OS from 1999, but still popular • Mac OS X is based on BSD Unix kernel • Tiger is 2005 release of Mac OS X; features include – Spotlight – a desktop search engine for locating files on loca ...
... – The OS that runs on Apple Macintosh computers – Pioneered the easy-to-use GUI – Proprietary OS • System 9 is OS from 1999, but still popular • Mac OS X is based on BSD Unix kernel • Tiger is 2005 release of Mac OS X; features include – Spotlight – a desktop search engine for locating files on loca ...
Cosc513-11 operating systems LINUX
... logo and know that your hardware can be trusted to perform when they run Red Hat LINUX. ...
... logo and know that your hardware can be trusted to perform when they run Red Hat LINUX. ...
Introduction to IT Security - Virginia Alliance for Secure Computing
... Working Definitions of Security IT Security Principles Three Aspects of Security Types of Security Services Types of Security Threats Goals of Security Types of Security Attacks Model for Network Security Model for Network Access Security ...
... Working Definitions of Security IT Security Principles Three Aspects of Security Types of Security Services Types of Security Threats Goals of Security Types of Security Attacks Model for Network Security Model for Network Access Security ...
networking operating system
... A multi-tasking operating system such as windows 98 allows you to have two or more programs open & displayed on your desktop at a time. ...
... A multi-tasking operating system such as windows 98 allows you to have two or more programs open & displayed on your desktop at a time. ...
Info Tech -
... ■ Application software: programs written to perform a specific function specified by the user such as Word processing or a spreadsheet application. ■ As the user is creating a document, the OS is what allows the key presses on the keyboard to register as alphabet characters, or numbers, or symbols o ...
... ■ Application software: programs written to perform a specific function specified by the user such as Word processing or a spreadsheet application. ■ As the user is creating a document, the OS is what allows the key presses on the keyboard to register as alphabet characters, or numbers, or symbols o ...
Current IT Security Threats
... Best defenses: Web application firewall, Web application security scanner, application source code testing tools, application penetration testing services, and most importantly a formal policy that all important Web applications will be developed using a valid secure development life cycle and only ...
... Best defenses: Web application firewall, Web application security scanner, application source code testing tools, application penetration testing services, and most importantly a formal policy that all important Web applications will be developed using a valid secure development life cycle and only ...
UNIX/Linux Environment
... Brian Kernighan (AWK programming language, many C and UNIX programming books) • Lorinda Cherry (many document processing tools) ...
... Brian Kernighan (AWK programming language, many C and UNIX programming books) • Lorinda Cherry (many document processing tools) ...
William Stallings, Cryptography and Network Security 5/e
... Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication Availability – resource accessible/usable ...
... Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication Availability – resource accessible/usable ...
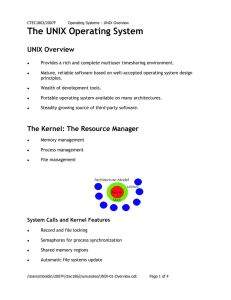
The UNIX Operating System - Niagara College Technology
... Mature, reliable software based on well-accepted operating system design principles. ...
... Mature, reliable software based on well-accepted operating system design principles. ...
William Stallings, Cryptography and Network Security 3/e
... • highly secure host system that serves as a platform for an application-level or circuit-level gateway. • host hardware platform executes a secure version of it’s operating system, making it a trusted system. • only services that the network administrator considers essential are installed on the ba ...
... • highly secure host system that serves as a platform for an application-level or circuit-level gateway. • host hardware platform executes a secure version of it’s operating system, making it a trusted system. • only services that the network administrator considers essential are installed on the ba ...
PROTECTING INFORMATION RESOURCES
... • Network administrator defines rules for access • Examine data passing into or out of a private network – Decide whether to allow the transmission based on users’ IDs, the transmission’s origin and destination, and the transmission’s contents ...
... • Network administrator defines rules for access • Examine data passing into or out of a private network – Decide whether to allow the transmission based on users’ IDs, the transmission’s origin and destination, and the transmission’s contents ...
Document
... – the preliminary design of a new operating system based on the concept of agent will be carried out. The classic issues in the design of operating systems, such as processor scheduling, memory management, system resources, communication, protection, security and user interface, will be extended to ...
... – the preliminary design of a new operating system based on the concept of agent will be carried out. The classic issues in the design of operating systems, such as processor scheduling, memory management, system resources, communication, protection, security and user interface, will be extended to ...
Unit I Operating Systems in Distributed Environments
... has the basic routines of an OS. • Some OS use the microkernel concept, this have the function to coordinate to the other parts of an OS such as : I/O Devices, Process, Memory and File Systems. • The structure of and OS could be different but in most of the time are very similar because some OS use ...
... has the basic routines of an OS. • Some OS use the microkernel concept, this have the function to coordinate to the other parts of an OS such as : I/O Devices, Process, Memory and File Systems. • The structure of and OS could be different but in most of the time are very similar because some OS use ...
Two Types of Software: System Software: Operating Systems
... Secondary memory - This is most often some sort of rotating magnetic storage (hard drive) that keeps applications and data available to be used, and serves as virtual RAM under the control of the operating system. ...
... Secondary memory - This is most often some sort of rotating magnetic storage (hard drive) that keeps applications and data available to be used, and serves as virtual RAM under the control of the operating system. ...
Operating Systems 1
... operator as intermediary is that the users have no interaction with their jobs once they are submitted to the operator. New operating systems were developed that allowed a program being executed to carry on a dialogue with the user through remote terminals (interactive processing) – in which the u ...
... operator as intermediary is that the users have no interaction with their jobs once they are submitted to the operator. New operating systems were developed that allowed a program being executed to carry on a dialogue with the user through remote terminals (interactive processing) – in which the u ...
pdf
... • Soft real-time • OS provides prioritization, on a best-effort basis • No deadline guarantees, but bounded delays • Examples: most electronic appliances ...
... • Soft real-time • OS provides prioritization, on a best-effort basis • No deadline guarantees, but bounded delays • Examples: most electronic appliances ...
Embedded Operating Systems Selection Guide
... from a terminal server. Citrix ICA client supports TCP/IP, IPX, SPX, and NETBIOS. Remote Desktop Protocol (RDP) is Microsoft’s terminal services protocol that governs input/output between a Windows terminal client and Windows Terminal Server. Rdesktop is an open source terminal services client capab ...
... from a terminal server. Citrix ICA client supports TCP/IP, IPX, SPX, and NETBIOS. Remote Desktop Protocol (RDP) is Microsoft’s terminal services protocol that governs input/output between a Windows terminal client and Windows Terminal Server. Rdesktop is an open source terminal services client capab ...
FOI Memo 5492 Nr 3
... an approach that is highly congruent with FOI’s, but which is not labelled as comprehensive security per se. Neither of the two categories coincides exactly with FOI’s approach, which appears to be unique in its particular configuration of integrated security. It is broad not only conceptually but a ...
... an approach that is highly congruent with FOI’s, but which is not labelled as comprehensive security per se. Neither of the two categories coincides exactly with FOI’s approach, which appears to be unique in its particular configuration of integrated security. It is broad not only conceptually but a ...
Operating Systems
... that the user was accessing before last power off. For some complicated environment, the operating system even checks out all the network connections and logging in the internet accounts that the user was logging on before last power off. Once everything is ready, the operating system will be in an i ...
... that the user was accessing before last power off. For some complicated environment, the operating system even checks out all the network connections and logging in the internet accounts that the user was logging on before last power off. Once everything is ready, the operating system will be in an i ...