Linux+ Guide to Linux Certification
... Has the ability to manage thousands of tasks at the same time Allows multiple users to access the system simultaneously ◦ Multiuser and multitasking OS ...
... Has the ability to manage thousands of tasks at the same time Allows multiple users to access the system simultaneously ◦ Multiuser and multitasking OS ...
ch 5 - sm.luth.se
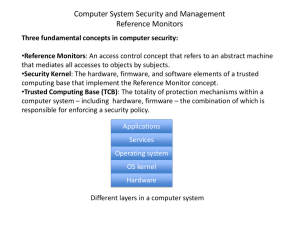
... Three fundamental concepts in computer security: •Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses to objects by subjects. •Security Kernel: The hardware, firmware, and software elements of a trusted computing base that implement the Referen ...
... Three fundamental concepts in computer security: •Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses to objects by subjects. •Security Kernel: The hardware, firmware, and software elements of a trusted computing base that implement the Referen ...
Lecture 3.1 - Host
... core, computer security is most effective when practiced in layers. If an attack is able to penetrate one layer, other layers may still be able to defend the assets. In recent lectures we have explored layers of defense based in cryptography. In this lecture we begin another layer. host-level securi ...
... core, computer security is most effective when practiced in layers. If an attack is able to penetrate one layer, other layers may still be able to defend the assets. In recent lectures we have explored layers of defense based in cryptography. In this lecture we begin another layer. host-level securi ...
cisco.camre.ac.uk
... While no one would wish to live in a society with a ‘Big Brother ‘figure watching every move, it is natural for people to desire the assurance that the working environment and all systems are safe. ...
... While no one would wish to live in a society with a ‘Big Brother ‘figure watching every move, it is natural for people to desire the assurance that the working environment and all systems are safe. ...
Open Source Software
... • More diversity and less coherence • Lack of formal support from a vendor • Modifiable ...
... • More diversity and less coherence • Lack of formal support from a vendor • Modifiable ...
Operating System Research Worksheet
... 7. Many people now are using mobile devices. List 3 popular mobile operating systems. Create a chart to compare desktop OS’s to mobile OS’s. ...
... 7. Many people now are using mobile devices. List 3 popular mobile operating systems. Create a chart to compare desktop OS’s to mobile OS’s. ...
Lecture_01
... 1991, first Linux kernel written in C by Linus Torvalds, University of Helsinki, Finland. First message about it posted on August 25, first release in September. It was developed with the contribution of many programmers around the world. It is functionally similar to Unix (a clone). ...
... 1991, first Linux kernel written in C by Linus Torvalds, University of Helsinki, Finland. First message about it posted on August 25, first release in September. It was developed with the contribution of many programmers around the world. It is functionally similar to Unix (a clone). ...
Answers to Even-numbered Exercises
... The Free Software Foundation (www.fsf.org) is the principal organizational sponsor of the GNU Project. GNU developed many of the tools, including the C compiler, that are part of the Linux operating system. Linux is the name of the operating system kernel developed by Linus Torvalds, which has since ...
... The Free Software Foundation (www.fsf.org) is the principal organizational sponsor of the GNU Project. GNU developed many of the tools, including the C compiler, that are part of the Linux operating system. Linux is the name of the operating system kernel developed by Linus Torvalds, which has since ...
KernelSec: An Authorization Model in the Operating System Kernel
... Hence there is a need for sound operating system based authorizations that can secure the system in the face of these challenges. ...
... Hence there is a need for sound operating system based authorizations that can secure the system in the face of these challenges. ...
Ch 5 Quick Quiz
... T F 3. The most recent version of Windows is Windows XP. T F 4. File management programs can be used to copy files from one storage medium to another. T F 5. Antivirus programs make files smaller so that they can be transmitted faster via the Internet. ...
... T F 3. The most recent version of Windows is Windows XP. T F 4. File management programs can be used to copy files from one storage medium to another. T F 5. Antivirus programs make files smaller so that they can be transmitted faster via the Internet. ...
Enter Title in Docm Properties
... Your initial responsibilities will be the development of modules for the Tofino Security Appliance. This includes system design, code development, documentation, unit-tests, code-reviews, and bug-fixes. Depending on your skill level, this will evolve into leading a team to develop new product module ...
... Your initial responsibilities will be the development of modules for the Tofino Security Appliance. This includes system design, code development, documentation, unit-tests, code-reviews, and bug-fixes. Depending on your skill level, this will evolve into leading a team to develop new product module ...
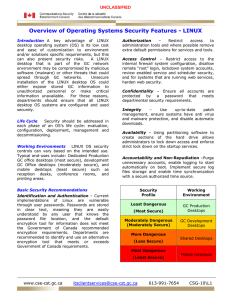
Overview of Operating Systems Security Features
... desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information ...
... desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information ...
• Overview of Cyber Security & need of cyber security • Introduction
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...